QR Codes – Sidestepping cyberdefenses

Scan with Caution
In the digital age, our defences against phishing have traditionally focused on the familiar: URL scanning, email spam filters, visually spotting suspicious URL’s. However, threat actors shift their strategies, continually finding new ways to exploit our trust and reliance on technology. The latest ruse in their arsenal? QR code phishing – a devious tactic that takes advantage of a common gap in phishing protection – the mobile device.
The Unseen Threat: QR Code Phishing
A recent incident brought to light a particularly sophisticated phishing threat, cloaked behind the seemingly innocuous facade of a QR code. This malicious campaign began with an email-delivered document purporting to be an unpaid invoice. To access supposedly redacted information, users were prompted to scan a QR code.
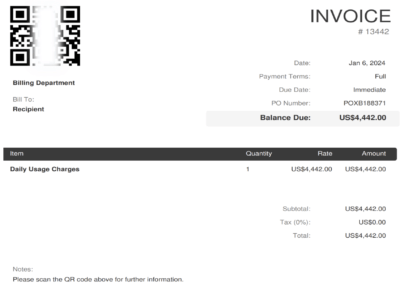
Unlike URL’s, QR Codes are often given a ‘free pass’ by traditional phishing protection systems – those not designed to scan a QR code’s embedded content for threats. This oversight, combined with the lack of a visible URL, means users may not question the legitimacy of the QR code, making the scam more difficult to detect at first glance.
Unfolding the Scam
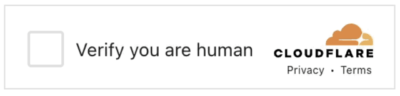
Those who scanned the QR code were redirected to a CloudFlare verification page – a common tactic used by threat actors to thwart both dynamic and static analysis by security systems. This step requires human interaction, bolstering the chances of the phishing site remaining under the radar of automated security defences.
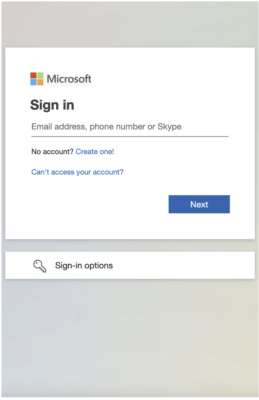
Upon navigating the CloudFlare hurdle, users encountered a fake Microsoft login page, asking them to enter their credentials – a classic phishing move designed to steal sensitive information.
The Takeaway
This incident is a stark reminder of the continuous need for vigilance and the importance of extending security protections to all endpoints. Attackers, increasingly exploiting the often lacklustre protection on mobile, spotting a gap they can exploit.
QR codes, offering convenience and efficiency, have often become a double-edged sword, providing cybercriminals with new opportunities to launch their attacks.
Corrata’s security solution immediately identified the threat posed by the newly registered domain. Our Zero Day Protection swiftly blocked the suspicious domain and alerted the administrators. Upon further analysis, the domain was reclassified as a phishing site.
Stay ahead of Cybercriminals
Corrata’s Mobile Security solution continues to monitor and defend against the ever-changing tactics of cybercriminals. By understanding the methods used by attackers and implementing advanced security measures, we can stay one step ahead.




