Why Google and Apple’s Mobile Malware Protection Isn’t Enough – Pt 1

Mobile malware can take many different forms. Spyware, adware, ransomware, and Trojans commonly hide in seemingly innocent apps. Attackers design malware to fool users so that they can take over, damage, and steal information from mobile devices. And with 42 million mobile malware attacks occurring every year, the problem only seems to be getting worse. In this two-part series, we take a look at two of the biggest mobile operating system developers, Apple and Google. We explore what they are doing in response to this growing malware problem and discuss whether this is enough…
Google and Apple’s security features
Google Play Protect (GPP) is Google’s built-in security feature for Android devices. Describing itself as “the most widely deployed mobile threat protection in the world”, GPP combines new and existing security technology to scan over 50 billion apps across 2 billion devices every day ensuring that the official Google Play Store is free from any malicious software or “Potentially Harmful Apps” (PHAs). According to Google, they rigorously analyse all apps before publishing them to the Play Store. Google then regularly scan all devices to ensure that apps are behaving as they should. Any apps exhibiting signs of malicious or improper behavior are promptly flagged to the user or removed from the device. In their 2018 Year in Review, Google reported an overall reduction of 15% in Android PHAs following the release of GPP, with the number of PHAs installed from inside the Google Play Store decreased to only 0.04%.
Meanwhile, since the release of the App Store in 2008, Apple have portrayed the iPhone as impenetrable. Apple state that they “review all apps and app updates submitted to the App Store in an effort to determine whether they are reliable, perform as expected, and are free of offensive material”. Apple examine all apps under strict technical, content, and design criteria. This includes performance, functionality, permissions required and description accuracy to determine whether apps are legitimate and safe for iOS users.

Google Play Protect
Google’s protection not what it seems
Despite Google’s positive findings in their 2018 Year in Review, we continue to see reports of fraudulent or malicious apps discovered on the Google Play Store. In March, a Motherboard investigation found more than 20 Android apps available in the Play Store advertised as offering promotions from cell phone providers but actually installing malware to steal data and leave devices vulnerable to additional hacking.
Similarly, Trend Micro recently discovered several supposed ‘beauty camera’ apps redirecting users to pornographic content and phishing websites while also collecting private data from the device. One of the most high profile of these discoveries occurred in 2018 when 12 apps on the Google Play Store designed to look like race-car driving games were discovered being used to install malware with full access to device network traffic. More than half a million Android users downloaded the apps. Two even trended on the Play Store, before the discovery was made. This further highlights the limits of Google’s security features.
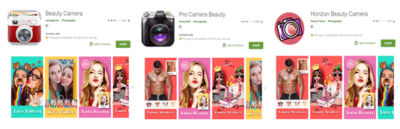
Screenshots of the malicious beauty camera apps on Google Play
iOS apps misbehaving
Despite Apple’s reputation, the App Store has also fallen victim to potentially malicious apps evading its vetting standards. In January 2019, researchers discovered more than a dozen iPhone apps covertlly interacting with the same command and control server previously used by known Android malware. ‘Goldluck’ was a strand of mobile malware which previously infected classic and retro games on the Google Play Store. By embedding backdoor code into the device, Goldluck allowed hackers to access high-level device privileges. They could then run malicious commands like sending premium SMS messages without the victim’s knowledge.
Last year researchers were surprised to discover 14 iOS ‘retro game’ apps (that made it through Apple’s strict vetting process) communicating with the same server used by the Goldluck malware. Although found to be mainly benign, the communications did present some evidence of sending IP address information and user location data back to the server. While the apps themselves were not technically compromise, the link to this server presented a serious risk for data exposure. It highlighted the potential for hackers to gain access to iOS devices via seemingly innocent apps from the App Store.
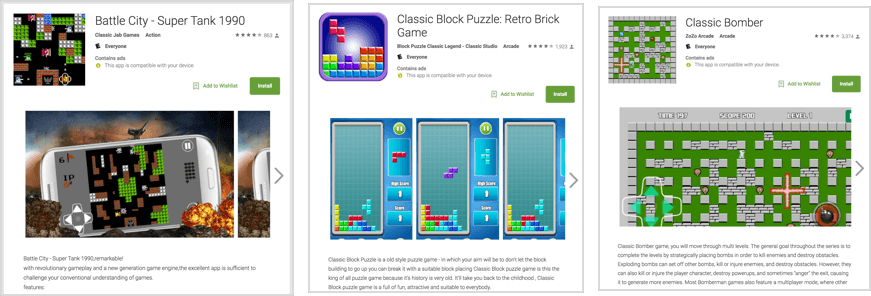
Some of the game apps on the App Store found communicating with the Goldluck server
To sumarize, Apple and Google’s security processes are flawed, leaving users potentially vulnerable to malware attacks.
Click here for Part 2 of our two-part series, where we will examine other ways in which mobile malware can circumvent these defenses, as well as the alternative measures we can take to protect ourselves and our mobile devices.
For more industry news, insights and analysis – follow us on Twitter and LinkedIn!