Your Roadmap To A Complete Mobile Threat Defense Solution

At Corrata, we are constantly monitoring the evolving mobile threat landscape to understand the tactics being used by cyber attackers in their efforts to compromise mobile devices. We also monitor the threat environment more generally to identify new attack vectors and techniques which will likely pose a significant risk to mobiles in the future. This work is critical for informing our product roadmap.
Over the course of 2022, we’ve been working on a range of enhancements to the Corrata mobile threat defense solution to address the changing security environment.
New Capabilities to Counter Continually Evolving Mobile Threats
Today we’ll be delighted to announce the launch of a range of new capabilities focused on defending against threats from Android malware, sophisticated spyware such as Pegasus, and state-sponsored cyber attacks.
Many of the capabilities we are announcing today are unique to Corrata. They leverage on our proprietary network traffic inspection technology – a technology that allows us to examine and control 100% of the IP traffic to and from mobile devices and not just the small subset of communications that travels over DNS. We developed this technology with a clear goal in mind – to provide the best possible protection for mobile devices.
IP Blocking – Mobile Threat Defense Taken to a New Level
Basic traffic filtering is done by scanning DNS lookups and blocking those deemed risky or suspicious. This is a technique known as domain name filtering, as it filters based on the domain name of the site. Corrata uses domain name filtering using both the DNS lookup (where the DNS traffic is unencrypted) and the server name indicator (SNI) in the increasing number of cases where the DNS lookup is encrypted.
Why is DNS important in Mobile Threat Defense?
The function of DNS is to translate a domain name (e.g. amazon.com) to the IP address of the server where Amazon is hosted. The vast majority of web traffic uses DNS to do this translation. But what about malware vendors? Conscious that security software may well be blocking malicious domains, many malware vendors will bypass the DNS completely by including the IP address of their command-and-control server in the malware package. This means that the malware resident on the phone can completely bypass the protection offered by DNS filtering.
Corrata has now addressed this weakness in malware defences by introducing the ability to block traffic to suspicious IP addresses.
Many malware actors are known to re-use the same server infrastructure (while frequently changing domain names).
By blocking access to these IP addresses, Corrata will disable the malware and highlight to the organization any devices which have been infected. This feature is unique to Corrata and not available on other vendors’ mobile threat defense solutions.
Geoblocking – A Regional Approach to Improving Mobile Threat Defense
So say you’re faced with an environment where there are heightened geopolitical tensions and evidence of increased offensive cyber attacks by unfriendly countries. What if you now know that one of the aims of your adversaries is to interrupt the smooth function of society. Say you’re a manufacturer of food labeling. You may not have considered yourself as critical infrastructure, but it turns out that your country’s enemies see you that way because they know that if your IT systems were disabled, it could quite easily result in food shortages.
The invasion of Ukraine has changed the geopolitical landscape.
Prior to this, we judged that giving our customers the ability to block traffic to a particular country would be of limited interest. The invasion has changed everything.
How do you block traffic to and from unfriendly countries?
You could block access to those countries’ top-level domains (for example, .kp for North Korea)… Would this do it? Well, actually no. Why?
Because there is no connection between a domain name and the location of the servers to which it refers. As a general rule, just because a server has a particular top-level domain name doesn’t tell us where it’s located. To block traffic to a particular country, you need to be able to block the ranges of IP addresses belonging to that country.
And this is what is now possible with the latest updates from Corrata. You can now prevent your employees’ phones from accessing servers in countries which you consider risky. Another unique capability from Corrata.
Port number – Blocking Illicit Traffic by Port Number
When cybersecurity researchers are checking sites to see if they contain malware, they will, as a rule, only examine the two principal ports for web traffic: port 80, which is used for HTTP traffic and port 443, which is used for HTTPS traffic. Knowing this, sophisticated attackers will sometimes hide their malware payloads in rarely used ports. This was exactly the mechanism used to hide the notorious iOS spyware Pegasus.
To find out more about this threat and how it is exploited, check out our mobile spyware article.
A Unique Approach to Strengthening Mobile Threat Protection and Detection
To strengthen our customers’ protection against these kinds of sophisticated attacks, Corrata is now able to block traffic on specific ports or ranges of ports. This is a feature generally found on firewalls and takes advantage of the Corrata app’s unique ability to monitor and control all traffic entering and leaving a mobile device. No other mobile threat defense product on the market today offers this capability.
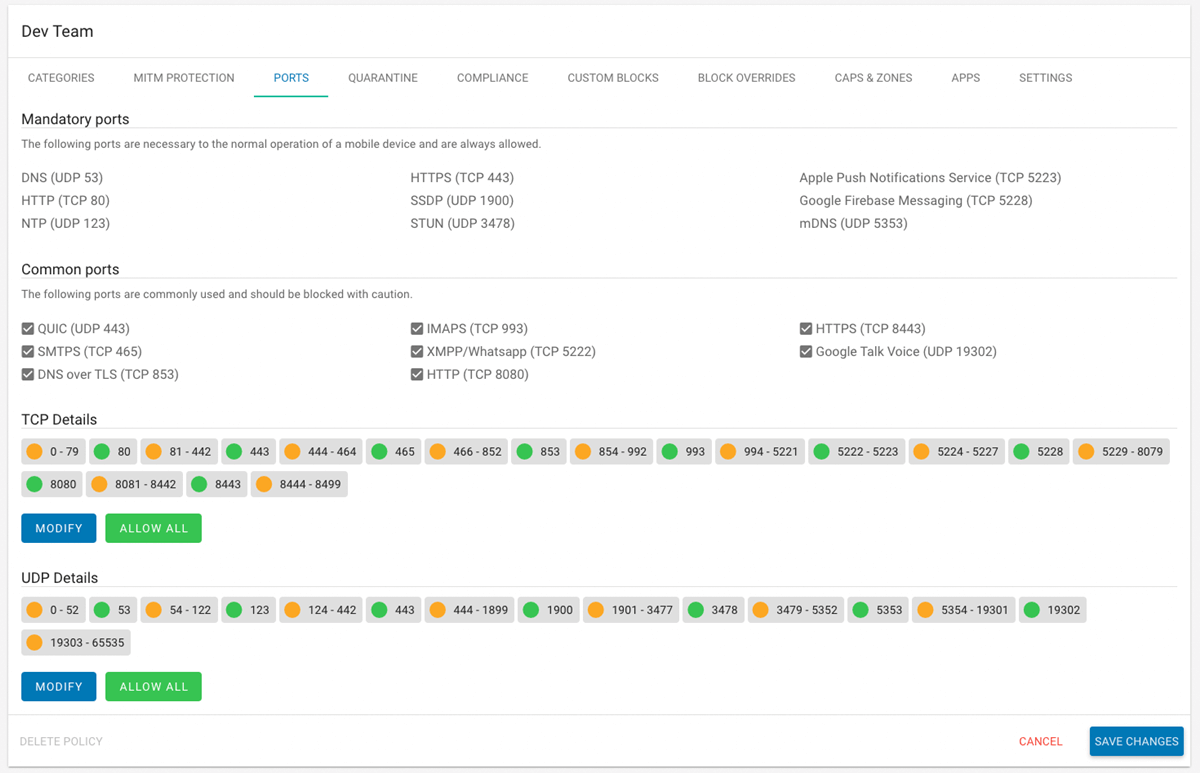
Screenshot of Corrata’s policy page for port blocking
Dangerous permissions – Corrata Slams the Door on the Number 1 Mobile Threat
Perhaps the biggest threat to mobile security is Dangerous permissions. To help you keep informed about this vulnerability, we have created an informative and comprehensive guide to how dangerous permissions are being exploited by the bad guys.
The nº1 way in which the bad guys scam people on Android is by tricking them into giving consent for the app to use functions which can then be exploited.
By far, the most dangerous permission to give to an application is the right to use Android’s Accessibility Service. This service is immensely powerful and allows an app to overwrite your phone’s screen with whatever content it wishes. This is often used to present fake login pages, which, once completed, allow the bad guy to steal your credentials.
Unfortunately, even the smartest people can fall for these scams on mobile. This leaves organizations vulnerable to credential theft because their employees could easily end up giving away usernames and passwords for business applications.
What is the Accessibility Service, and how is it exploited?
The Accessibility Service is intended to be used in the rare cases where an app needs to provide additional ways for people with disabilities to interact with it. As a result, only a handful of apps have a legitimate reason to use the Accessibility Service.
One thing that has helped muddy the waters in this regard is the fact that many security apps request Accessibility permission. In our opinion, this is extraordinarily poor practice… Unfortunately, a range of security software vendors continue to use the Accessibility permission in order to deliver their services.
How Corrata can help secure against exploitation of the Accessibility Service
To help organizations guard against this threat, Corrata introduced a feature which gives details of any app where the users have granted Accessibility permission. This acts as a warning to the Infosec team that a user may be vulnerable to an attack.
If this occurs, IT can quarantine the phone until it’s clear whether or not the application is legitimate. In keeping with the importance that Corrata places on employee privacy, we do not report on the apps installed on a user’s phone, instead adopting an exception reporting approach and only sharing information with the backend of the service when a clear security concern has been identified. In accordance with this approach, if our on-device software spots an app which is using dangerous permissions, this is reported to the Information Security team for further investigation.
Summing up – Mobile Threat Defense Made Easy
This rich suite of additional protections which Corrata is bringing to its customers and partners is part of our mission to advance the state of the art in mobile endpoint security and to do it in a way that is always consistent with employee privacy, user experience, and ease of use.
We look forward to your feedback on these new features and to continuing to advance our mission to continue to provide the best mobile threat defense solution in the business.




