Blog
Read our blog to get expert insights into the most pressing issues in mobile security including the latest threats and how to counter them.
Filter by:
-

Feb 12, 2026 · 15 min read
The Encryption Illusion: Why Your “Secure” Messaging Apps Aren’t Protecting Your Business Data
"We use Signal. We're secure." If that sentence sounds familiar, your organisation has a problem. Not because Signal isn't secure...Read more -

Feb 10, 2026 · 15 min read
Continuous Monitoring of TLS Encryption: What Corrata Sees in the Real World
Corrata’s Mobile Endpoint Detection and Response (EDR) solution runs directly on end-user phones and tablets across more than a thousand...Read more -

Jan 19, 2026 · 5 min read
An Overview of Data Loss Prevention (DLP)
Mobile devices have become the primary gateway to corporate data for most employees. With over 60% of enterprise data now...Read more -

Nov 26, 2025 · 8 min read
Landfall: Detecting Spyware in the Wild
In late 2025, Unit 42 published an in-depth analysis of a novel Android-focused spyware family, dubbed LANDFALL. (Unit 42) This...Read more -
Oct 30, 2025 · 7 min read
The Hidden Security Risks of AdInt
Data produced as a byproduct of the online advertising industry presents a significant risk to enterprise security. Every day, online...Read more -

Sep 26, 2025 · 3 min read
Dangerous Permissions – Location Tracking
Data showing the specific movement of tens of thousands of smartphones in Ireland is available to purchase from companies working...Read more -

Sep 9, 2025 · 10 min read
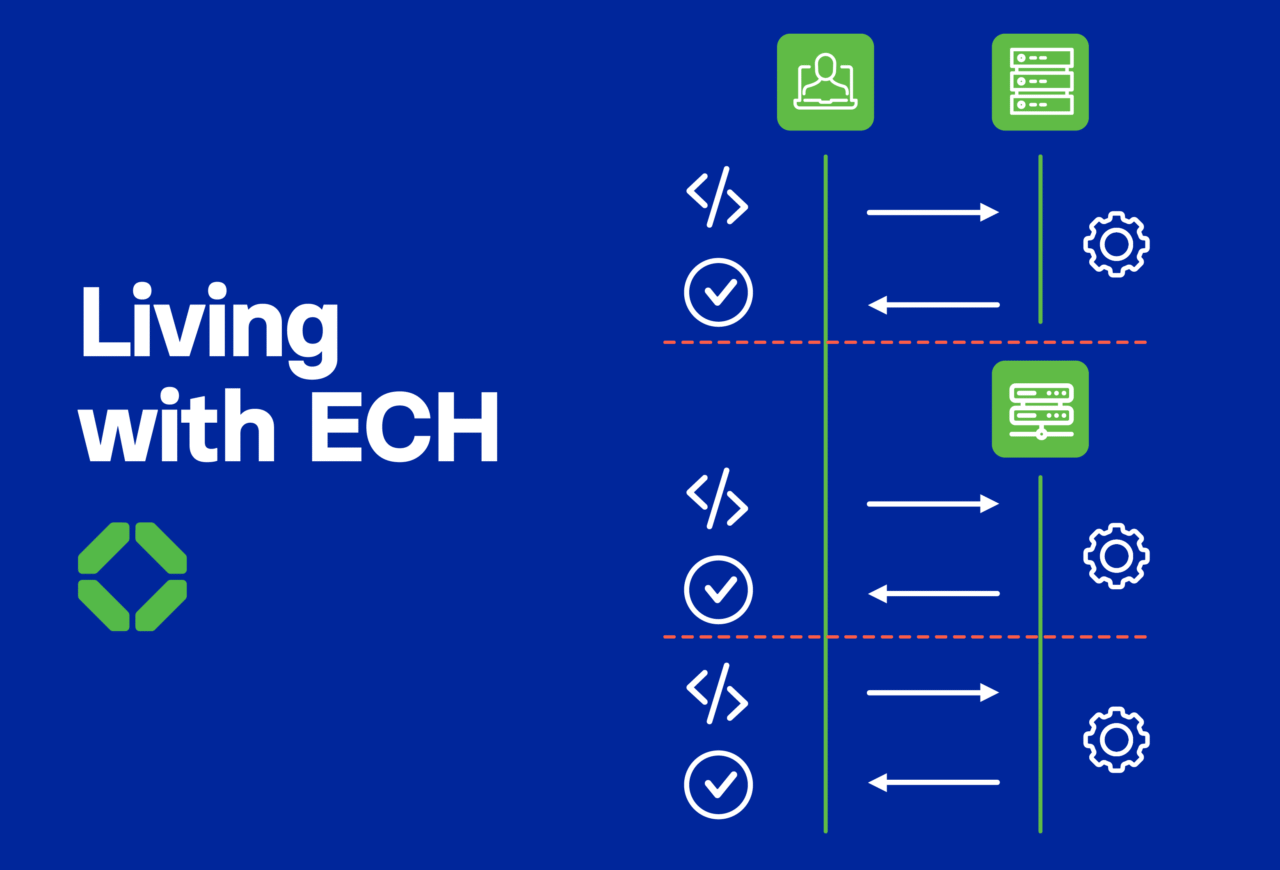
Is a new privacy protocol helping malicious actors more than internet users?
By Colm Healy published August 21, 2025 on TechRadar. ECH adoption is low, but risks remain for enterprises and users. Encrypted Client Hello...Read more -

Sep 9, 2025 · 6 min read
Pegasus, Graphite, Predator, Hermit Spyware – NSO and its clones
Commercial spyware: it hasn’t gone away For a brief moment, it looked as if the commercial spyware industry was on...Read more -
Jul 24, 2025 · 5 min read
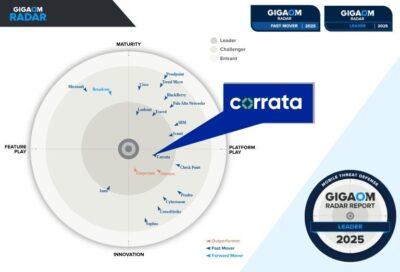
Corrata Named Leader and Fast Mover in GigaOm Radar for Mobile Threat Defense
DUBLIN, July 24, 2025 Corrata, a leading provider of enterprise mobile threat detection and response solutions, today announced its recognition as...Read more -
May 21, 2025 · 5 min read
Corrata Report Examines Impact of New Privacy Protocol
Encrypted Client Hello faces barriers to adoption but malicious actors are already taking advantage of the anonymity the protocol provides,...Read more -

May 19, 2025 · 5 min read
TLS – Trust the Lock, Not the Road.
Transport Layer Security (TLS) is the backbone of secure communication on the modern Internet. Over the years, TLS has evolved...Read more -

Feb 27, 2025 · 4 min read
No Filter – Part Two
Spear phishing attacks take advantage of gaps is network, application and browser protetctions Successfully blocking malicious links is the fundamental...Read more