Understanding Malware Part 1 – What is Social Engineering?

Social Engineering – psychologically manipulating users to make security mistakes
Anyone following the latest industry news will know that one of the most significant cyber-threats facing organizations today is mobile malware. We constantly see reports detailing the latest malware strands making the rounds or malicious apps gaining access to the app stores. So what can we do? Defending against these attacks starts with understanding how they work. There are two categories of malware, Social Engineering and Advanced Mobile Malware. They are very different but equally dangerous and deserving of our attention. So let’s start with social engineering – what is it and how can we defend against it?
What is social engineering?
Social engineering is the manipulation or taking advantage of human qualities to serve the purpose of a malicious actor. The term describes the broad range of malicious activities that use psychological manipulation to trick users into making security mistakes. Most often, hackers prey on human emotions. The most commonly targeted psychological traits include carelessness, curiosity, fear, desire and ignorance. Generally, attacks like these occur when users believe they are downloading or accessing a legitimate service. In fact, hackers are actually tricking users into installing malware onto their device or disclosing sensitive information.
What makes social engineering especially dangerous is the fact that it relies on human error rather than vulnerabilities in software. Mistakes and lapses of judgement made by users are much less predictable and harder to prevent than software-based intrusions and therefore can present some of the biggest risks to organizational security. According to InfoSecurity magazine, the FBI recorded 40,203 cases of social engineering attacks around the world between 2013 and 2016, resulting in total exposed losses of over $5 billion. So let’s have a look at some examples of how malicious mobile apps use social engineering techniques.
Abusing accessibility features
One of the most advanced forms of social engineering in recent years is the ‘clickjacking’ of device accessibility features. A system called sandboxing protects ordinarily data found within mobile apps. This system prevents one app from accessing the content of another. But, by using Accessibility Services, hackers can circumvent sandboxing systems, allowing apps to see content and perform actions on other apps. Once users have granted an app accessibility permissions, hackers can use a technique called ‘clickjacking’. This process involves overlaying one application on top of another to propagate user’s clicks without their knowledge.
For example, a user downloads a legitimate looking gaming app from an app store or third party source. When installing the game, the user is asked to grant it permission to “draw over other apps”, a request that does not seem too suspicious as it is common to other legitimate apps such as Facebook Messenger. Then, without the user’s knowledge or consent, as they click on the character moving around the screen in the game, their clicks pass to the device settings which enables the game access to the Accessibility Services. Once plugged into these Accessibility capabilities, the malware in the game is then able to do pretty much anything that the owner of the phone can do – including perform banking functions, write or read emails, and create and read documents.
Earlier this year, it was discovered that several apps available in the Google Play Store appearing to be regular “call blocker” apps had been updated with malware code. Once installed, hackers used the ‘clickjacking’ technique to gain access to an estimated 10,000 users’ online banking apps.
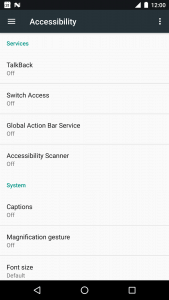
Screenshot of Accessibility Services on an Android smartphone
SMS fraud
Another form of social engineering involves enticing users to download and install a seemingly benign app. The device then sends premium SMS messages or signs users up to premium subscription services without their consent. Often these apps will also disguise their malicious activities by hiding disclosure agreements or SMS messages from the mobile operator notifying the user of charges or confirming subscriptions. Therefore, a user could potentially have the app on their phone without ever realizing the huge bills are accumulating.
For example, at the beginning of the year it was discovered that one of the world’s most downloaded weather apps had been collecting an unusual amount of data from smartphones and attempting to subscribe users to paid services without their permission. The app “Weather Forecast – World Weather Accurate Radar” appeared to be a legitimate weather prediction app. Over 10 million people downloaded it, ranking it among the top five weather apps in over 30 countries. However, Upstream Systems discovered that the app had attempted to subscribe more than 100,000 users to paid virtual reality services. The app would have accumulated bills of more than $1.5 million had the attempts not been blocked.
Adware
Adware’s primary function is to serve advertisements by hiding on devices. Cyber criminals push this popular type of malware onto mobile devices via social engineering. Adware generates revenue by automatically displaying online advertisements and encouraging users to click on links to malicious or unsavory websites. Some adware even tracks user activity to target users based on their interests and browsing habits.
In early 2019 several ‘beauty camera apps’ were discovered on the Google Play Store that were capable of accessing remote ad configuration servers that can be used for malicious purposes. This allowed the apps to push full screen ads to users when they unlocked their devices. These included ads with fraudulent content and pornography that redirect to phishing websites or malicious downloads. None of the apps acted unusually or gave any indication that they were the source of the ads. Many users would not even suspect that there was anything amiss until they tried to delete the app. It was then that they noticed that the app had hidden it’s icon making it extremely difficult to uninstall.
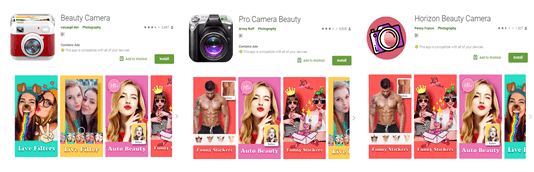
Malicious ‘Beauty camera’ apps on the Google Play Store
Credential stealing
Credential stealing is one of the most common consequences of social engineering attacks on mobile devices. Mobile has become our primary means for communication and a valuable avenue for accessing sensitive files and data. Dozens of malware masquerade as legitimate fitness, beauty, lifestyle, and gaming apps. They secretly contain adware to trick users into giving up their credentials to gain access to this data.
Just last week a gaming app named “Scary Granny ZOMBY Mod: The Horror Game 2019” with over 50,000 installs was discovered to be launching persistent full-screen ads on users’ phones and requesting them to input their login credentials. The game is fully functional, but asks users to restart their device to launch the game. This allows the malware to show full-screen phishing overlays even after the user reboots their device. The app then presents an extremely convincing-looking login page for trustworthy brands like Google or Amazon. The page prompts users to input their credentials. After successfully stealing the victim’s data, the app can then collect account information such as email addresses and verification codes. This is all occurring while the user is unaware and continues playing the zombie horror game as usual.
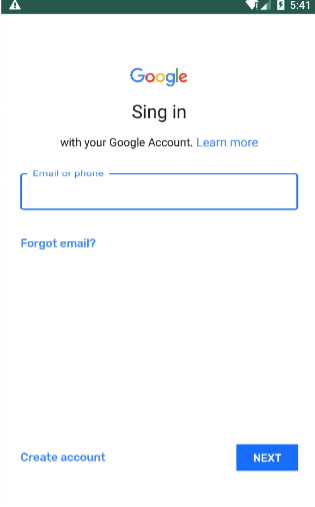
One of the credential phishing pages that appears for players of the “Scary Granny ZOMBY” game
How do we avoid social engineering attacks?
The main aim of social engineering is to manipulate users into infecting their device with malware. It is often much easier to exploit users’ weaknesses than it is to find a network to attack. In 2018, it was reported that human error is responsible for 95% of cyber-crime events and it is clear that employees themselves pose one of the greatest risks to the enterprise. However, security awareness training can go a long way towards preventing social engineering attacks. If people know the forms that attacks are likely to take, they will be less likely to become victims. Avoiding clicking links and downloads from suspicious sources or pop-ups, double checking apps and user reviews, and being wary of tempting offers that seem too good to be true can all be extremely effective in reducing the risk of falling victim to a social engineering attack.
However as these attacks become more convincing and therefore harder to recognize, human error is a guarantee. This is where external mobile threat protection solutions become essential. Solutions like Corrata Security and Control can use Machine Learning technology to protect mobiles from malware attacks in real time. This means that even if an employee is fooled by an app posing as the latest horror game or photo editing tool and clicks on a malicious link, they will instantly be blocked from accessing the site, protecting their device and the data it holds.
Check back next week for our profile on Advanced Mobile Malware.
To find out more about how Corrata’s solution could help protect your organization’s mobile devices from malware and social engineering attacks, visit www.corrata.com or email us at info@corrata.com.
For more industry news, insights and analysis – follow us on Twitter and LinkedIn!





