No Filter – Part Two

Spear phishing attacks take advantage of gaps is network, application and browser protetctions
Successfully blocking malicious links is the fundamental technical defence against spear phishing attacks. However, on mobile devices, this protection is far less effective than many realize, leaving enterprises exposed to various threats.
To understand why we’ll use a recent phishing text that was delivered to the phones of one of our staff members as a case study.. While this isn’t the kind of highly targeted attacks we see delivered to our enterprise clients, it nonetheless will serve to illustrate how unreliable the build-in protections provided by networks, applications and browsers.
The First Line of Defense: Carrier-Level Filtering
For SMS based attacks, the first line of defence should be an SMS firewall deployed on the carrier network. But this is where the problems start: its not mandatory for carriers to implement such firewalls in all jurisdictions. Even where such firewalls exist they simply cannot be tuned to reliably spot every zero day malicious url without generating large numbers of false positives (and angry customers). They face the same problem when they filter based on keywords e.g. messages with the name of a bank or postal service are often blocked.
It’s worth noting that text message services aren’t just about text. With the use of iMessage and the wider adoption of RCS the ‘texting’ channel increasingly sees multimedia content. Recently we’ve seen attackers adopt detection by sending links in pdfs. To avoid keyword filtering the ‘text’ accompanying is now being sent as an image
So lots of attacks get through the carrier. Similar issues arise if you’re receiving a link over another channel whether its iMessage, RCS, WhatsApp or Teams. The operators of these services struggle to filter out spear phishing attacks as their filtering is designed to block ‘consumer’ grade fraud. Today most of these services over end-to-end encryption for messages sent between two devices. In this scenario filtering is limited to the connections they offer to businesses.
But getting back to our recent phishing text. Where are the other opportunities to filter out these malicious messages ?
The Browser’s Role in Blocking Malicious Links
The next line of defence is the browser. On mobile the predominate browsers are Chrome and Safari. Both use the Google Safe browsing block list but the refresh rates appear to vary. In the case of the recent phishing text received by our employee we found that while Safari correctly identified it as malicious, Chrome did not.
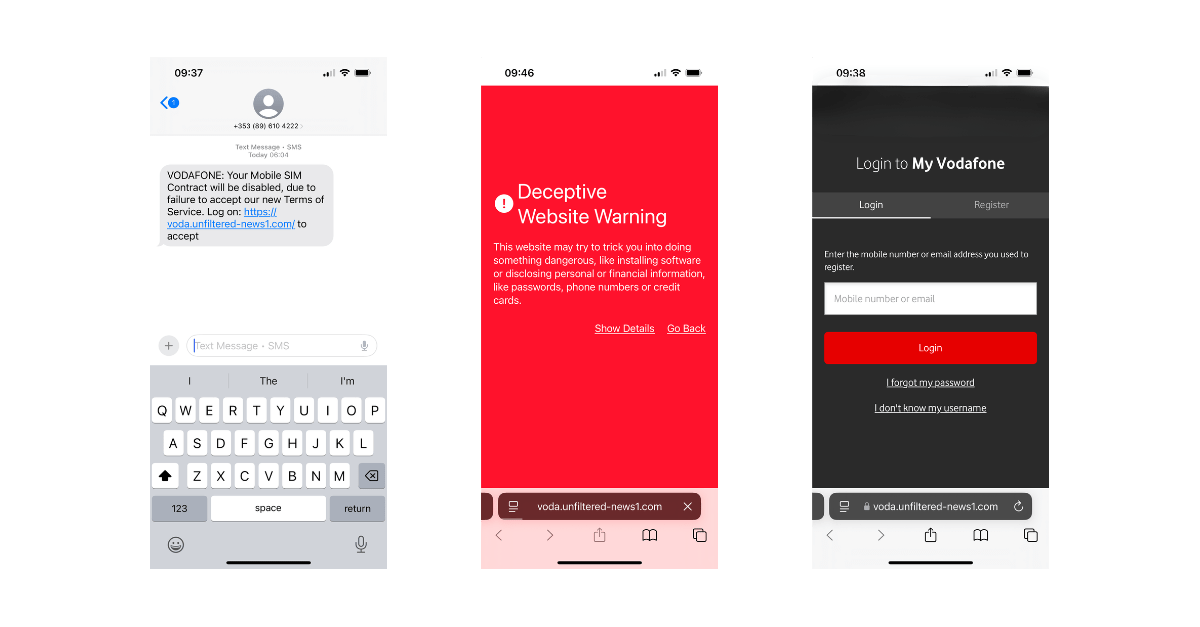
Phishing site blocked by Safari but allowed by Chrome
A check on VirusTotal showed that at of ninety four vendors, only Google detected this link as problematic. This is worrying as it suggests that the next line of defence, web filtering solutions, might not be updated sufficiently quickly to block the malicious link in the message. Web filtering can be deployed on network (for example if you’re connecting to your corporate wifi network or using a vpn or equivalent to connect to a gateway ) or on device (if you’re device is running an mobile endpoint security solution). But some such solutions have blindspots. Their threat intelligence can be out of date. When we tested the malicious link using a leading mobile threat defense solution the link was not marked as dangerous. Another issue is when filtering is limited to DNS ‘sniffing.’ This is a lightweight approach to filtering by examining only DNS traffic (a tiny proportion of all IP traffic going to and from a device) which, when introduced first, was very effective. However, Corrata research shows that circa 20% of devices are now using encrypted DNS making DNS sniffing completely ineffective. Secure Web Gateway solutions can overcome this blindspot but bring with them challenges around latency and privacy. On device solutions can avoid these shortcoming, but none of them, with the exception of Corrata, incorporate the host firewall technology required to accurate identity malicious domains.
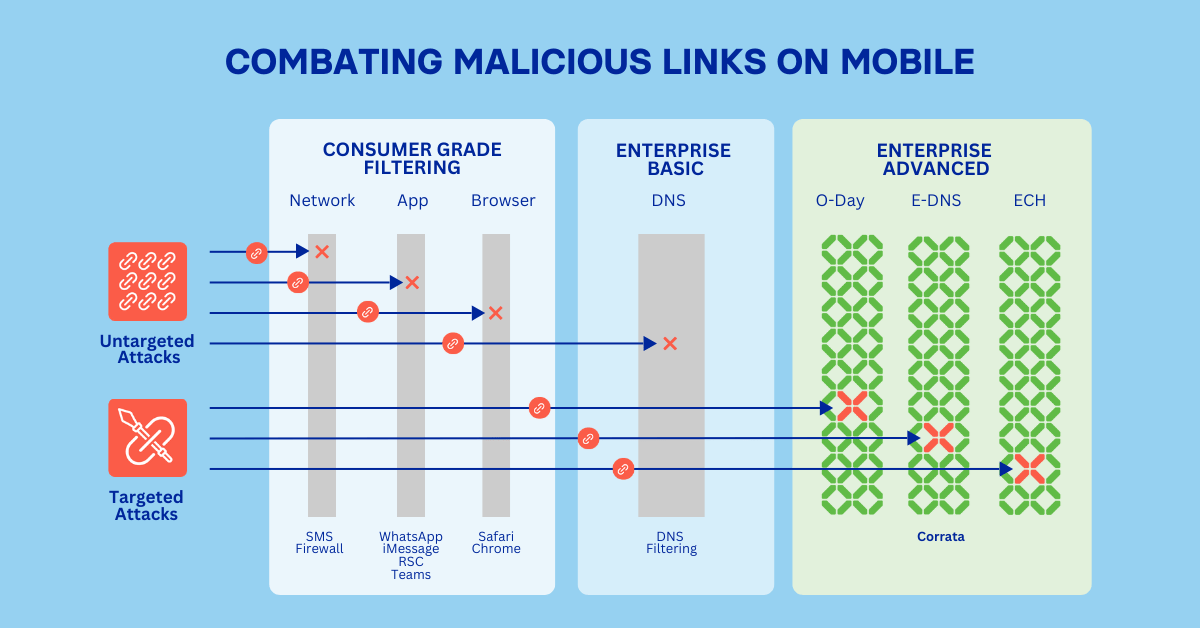
Effectiveness of consumer and enterprise protections
Attackers’ Evasion Tactics
Coming back to our case study – it turns out that our attackers took further measures to avoid detection. The domain’s DNS information initially directed the browser to Cloudflare’s infrastructure. And the attackers used this to take advantage of Cloudflare’s support for Encrypted Client Hello (ECH). ECH hides the name of the requested domain which would otherwise be transmitted in the clear and therefore detectable at the firewall level. The net/net of this is that, for those 20% of devices which use encrypted dns, the malicious site would be completely undetectable. The Corrata Labs team has identified that over 90% of phishing sites are now using Cloudflare ECH to bypass security controls.
| Defense Layer | Weaknesses |
|---|---|
| Carrier-Level Filtering | Not mandatory; weak against zero-day threats; easily bypassed with images/PDFs |
| Messaging Apps (iMessage, RCS, WhatsApp, Teams) | Limited filtering capabilities; phishing links often go undetected |
| Browser Protection | Google Safe Browsing updates inconsistently; Chrome and Safari results vary |
| Web Filtering Solutions | Threat intelligence delays; encrypted DNS bypasses detection |
| Secure Web Gateway | Cloudflare ECH encrypts domain requests, making firewall-based filtering ineffective |
Table summarising the gaps in protections
The combination of ‘permissive filtering’ by service providers and browser vendors and gaps in ‘lightweight’ enterprise solutions means that organizations are more exposed to spear phishing attacks on mobile that they appreciate. This is a marked contrast to the corporate email box: defenders and solution providers have worked relentlessly to augment the limitations in the built-in protections. Attackers are fully aware that other messaging platforms are both growing in popularity within the enterprise and that such channels are poorly defended. Its time for organizations to re-visit their risk assessments in light of the challenges that mobile brings.




