Avoiding Detection

SMS phishing scam attempts to hide to avoid detection engines
Corrata observed a sms phishing scam targeting Irish mobile users “in the wild.” The attack itself was designed to harvest credit card credentials, but what made it noteworthy were techniques which were designed to prevent automated anti-phishing engines from easily detecting it.
Description
The following SMS message was received by users on Irish mobile networks.
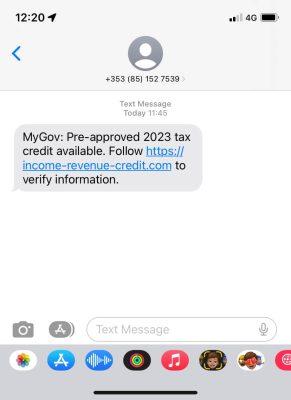
Clicking on the link brought the user to the series of pages which are replicas of the Irish tax authorities website.
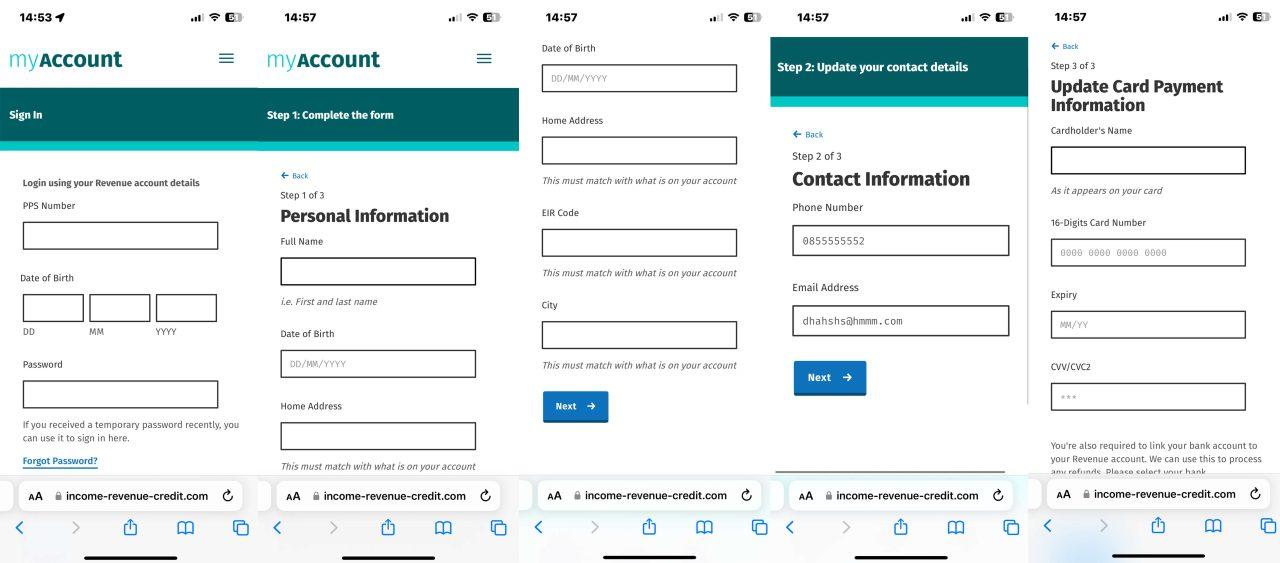
Attacks of this type are not uncommon. We have noted that attackers have become much more adept at providing credible fake landing pages which are difficult to distinguish with the naked eye.
The video below shows how the user is guided through the website to the point where credit card details are requested.
Avoiding detection
Fast detection is critical to defending users against such attacks. When a new domain is identified by a web-filtering or anti-phishing engine it is immediately subject to automated scanning to look for indicators that it might be malicious. This is especially the case when the domain is recently registered.
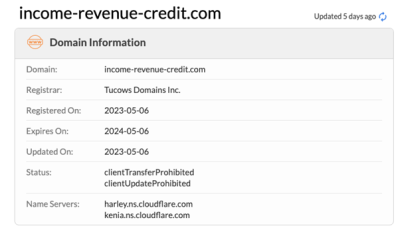
Whois details for the malicious domain
The attackers behind the domain income-revenue-credit[.]com, however, used two techniques to try and avoid detection.
When the attack was first launched, only the first page was accessible. This was designed to make detection less likely. When a user pressed submit, nothing happened. 24 hours later, the fake website was fully operational.
The website was also designed to be non-responsive to queries from a desktop browser. As many phishing systems are designed to detect traditional email phishing, they rarely scan domains using a mobile browser. By being non-responsive to scanning, the phishing site effectively remained invisible.
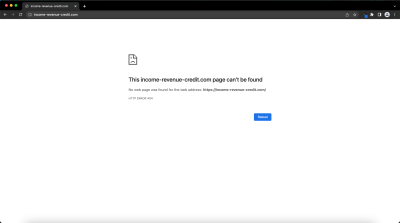
Response when attempted to access site with Chrome for desktop
Conclusion
Attackers are very aware of the sizeable resources which are being directly at disrupting their attacks and are constantly evolving their techniques to maximise the possibility that an attack will reach their intended victims. For them, it’s a funnel from delivery through to success which they look to optimize constantly. The kind of techniques which Corrata observed in this attack will no doubt evolve and mutate over time. The battle is constant.





