Why Google and Apple’s Malware Protection Isn’t Enough – Pt 2

Last week, Part 1 of our two-part series outlined the current defense systems offered by Apple and Google, two of the world’s biggest mobile operating system developers, to protect devices from mobile malware. Despite strict content requirements and security scans, malicious apps still appear in the Google Play Store and Apple App Store.
Circumventing the official app stores altogether
A number of hackers have learnt to circumvent these security restrictions. As we previously reported, ‘sideloading’ is the process of downloading and installing apps onto a mobile device from a source that is not an official consumer or enterprise app store.
For Android apps, this is relatively straightforward, done by enabling the download of an app .apk file from an ‘unknown source’. Hundreds of unofficial Android apps are readily available for download using this method both online and via third-party marketplaces such as Getjar, Mobogenie and Appbrain.
For iOS the process is a little more complicated but possible nonetheless. Just this year it was discovered that malicious app developers could pose as legitimate businesses to obtain Apple Enterprise App certificates, allowing them to validate and distribute apps independently of the official App Store. Pornography, gambling and fake versions of gaming apps developed under this program have all been discovered.
Although not used exclusively by fraudulent apps, many hackers use ‘sideloading’ to avoid security checks and regulations. Hackers take advantage of users’ attempts to avoid paying for content or to overcome geographical release restrictions. Sideloading provides malicious developers with the perfect vehicle to spread Trojans, spyware, adware, and click fraud malware.
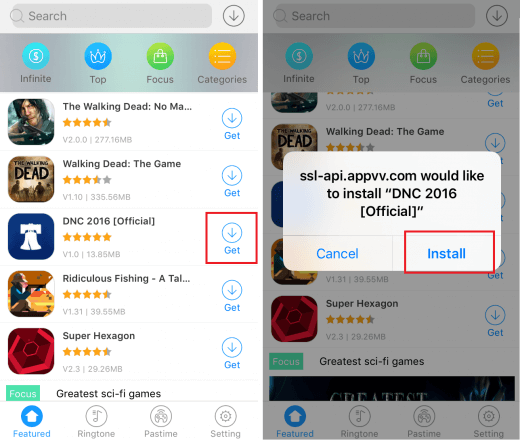
Downloading an app from an unofficial app stores
Not all malware delivered via apps
The reality remains that hackers aren’t just using apps to deliver malware to mobile devices. It has become increasingly more common for attackers to target email, SMS, social media sites, and WhatsApp. Many attackers prey on the trust we put in these services in the hope that someone will unwittingly click. One of the most high profile instances of malware distribution in recent years was Trident/Pegasus, a targeted spyware attack sent via SMS that exploited three zero-day vulnerabilities causing catastrophic data loss on iOS devices. The attacks allowed hackers to jailbreak devices. They can then gain access to messages, calls, emails, and end-to-end encrypted apps.
Just two weeks ago, the world learnt about a vulnerability in the audio call feature of WhatsApp. This allowed hackers to inject Pegasus spyware onto a device, regardless of whether the user answered the call or not. Described as “the most sophisticated” attack ever seen on an endpoint, the discovery of Trident/Pegasus has served as a major wake up call and reminder that any and all platforms have vulnerabilities and that blind trust in companies like Google and Apple may not be enough to protect from them.
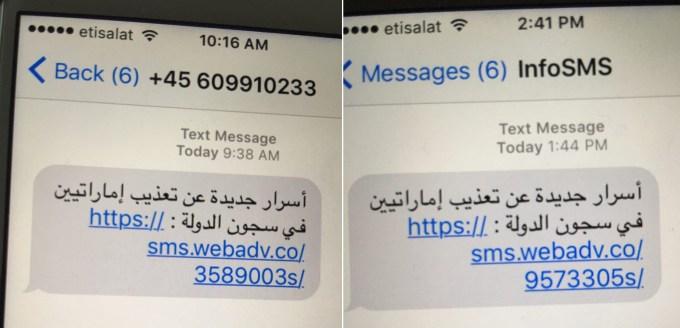
SMS messages that led to Trident/Pegasus attack
So how can we protect our devices?
If we cannot rely on Apple and Google, what can we do to protect ourselves from mobile malware? Firstly, education and exercising vigilance is key. Mobile users need to be aware of the potential dangers involved in processes like sideloading. Similarly, we should always be cautious of clicking on links or downloads in messages online. Even when we trust the source, we need to be aware offers that seem too good to be true.
As humans however, it is quite possible that we might mistake a cyber threat for a seemingly innocent app. To ensure protection from all forms of mobile malware, including ransomware, spyware, and Trojans, external security is essential. Dedicated mobile security products, such as Corrata Security and Control, that block access to suspicious sources such as unofficial app stores or malicious sites, and constantly monitor devices for evidence of malware infection are becoming more and more necessary to prevent malware infection and protect our sensitive data. So if your organization is concerned about the security of your data, now is the time to consider upgrading your defenses against mobile malware as well as the other threats we face in a mobile-first world.
To find out more about how Corrata Security and Control can protect your mobile devices from the threat of malware on all platforms, visit www.corrata.com.
For more industry news, insights and analysis – follow us on Twitter and LinkedIn!





