Use Case
Mobile
Phishing
Protection
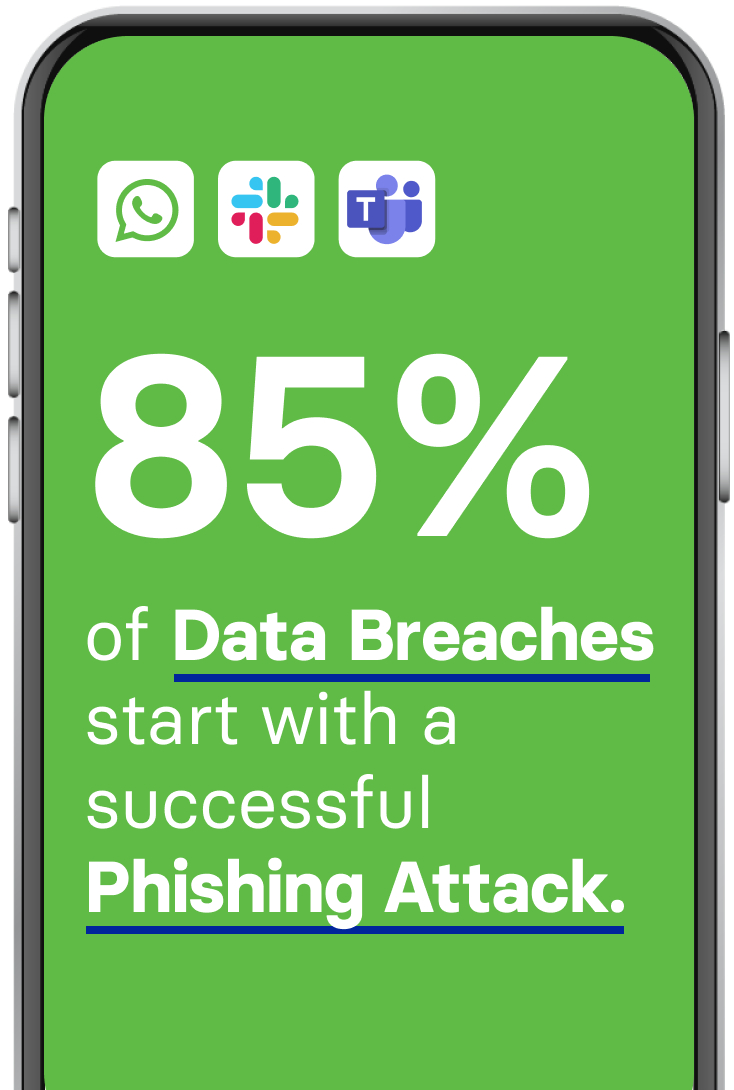
85% of data breaches start with
a successful phishing attack. On mobile SMS phishing is the most common threat but increasingly attackers leverage QR codes, WhatsApp messages and other channels to steal credentials and bypass MFA
Because SMS phishing messages are delivered directly by your mobile operator they bypass your organisation’s defenses - and without Corrata you are completely unprotected.
And it's not just text messages: WhatsApp, Slack, Microsoft Teams and QR codes are among the communications channels cybercriminals seek to exploit.

How Corrata protects against mobile phishing
Corrata protects against phishing by blocking suspicious links detected by our specialized mobile phishing threat intelligence. This includes threats from SMS phishing, WhatsApp meesages, QR codes, LinkedIn posts and more.
Corrata delivers protection which is 3 times more effective than the competition. In addition to blocking domains based on DNS filtering, Corrata also implements a range of enhanced protections, listed below, which go beyond our competitors.
Enhanced mobile phishing protections
-
Protecting against zero-day attacks.
A new phishing domain appears every 60 seconds - Corrata responds in real-time.
Corrata uses a range of techniques to assess the threat level associated with previously unseen domains. Domains which are assessed as risky are quarantined until their reputations can be established.
-
Blocking IP address ranges used by phishing tool kits.
Cybercriminals use toolkits sourced on the dark web - Corrata stops these in their tracks.
90% of phishing attacks are delivered using toolkits. By blocking access to the servers hosting the phishing infrastructure Corrata renders these toolkits ineffective.
-
Blocking website builder platforms with high phishing incidence.
Website builder platforms are used extensively to host phishing domains.
Cyberciminals often avoid detection by using legitimate web platforms to host their phishing sites. A number of website builder platforms are known to host a large number of phishing sites.
Corrata gives customers the ability to block access to any content hosted on the most abused platforms.
-
Detection based on Server Name Indicator as well as Domain names.
Using SNI Corrata never goes dark even when DNS traffic is encrypted.
Privacy concerns are leading more and more end users to ‘hide’ their DNS requests using DNS over https (DOH) or DNS over tls (DOT). To address this Corrata has developed a unique capability to establish server domains using the Server Name Indicator (SNI) protocol.
-
Specialist threat intelligence.
Corrata enhances standard industry phishing block lists with specialist mobile threat intelligence.
Traditional phishing threat intelligence focuses on email. As a result many mobile security solutions lack reliable, timely intelligence on mobile attacks. Corrata augments traditional threat intelligence with threat research focused on smishing and other mobile specific threats.
FAQ’s
85% of phishing on mobile takes place outside email therefore bypassing your email security protections. And employees are notably less vigilant when using mobile due to its convenience and informality. They click on links in SMS messages and scan physical and digital QR codes opening up your organization to risk
Unfortunately the built in consumer grade protections against unsafe content found on mobile devices are completely ineffective against the pace at which new phishing domains are generated. They are particularly useless against the kind of targeted attacks used against organizations.
Corrata doesn’t just rely on industry threat intelligence. As a mobile security specialist we generate our own proprietary intelligence and combine it with machine learning assisted techniques to spot malicious attacks, including mfa bypass attempts, before the competition.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Anti-malware
Device Trust
AiTM Protection
Vulnerability management
Web filtering





