No MAM

Every Employee, Every Application, Any Device?
Digital transformation, often regarded as a hackneyed phrase, fails to fully express the revolution spurred by the combination of cloud computing, ubiquitous connectivity, and advanced mobile devices. Consider that most banking and e-commerce transactions now occur on mobile devices rather than desktops. Tradespeople, taxi drivers, and delivery personnel commonly use mobile apps for payments, receipts, and order recording. Complex tasks like fault troubleshooting in power plants or completing safety training en route to construction sites are now efficiently managed via mobile technologies. Digital technologies are sweeping across every industry, every business process, and all aspects of our daily lives like a flood.
A pivotal factor enabling these changes is the technologies that ensure devices are secure. Device management, alongside endpoint security, plays a critical role. Device management controls configuration, while endpoint security protects against malware and other threats. A managed device, identifiable to an organization through a unique identifier, shares this identifier with the endpoint security product, allowing signals to be passed to conditional access systems.
The Reluctance to Enroll and the Persistence of BYOD
Despite these advances, we are far from a world where every device used by every employee in every organization is enrolled in a device management system like Intune, Workspace ONE, or Ivanti Neurons. The reasons vary. In some cases, it’s just not seen as a priority, especially in smaller organizations with limited resources and less focus on information security. Even in organizations with high security standards and well-developed information security programs, device enrollment is not always the chosen approach. This is often due to employee resistance, especially where personal devices are involved, as culture and privacy concerns may oppose mandatory enrollment. Thus, while device management options range from complete control to managing a partitioned segment of the device, for some organizations, securely supporting BYOD is essential.
Furthermore, users such as non-executive directors, contractors, freelancers, and consultants, who work with multiple organizations, cannot enroll their devices in a single organization’s system, limiting their flexibility.
Enter Mobile Application Management (MAM)
Mobile Application Management (MAM) has been the preferred solution for managing risk in a BYOD context. MAM secures individual applications rather than the entire device. Features like remote data wipe, restricted copy-paste, and setting access requirements (e.g., password complexity) enhance security. MAM is widely supported by applications such as Microsoft Outlook, OneDrive, SharePoint, and the entire Microsoft 365 suite, as well as Google Workspace, including Gmail and Drive. Additionally, various MDM vendors support open standards for app development, particularly useful for bespoke organizational apps.
Why MAM is Broken
However, the burgeoning use of enterprise SaaS applications has exposed MAM’s limitations, especially in medium and large businesses that use dozens to hundreds of SaaS applications. A recent study by Corrata on Okta’s top 50 enterprise SaaS applications revealed that only 12% support MAM. Major applications like Workday, SAP Concur, HubSpot, and Dropbox lack MAM support, leading organizations to either disallow these apps on BYOD devices or overlook the associated risks – neither approach is satisfactory for security, user experience, or productivity.
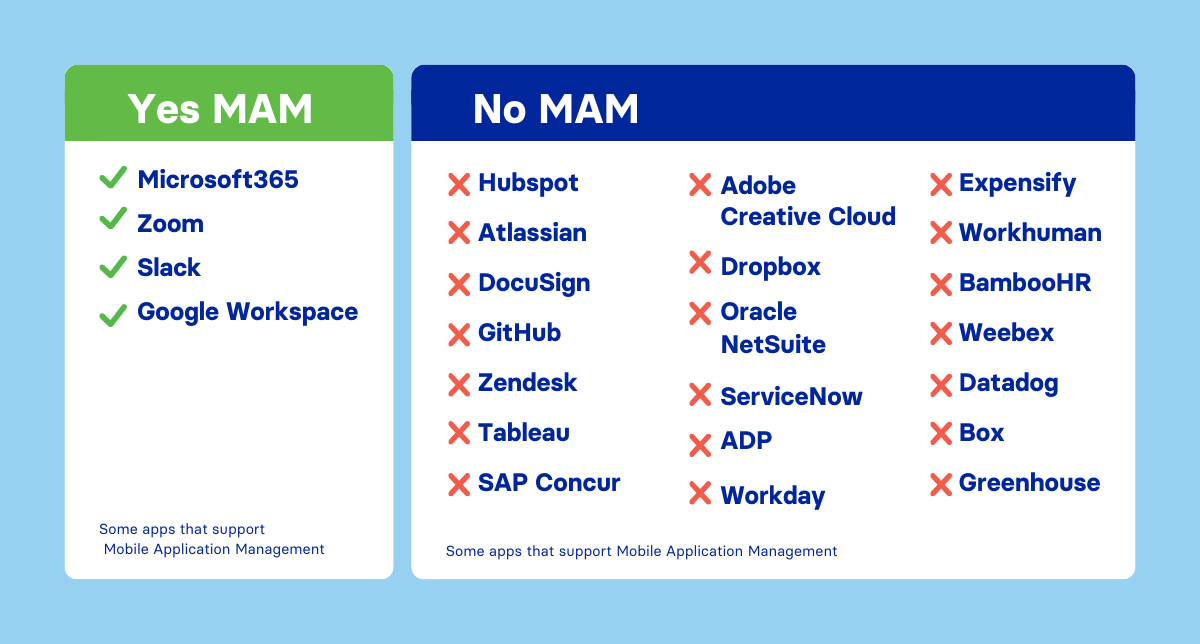
Extend of support for MAM across popular enterprise apps
A significant challenge with BYOD devices is browser access. SaaS applications, typically designed for optimal browser use, lead employees to bypass MAM and access apps via browsers. Some organizations respond by blocking browser access or restricting it to managed devices, but this can be overly restrictive.
Furthermore, MAM assumes the underlying platform’s safety, but checks on the operating system’s integrity or jailbreak status are often superficial. MAM alone doesn’t ensure protection from malware or other threats, a gap that only an endpoint security solution can fill.
Endpoint Security to the Rescue
The good news is that these limitations can be addressed by deploying an endpoint security solution alongside MAM on BYOD devices. Mobile Threat Defense (MTD) products, like Corrata, are tailored for mobile security, offering features such as anti-phishing protection, secure communications, and endpoint detection and response. They perform sophisticated security checks to ascertain device safety and, crucially, can block compromised devices from accessing corporate applications. MTD offers superior protection over MAM and covers all applications, not just those MAM-compatible.
However, MTD’s success hinges on privacy-first solutions. Users need assurance that their personal data, from browsing activity to message content, remains private. Fortunately, solutions offering such privacy are gaining acceptance, especially as employees become more aware of personal mobile security risks. A robust mobile security solution benefits both the company and the employees.
Every Employee, Every Device, Many Applications
While there’s a place for corporately managed devices for privileged users and certain high-security applications, BYOD can provide adequate security for many apps. Leveraging MTD, we can now extend appropriate security levels not just to a few apps but to the majority transforming our workplaces.




