Types of Mobile Phishing

Mobile phishing is becoming more prevalent and more difficult to spot
In recent years, hackers have moved away from traditional mediums like email. Instead, mobile phishing is their new approach and are targeting services like SMS, WhatsApp, Facebook, and fraudulent mobile apps.
Cybercriminals are adept at using social engineering techniques to make their content appear authentic. Research has found that mobile users are 3 times more likely to fall for phishing attempts compared to their desktop-using counterparts. Let’s explore the channels they are exploiting.
Top mobile phishing channels:
- Smishing
- Social media
- Whishing
- Malicious apps
Smishing
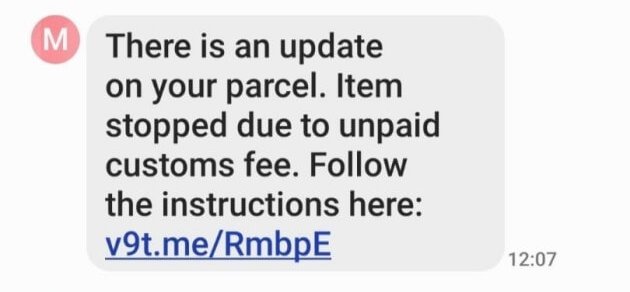
‘Smishing’ is popular because it focuses the attack on an often overlooked component of organizational cybersecurity: text messaging. The attacker sends a text to the victim’s phone that persuades them to click a link found in the message. Clicking this link results in one of two possibilities:
One – the link loads a phishing page, tricking the user to input their login credentials.
Two – it initiates a silent download of surveillance spyware to the device. Ultimately, the attacker’s aim is to gain unauthorized access to personal, sensitive and corporate data.
With open rates of 98%, too often is this attack successful.
Social Media
Social media is another method attackers are using. While companies prioritise security for workplace desktops, they generally ignore (or forget) mobile devices. This leaves the user free to engage with and download potentially malicious content.
The problem arises when they do inevitably engage with a malicious link embedded in a social media post. This is an extremely common way to trick unsuspecting users into revealing personal information and other sensitive credentials.
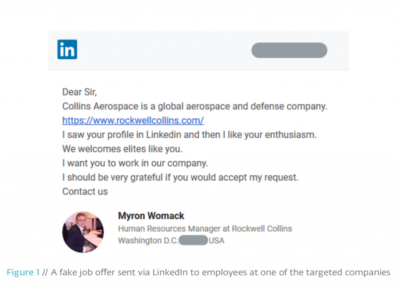
Malicious links appear across the board, and not just for the most popular sites such as Facebook, Twitter and Instagram. Even professional networking platform, LinkedIn, has been known to play host to similarly malicious phishing attempts. These attacks put both user and organization at tremendous risk.
Whishing and Messaging-Based Attacks
‘Whishing’ is the term coined to describe WhatsApp phishing. Because Whatsapp enables communication with anyone else on the platform, phishers can target a huge amount of users with the same blanket message. It’s a cheap and relatively easy way to quickly reach lots of users, which is why whishing is becoming especially prevalent.
Again, the mechanics are as simple as clicking a malicious link in a Whatsapp message but the consequences are anything but innocent.
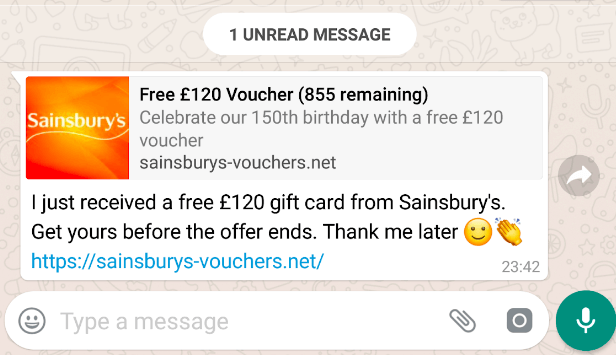
WhatsApp-based phishing, like any phishing attack, can be neutralized by blocking connections to the phishing server using a web gateway. However, today’s web gateways only work for devices on the corporate network. Mobile devices by their very nature, function on any network putting them at risk of phishing attacks.
Malicious Apps
Malicious applications arrive in different forms. The first is from unofficial app stores. Users may unknowingly download a mobile application riddled with malware. There’s no enforceable guarantee that the download is the desired app. Often, the malware only activates after the app installation.

Another entry point for phishing attacks is through malicious apps on official app stores. There have been countless cases of app removals from iOS and Android app stores.
Malicious apps on official app stores are generally, until Google or Apple themselves declare, undetectable. Corporate desktops have a regimented and pre-approved list of software. On the contrary, mobile devices are free to download any app from any network.
Conclusion
How can organisations protect themselves against mobile phishing attacks?
The first step is bridging any gaps in existing enterprise security, which we’ve found usually presents itself through insufficient or non-existent mobile security solutions. While corporate-owned desktops and laptops are secured from day one, organizations need to remember to safeguard their mobile fleet too. Corrata has helped financial institutions like Ulster Bank secure their devices from such malicious attacks.
And for more industry news, insights, and analysis – follow us on LinkedIn & Twitter




