Securing your Business Apps: Corrata’s Latest Updates

The cyber-threat landscape is evolving. 2021 has proven that even the biggest companies and governments in the world are vulnerable to cyber-attacks and need months to recover from the loss of data. Implementing strong security measures to protect business apps is more important than ever before. And this time, the security measures need to cover more than just emails and computers.
Unsecured mobile devices pose a significant threat to businesses
As experts in mobile security and threat defense, Corrata constantly monitors the ever-changing threat landscape to improve our solution. If the hackers are fast, we need to be faster. Keeping this in mind, we’ve developed 2 new features to provide an extra layer of protection to your business data and your employees.
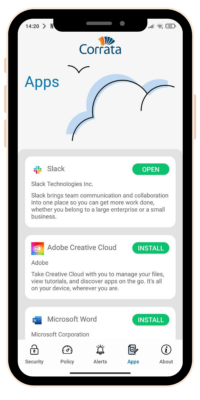 | 1) App CatalogApp catalog enables businesses to add their organization-approved apps to Corrata. This gives the employee a simple method to access their business-approved apps on their mobile device. Why is App Catalog Necessary? Malicious apps are widely available on official app stores. There is no guarantee that every employee in the organization has downloaded the correct app on their business device. Corrata guides employees to legitimate apps and prevents mistakes from happening. |
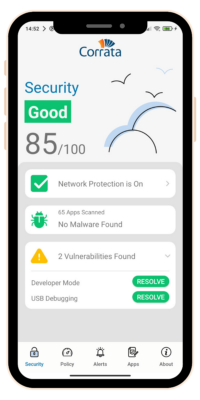 | 2) App QuarantineApp Quarantine enables organizations to instantly “quarantine” their business applications if an employee’s device has a low-security score. This protects organizations from exposure to data leaks before IT can step in and further assess the situation. Why is App Quarantine Necessary? Currently, if an employee’s device is compromised, the attacker may have access to the company’s resources like email, file shares, CRM, and Intranet. App Quarantine temporarily restricts network access to these resources keeping business data safe. |
Learn how Corrata detected a security flaw in one of the most visited websites in the world and prevented employee credentials from being intercepted.





