Use Case
Data Loss Prevention
Organizations need the right data loss prevention tooling in place on all endpoints to allow their employees fully embrace the benefits of AI Chatbots and use cloud services responsibly.
By unloading corporate data to unsanctioned LLM’s, email accounts, file sharing sites and other cloud services employees can put your company at risk of disclosing sensitive internal information, IP and customer data.
While interacting with the online world employees unknowingly share sensitive information about online and offline behavior.

How Corrata prevents data loss
Corrata operates to protect against unauthorized sharing of data from employees phones and tablets. Access to ShadowAI and other unsanctioned services is blocked. The use of previously unknown applications is identified and policies are updated accordingly. Inadvertent sharing of PII with data brokers is prevented. |
Endpoint DLP for Mobile
-
Prevent misuse of AI Chatbots
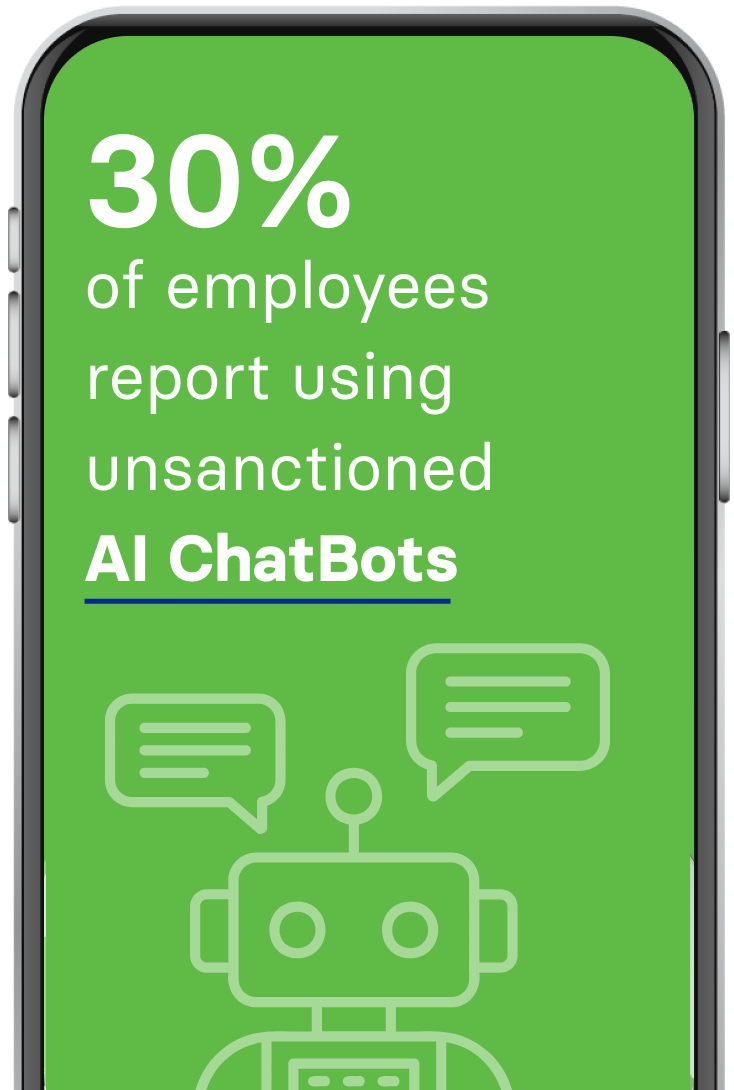
ShadowAI is a new risk vector for data loss
Many employees report using unsanctioned AI services to improve productivity. Corrata provides organizations with a comprehensive capability to monitor and control such use at the mobile endpoint significantly enhancing the basic controls available with MDM.
-
Enforce policies for File Storage and Email services
Prevent the use of unsanctioned cloud storage or mail services
Corrata prevents mobile users either intentionally or inadvertently uploading sensitive files to unapproved files shares, email and collaboration applications – whether through mobile apps or web browsers.
-
Monitor use of both sanctioned and unsanctioned SaaS services
Allow, block or monitor use of popular enterprise SaaS
Typical medium and large organizations use over 100 individual SaaS services across sales, marketing, finance and IT. Increasingly these services a mobile first. Corrata’s fine grained controls allow you to implement policies which balance risk with productivity.
-
Ad Intelligence
Prevent leakage of PII via the online advertising ecosystem.
The real-time bidding advertising eco-system shares sensitive data with thousands of unregulated data brokers. This has become a channel for the leaking of sensitive employee data including location information. Ad-Blocking and Location Permission controls prevent the leakage of PII into the highly opaque environment.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management





