Mobile Security Trends for 2022

The past two years have highlighted that the failure of adequate mobile endpoints will inevitably lead to them being targeted by cybercriminals and other bad actors. Widespread phishing, smishing, mobile malware, and ransomware attacks delivered via different platforms like SMS, email and social media have made businesses rethink their security strategy.
Additionally, high-level threats like Pegasus and cyberattacks on government organizations like the NHS in the UK, the HSE in Ireland, and Colonial Pipeline in the US, have highlighted that all it takes is one misstep to completely debilitate a country’s critical infrastructure.
Due to the above incidents, mobile threat defense has taken center stage, and organizations across the globe are significantly shifting their focus to secure their mobile estate.
Here are some of the biggest mobile security trends that we believe will impact businesses and government organizations in 2022:
Mobile phishing scams are increasing exponentially across multiple channels
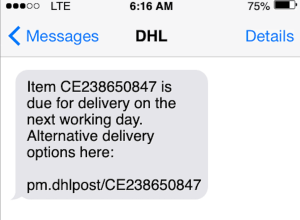
Mobile phishing scams were one of the biggest threats in 2021 and they will continue to grow in 2022. Mobile phishing includes traditional email phishing, smishing (sent via text messages), vishing (using phone calls or voice messages), and social attacks (phishing scams distributed via social media platforms).
Smishing scams in particular have become widespread due to COVID-19. It has become a popular avenue for cybercriminals due to the ease and lack of security in smartphones. There has been a 300% year-on-year increase in phishing attacks since 2020. There have been thousands of organizations and individuals who have been victims of such scams. Mobile users are 3 times more likely to click on a phishing link in a text message than on emails.
Sophisticated attacks move beyond the geopolitical
Sophisticated mobile malware has been successfully used for a number of years by nation-states for cyber espionage and by repressive regimes targeting journalists, dissidents, and civil rights activists. However, such tools are no longer the preserve of state actors. Today, cybersecurity practitioners have little visibility of the extent to which their staff is being targeted as these attacks are impossible to detect without equally sophisticated mobile endpoint security. As more organizations enhance their mobile security game, we expect to see more reports of organizations successfully defending attempts to compromise their mobile communications
DNS filtering solutions go dark – Adoption of encrypted DNS
Today many organizations rely on DNS filtering as the first line of defense against cyber attacks. DNS filtering examines the requests by devices to access internet domains blocking anything that is potentially malicious like a phishing or malware download site. Until recently, this has been easy to implement technically because DNS traffic is unencrypted. However, this is changing as the industry moves to enhance privacy by implementing encrypted DNS using either DNS over HTTPS or DNS over TLS. The downside is that many DNS filtering solutions will now go dark and will be unable to ‘read’ (or ‘sniff’ to use the colloquial expression) the DNS queries. As a first step, some organizations are blocking access to services that provide encrypted DNS. Unfortunately, this approach only works in a limited number of circumstances and is easy to bypass. Our recommendation is if you’re implementing a mobile endpoint security solution make sure it is robust enough to work when DNS traffic is encrypted.
Conditional access: The future of accessing corporate information from your mobile device
The pandemic has accelerated the move from the traditional perimeter-based security model to ones that work regardless of where the employee, application or device is located. Above all, we are seeing rapid adoption of ZTNA – zero-trust network access. In the future, any device or user looking to access corporate applications or data will need to be continuously validated. In effect, their access is conditional on their providing proof that they are legitimate. Conditional access can protect the organizations from data theft by preventing the download of sensitive files, requiring multiple authentication to access certain documents/sites, and preventing the upload of unsecured files. A critical part of conditional access is ensuring that the device requesting access is secure. Mobile endpoint security solutions can provide this assurance and we expect to see many organizations deploying them as part of the move to Zero Trust Network Access.
Privacy legislation begins to bite
Over recent years privacy legislation has been enacted in a wide variety of countries and regions. Initial moves by organizations have focused on ensuring baseline compliance. What we now see are organizations taking a much more thorough approach to the obligations in relation to end user privacy. This means that new security solutions in the future will need to work well without engaging in anything that looks like employee surveillance. This will prove challenging to many providers who have built their security approach on an assumption that they can engage in indiscriminate and widespread data collection.
Today’s mobile security solutions need to evolve and adapt to the growing threat landscape. Traditional mobile anti-virus scanning does not have the capabilities to detect and protect your device from advanced phishing and malware attacks. Mobile devices are imperative to our personal and professional lives, thus, it is important to put a guard on the gates to ensure your data is secure from current and future threats. Corrata mobile security is an immune system for mobile that protects your data without compromising your privacy. Get in touch for a live demo.




