Threat Detection and Response for Mobile
See every mobile threat. Stop it instantly. Protect users without slowing them down. EDR for mobile, deployed in 24 hours or less – with no friction and no compromise.
We keep global companies safe
The most advanced protection possible
Corrata continues to advance the current state of the art, building on our lead in device traffic inspection with features such as dynamic malware detection, device quarantine and identity gate.
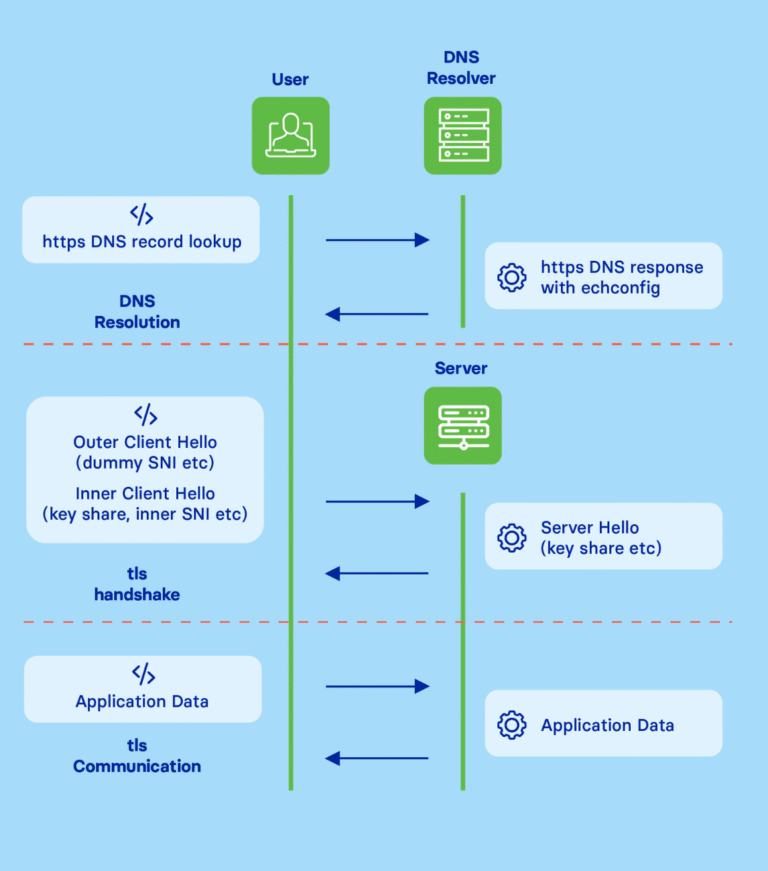
Research Report
Living with ECH
Read Corrata's first-of-its-kind report on the prospects for widespread adoption of Encrypted Client Hello and assessing its impact on enterprise information security.
Learn more
whitepapers
Guide to Mobile Phishing
85% of phishing attacks on mobile take place outside email on channels such as SMS, WhatsApp and Facebook Messenger. To learn how to combat this threat download our updated guide
Learn howWe’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management
News & Insights
Safe & Secure
Read the latest news on threat detection and response for mobile from the experts.
Explore the latest in endpoint threat detection and response for mobile by taking a look through our most recent blogs and threat news.