Technical details
Deployment and integration
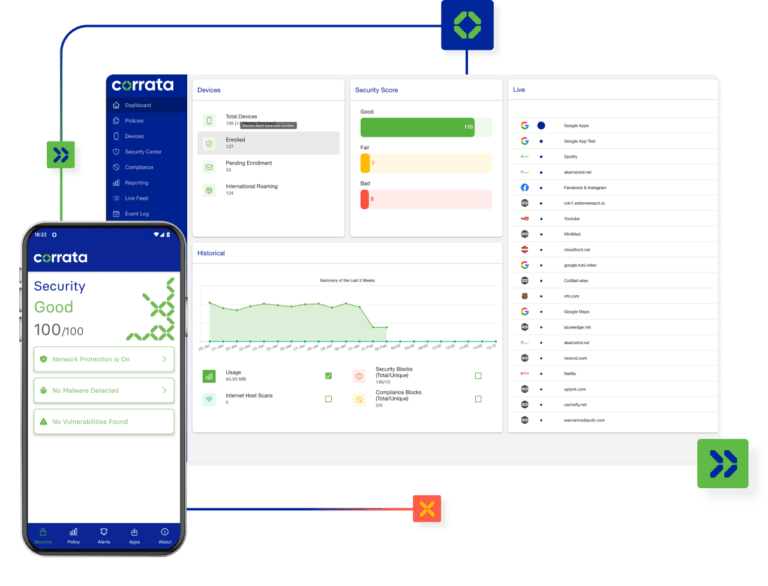
No endpoint security solution is easier to deploy and manage. Choosing Corrata means dramatically reducing risk with minimal investment of time or money.
Easy to deploy, simple to manage
Deploying Corrata is as simple as installing an app. Ongoing management is low touch, low effort.
1
Ease of deployment
Corrata offers a comprehensive range of deployment options including zero-touch for both managed and unmanaged devices. Robust and battle hardened integration with all the leading mobile device management (MDM) platforms including Microsoft Intune and VMWare’s Workspace ONE simplifies deployment. Manual enrollment via email or sms is also supported for BYOD devices or for organizations who don’t use MDM.
2
Integrating with your security stack
Corrata is committed to helping you leverage your existing IT investments. As well as integrating with MDM, Corrata also integrates with a range of other critical systems. We support identity providers including Microsoft, Google and Okta. Corrata also integrates with EDR and XDR solutions such as Microsoft Defender for Endpoint, acting as the specialist mobile component of a best of breed endpoint security stack.
3
Ease of management
Corrata is designed to protect not just notify. Threats are eliminated automatically and remediation actions implemented dynamically. When malware is discovered, users are assisted in removing the offending application. Automatic quarantining of at-risk devices encourages users to take corrective action while reducing the organization’s risk profile. All of this adds up to a solution which protects without absorbing scarce resources.
-
The integration of Corrata with Microsoft Defender for Endpoint will help provide enterprises with comprehensive security operations and visibility across not just their Windows devices but also those running other platforms like iOS and Android
Ryan McGee, Director of Microsoft Security Marketing
Key features
Competitor comparison
Best in class leverage agile frameworks to provide a robust synopsis.
Features
DNS Filtering
Anti-Virus
IP and Port blocking
Encrypted DNS filtering
AitM protection
Quarantining and Access Control
Vulnerability management
Leading competitors
Leading competitors do not block all mobile threats.
true
true
false
false
false
false
false
Corrata
Corrata is the only protection that defends against every threat.
true
true
true
true
true
true
true
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Anti-malware
Device Trust
AiTM Protection
Vulnerability management
Web filtering

case study
Learn how we helped Natwest provide unrivalled security for their iOS and Android phones and tablets
Natwest subsidiary Ulster Bank uses Corrata to secure mobile devices for their employees and retail branches.
Learn how





