Blog
Read our blog to get expert insights into the most pressing issues in mobile security including the latest threats and how to counter them.
Filter by:
-
May 21, 2025 · 5 min read
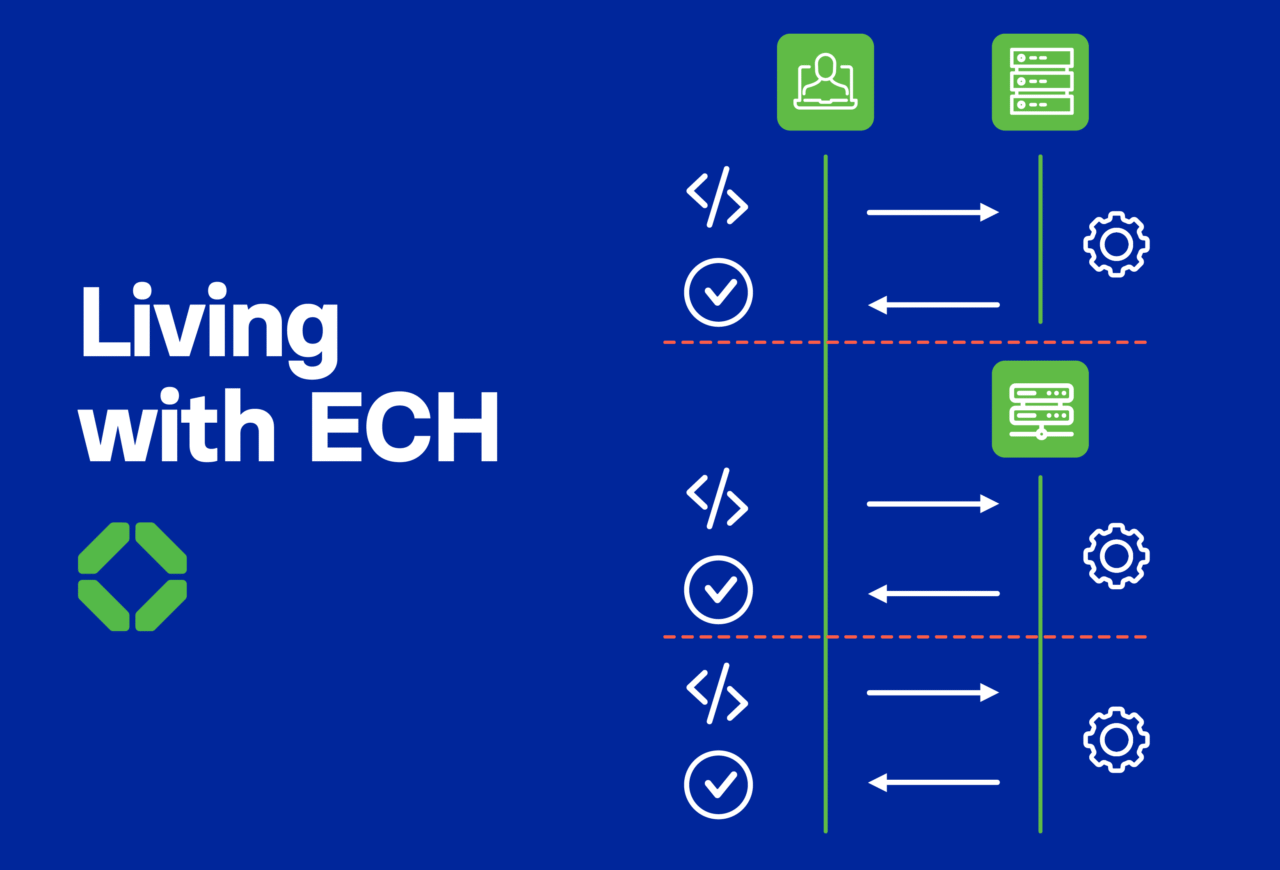
Corrata Report Examines Impact of New Privacy Protocol
Encrypted Client Hello faces barriers to adoption but malicious actors are already taking advantage of the anonymity the protocol provides,...Read more -

May 19, 2025 · 5 min read
TLS – Trust the Lock, Not the Road.
Transport Layer Security (TLS) is the backbone of secure communication on the modern Internet. Over the years, TLS has evolved...Read more -

Feb 27, 2025 · 4 min read
No Filter – Part Two
Spear phishing attacks take advantage of gaps is network, application and browser protetctions Successfully blocking malicious links is the fundamental...Read more -
Jan 21, 2025 · 4 min read
TikTok alternative, RedNote, leaking user data
TikTok alternative, Xiaohonghsu, transmitting user data in plaintext. The news that Donald Trump has intervened to keep TikTok accessible for...Read more -

Oct 10, 2024 · 6 min read
No Filter – Part One
Spear phishing exposes the ‘mobile gap’ in enterprise defenses. Spear phishing is one of the most effective, widely deployed, and...Read more -

Aug 8, 2024 · 4 min read
Stealing secrets – the menace of mobile RAT’s
Smartphones infected with Remote Access Trojans are a critical risk for enterprise security Remote Access Trojans (RATs) have plagued Android...Read more -

Jul 22, 2024 · 5 min read
MFA Bypass – Stealing Cookies
How Adversary-in-the-Middle attacks undermine multi-factor authentication According to Verizon’s authoritative Data Breach Investigation Report, 90% of data breaches start by...Read more -

Jul 12, 2024 · 6 min read
Pegasus, Predator, Hermit Spyware – NSO and its clones
Rise in known exploits point to the proliferation of sophisticated cyber-surveillance tools targeting iOS and Android devices. The recent revelation...Read more -

Mar 27, 2024 · 5 min read
Uncovering a sophisticated QR code phishing attack
A Case Study on Enhanced Security Measures In a recent cybersecurity incident a sophisticated phishing attack was unveiled, employing QR...Read more -

Feb 21, 2024 · 5 min read
Is it Safe ?
When devices hide their identity, how can we tell if they are safe? Many of us, especially those of a...Read more -

Jan 29, 2024 · 4 min read
QR Codes – Sidestepping cyberdefenses
Scan with Caution In the digital age, our defences against phishing have traditionally focused on the familiar: URL scanning, email...Read more -