Phishing attacks are ramping up on smartphones

As remote working sets to become the ‘new normal’, securing mobile devices should be a top priority for companies
Spike in Phishing Attacks
Phishing is not a new concept. In fact, it’s one of the most popular and effective strategies deployed by hackers. Since the beginning of the pandemic, Covid-19 phishing emails alone have risen by 667%.
One common phishing tactic is to pose as a well known reputable business such as Microsoft or Amazon. These emails can be extremely convincing and difficult to detect. Revolut is the latest company hackers are impersonating. Recently, cyber criminals have been impersonating the financial tech giant through email and text asking customers to verify credentials and click on embedded links. In response, Revolut have warned their client base against these fraudulent messages with information on how to tell if a message is legitimate or not.

Phishing on Smartphones
While we tend to be on high alert for phishing attacks on desktop, we tend to let our guard down when it comes to smartphones. And, with the majority of us forced to work from home, we’re using our mobile devices twice as much. The reality is that mobile devices are particularly vulnerable to phishing due to multiple alternative attack vectors. Hackers exploit channels such as social media, SMS and popular messaging apps such as WhatsApp. Games, sports and dating apps have also been used to execute mobile phishing campaigns. And, attackers recognise that employees are relying more on their mobile devices. According to researchers, 87% of successful phishing attacks on mobile occur outside of email.
SMS phishing is becoming increasingly more common. Why, you may ask? This is largely due to the growing popularity in text message verification for 2-factor authentication or password recovery. While employees are quick to investigate a suspicious email, they are less likely to scrutinise a text message. However, a properly crafted SMS phishing attack can extract credentials or other highly sensitive data.
The Gaping Hole in Enterprise Security
Despite the risks on mobile, most enterprise security systems offer no protection against these threats. This is due to one simple fact: mobile devices access the internet over public networks (e.g. WiFi, 3G/4G). As a result, protections on the Corporate LAN, such as web gateways and firewalls, are unavailable. This means that these systems are powerless in preventing employees from accessing malicious sites.
There are two factors which significantly increase the risk of a mobile cyber attack. Firstly, research by IBM has shown that people are much more likely to fall for phishing attacks on mobile than on desktop. The smaller form factor makes it more difficult to detect the telltale signs of a possible scam.
The second factor is being unable to determine whether an attack has actually occurred. Mobile security systems such as MDMs or anti-virus software do not provide information about network activity. This makes it impossible to search the mobile fleet for indicators of compromise (IOC’s) when the security team becomes aware of an attack. Consider the implications: your CEO detects a spear phishing attack over SMS. He wants to know if any employees has fallen for the attack. Due to the lack of visibility, there is no way of knowing.
Plugging the Gap
Existing security solutions route employee mobile traffic through a gateway using either a VPN or proxy solution. However, this approach has major drawbacks. Firstly, it invades employee privacy as all internet traffic can be inspected by the employer. Secondly, routing to a single control point can impact performance and reliability. If the gateway goes down, all employee devices will become unusable.
Corrata has pioneered an alternative approach. Our ‘zero gateway’ technology offers the required level of protection but without the drawbacks outlined above. Instead of routing traffic through a central gateway, we analyse traffic on the device. Devices are protected against cyber threats without compromising user privacy. In addition, Corrata avoids the latency and reliability issues associated with a central gateway.
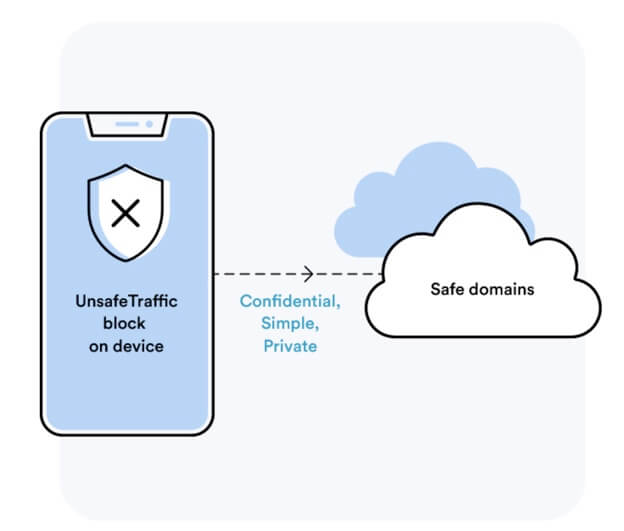
As remote working moves towards becoming the new normal, it’s more crucial than ever that employee smartphones and tablets are safe from the full scope of cyber attacks.





