Is it Safe ?

When devices hide their identity, how can we tell if they are safe?
Many of us, especially those of a certain age, are still haunted by the dentist scene in the 1976 movie Marathon Man. Dustin Hoffman’s character writhes in agony as his Nazi war criminal interrogator drills into his unanesthetized teeth, repeatedly asking, “Is it safe?”
While such extreme methods are hardly appropriate for cyber defense, establishing the security status of user mobile devices often feels just as daunting. Why does this matter?
When users attempt to access an application, it’s crucial to know their device’s security status. A compromised device poses a real risk of becoming an entry point for account takeovers, malware infections, or data theft.
Hidden identity
You’d think verifying a device’s security status would be straightforward. Ideally, you’d confirm that security software is active and reporting a good security status, with no indicators of compromise, an up-to-date operating system, and secured with a passcode or biometric authentication. However, the privacy models employed by iOS and Android complicate the connection between security software signals and access requests, making it generally impossible.
The main issue is that neither iOS nor Android allows third-party apps to share a unique device identifier. Consider your email client, CRM app, or browser requesting access to company data. While these apps can provide user credentials and undergo authentication, they cannot confirm the device’s identity. Even if a security solution is mandated, and the app signals the device’s safety, there’s no guarantee it’s the same device trying to access corporate applications. Moreover, enforcing the installation of security applications is unfeasible without a unique identifier.
One exception exists for devices enrolled in a mobile device management system, which can share a unique device identifier and sync it with security software signals. But what about the millions of employee-owned devices routinely accessing corporate data? A recent Samsung survey found that only 15% of organizations provide smartphones to all employees, with 46% adopting a hybrid approach and 39% fully relying on BYOD.
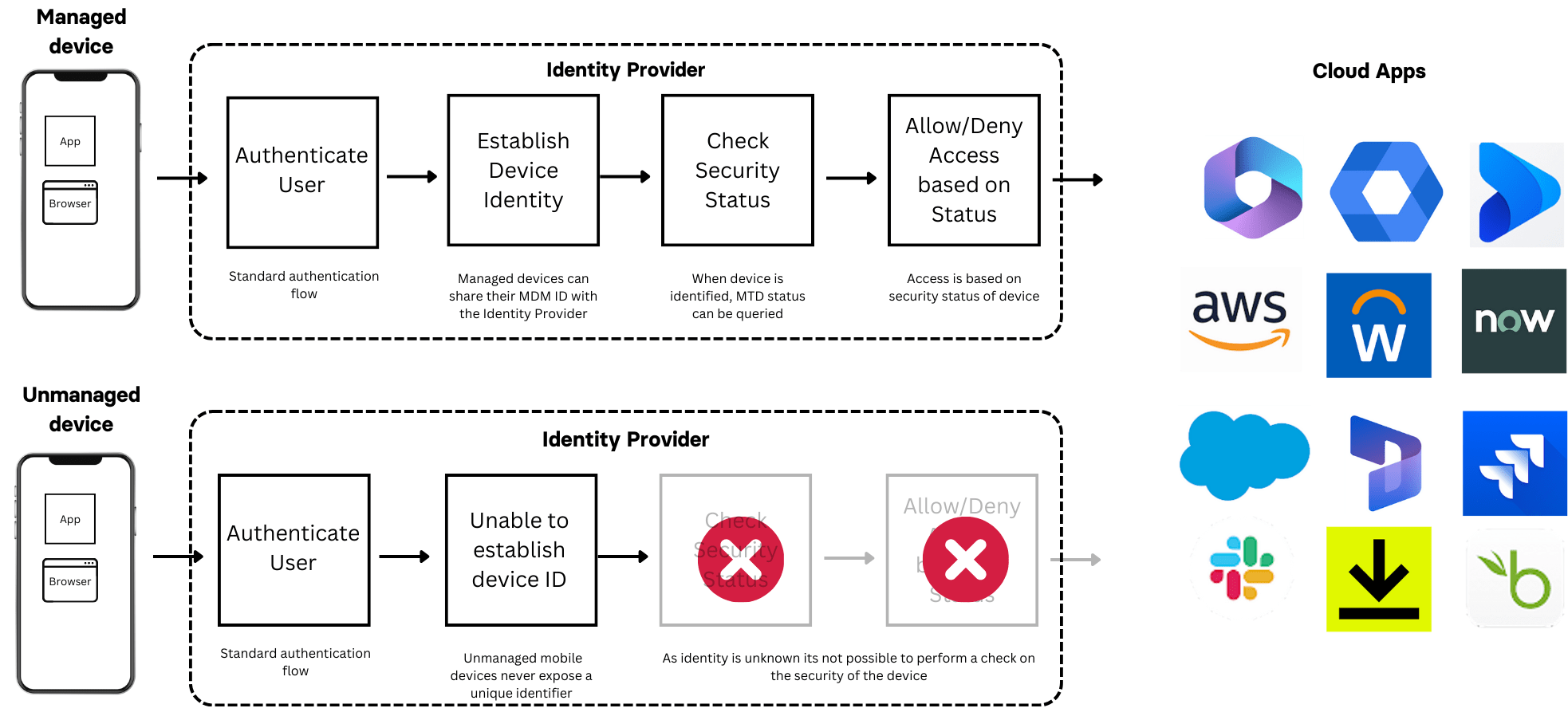
Device identity with managed and unmanaged devices
The Limitations of MAM
Many organizations use Mobile Application Management (MAM) to manage BYOD challenges by focusing on the application rather than the device. MAM is supported by productivity suites like Microsoft365 and Google Workspace, but most popular SaaS applications do not support MAM. This leaves organizations facing difficult choices: compromise on digital transformation by limiting SaaS app usage to company devices or compromise on security by allowing access from devices with unknown security statuses.
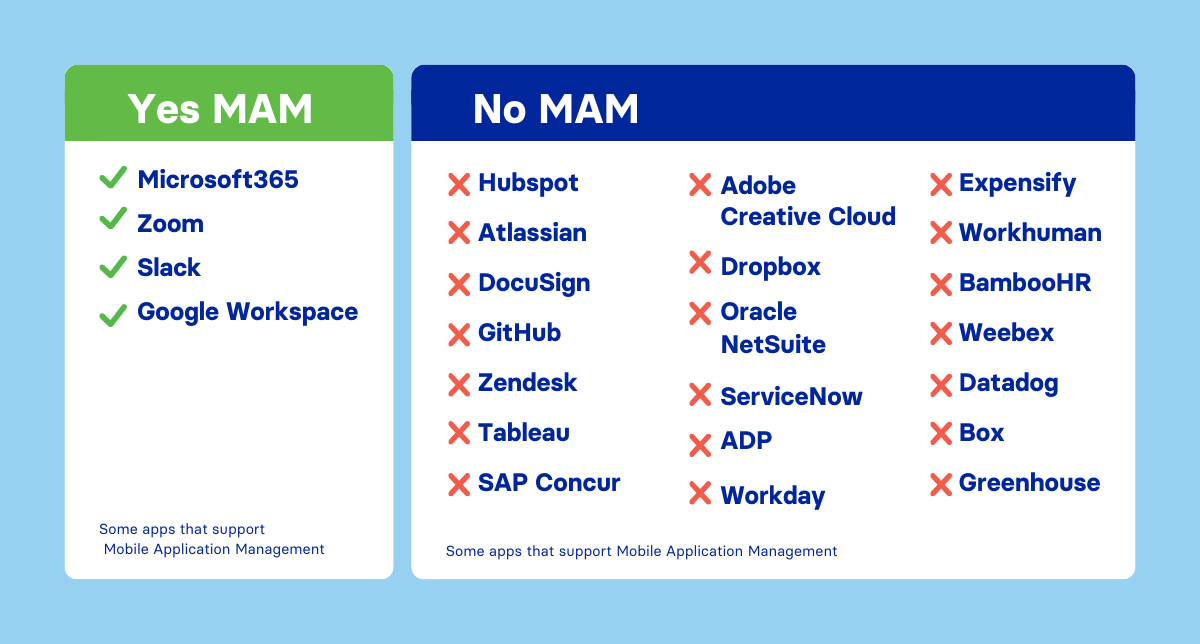
Extent of support for MAM across popular enterprise apps
Corrata to the rescue
Fortunately, help is on the way. In 2024, Corrata will launch a new version of our popular Mobile Threat Defense (MTD) solution that works seamlessly on both managed and unmanaged devices. Corrata’s innovation eliminates the need for IT departments to depend on employee diligence in installing MTD on personal phones. With Corrata’s solution, installation of MTD can be enforced as a precondition for accessing any business application, securing unmanaged devices like never before.
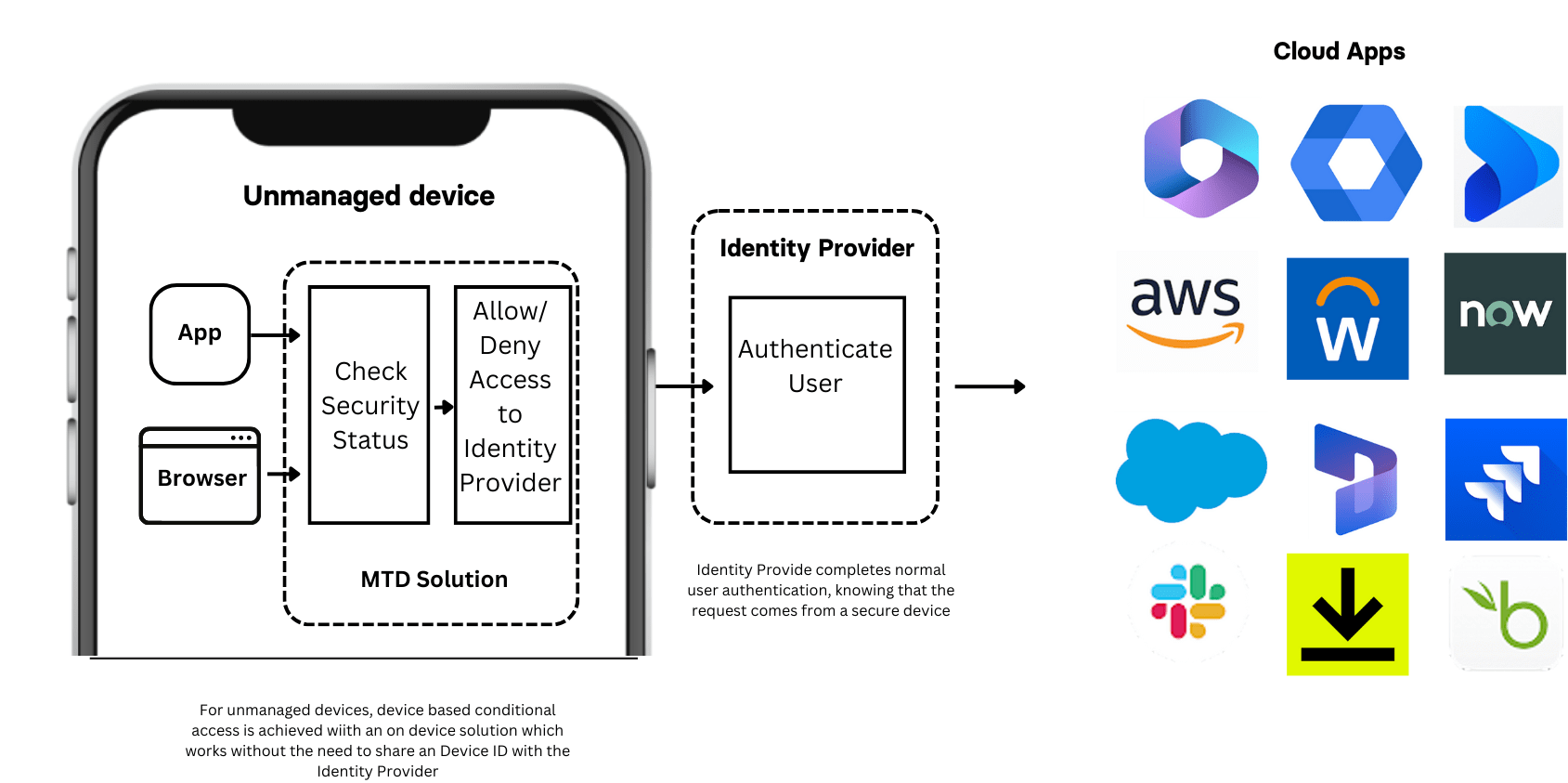
Corrata’s solution for securing BYOD access
For CIOs, this represents a myriad of possibilities. It marks the end of having to choose between security and digital transformation. Access can be granted to any application from any mobile device, potentially reducing the corporate device fleet and delivering cost and administrative savings. More importantly, it offers measurable risk reduction for organizations worldwide.
Interested in how Corrata’s forthcoming solution for BYOD can benefit your business? Join our beta program to learn more.




