Uncovering a sophisticated QR code phishing attack

A Case Study on Enhanced Security Measures
In a recent cybersecurity incident a sophisticated phishing attack was unveiled, employing QR codes as the primary tool for deception. This case study not only sheds light on the evolving tactics used by cyber attackers but also emphasizes the crucial role of mobile security in thwarting such threats.
An organization fell prey to a phishing scheme orchestrated through emails that appeared to be from a known supplier. Unbeknownst to the organization, the supplier’s email account had been compromised. The phishing emails stood out because they instructed employees to scan a QR code to view details of an alleged outstanding invoice. This QR code, however, redirected the victims to a counterfeit login page designed to harvest Microsoft365 credentials.
Why QR Codes?
The choice of QR codes by the attackers was strategic and based on two key insights:
- Under-the-Radar: Many anti-phishing systems integrated into email services or offered by specialized providers overlook the verification of links embedded in QR codes. This oversight presents a loophole that the attackers exploited, sidestepping traditional email scanning measures.
- Bypassing Desktop Security: By encouraging targets to use their mobile phones to access the malicious site, the attackers effectively bypassed web filters and firewalls typically in place to protect laptops and desktops. This tactic demonstrates a deep understanding of the typical security infrastructure and its vulnerabilities.
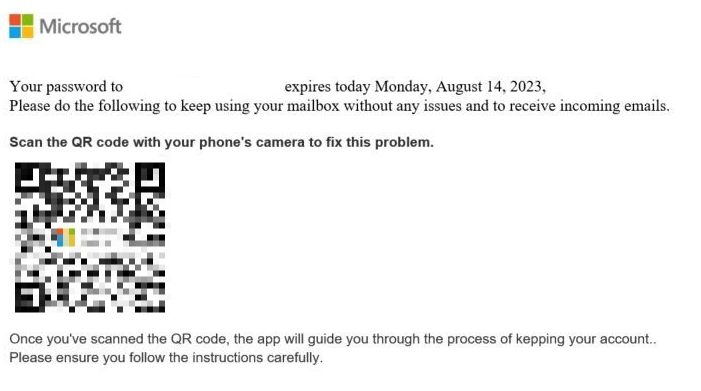
Example of QR code phishing email
An Integrated Defense
Fortunately, the targeted organization had previously implemented Corrata’s mobile threat defense solution. Corrata ZDP (zero day protection), a key element of Corrata MTD, identified the previously unseen link as suspicious, successfully blocked access to the malicious link and alerting the Security Operations Team through an automated integration with their SIEM, Google Chronicle. The response was swift and comprehensive:
- The Security Operations Team initiated an automatic process to filter out all related phishing emails from user inboxes, significantly reducing the risk of further compromise.
- Affected employees were alerted about the phishing attempt, and a mandatory password reset was enforced for all targeted accounts to mitigate any potential security breaches.
- The organization also took the responsible step of informing its supplier about the email account compromise, closing the loop on the immediate threat and potentially preventing further attacks.
Lessons Learned and the Path Forward
This incident is a stark reminder of the continuous evolution of cyber threats and the importance of staying one step ahead. It highlights not just the value of a robust mobile threat defense solution but also the critical need for integrating such solutions into the broader security operations technology stack.
Key takeaways for organizations looking to bolster their cybersecurity posture include:
- Vigilance against sophisticated phishing tactics: As attackers get more creative, awareness and education on new phishing techniques are paramount.
- Comprehensive security measures: Beyond traditional desktop and network security, mobile threat defense is a critical layer that organizations must not overlook.
- Integrated security approach: Seamless integration between different security solutions enhances the ability to detect and respond to threats swiftly and effectively.
In conclusion, this case study serves as a powerful example of how modern attackers seek to exploit gaps in defenses and the indispensable role of integrated, advanced security measures in protecting against sophisticated cyber threats. As we navigate an increasingly digital world, such proactive and comprehensive security strategies will be key to safeguarding valuable data and maintaining trust in the digital ecosystem.




