The dangers of Stalkerware – Corrata investigates surveillance apps

With stalkerware cases rising, Corrata conducts research into the most invasive apps on the market
Stalkerware is a malicious piece of software designed to spy on individuals. The malware is installed onto a device without the owner’s knowledge or consent.
While you may think that this invasive software only exists in James Bond or Mission Impossible movies, this is not the case. The reality is that thousands of individuals (predominantly women) are unknown targets of this smartphone spyware. Sometimes, in an abusive relationship, the abuser will secretly install stalkerware onto their partner’s device to monitor them 24/7.
Unfortunately, this issue is becoming more prevalent with statistics showing that incidents of this nature have risen by a staggering 91% from 2018 to 2019.

The Coalition Against Stalkerware are an alliance of non-profit organisations and cyber security experts who work together to combat the issue of stalkerware. The coalition helps victims and survivors by raising public awareness of the issue, improving IT security training and providing support to advocacy groups.
The CAS define stalkerware as “software, made available directly to individuals, that enables a remote user to monitor the activities on another user’s device without that user’s consent and without explicit, persistent notification to that user in a manner that may facilitate intimate partner surveillance, harassment, abuse, stalking, and/or violence.”
As a member of the Coalition Against Stalkerware, the development team here at Corrata decided to do some research. We looked into some of the most popular stalkerware apps on the market and downloaded them onto a selection of test phones. This is what we discovered…
Experiment
Part 1: Downloading stalkerware
The first step in the experiment involved downloading a number of different stalkerware apps onto several test phones. The research team was able to see everything including calls, texts, social media messages, apps, photos, screenshots and GPS locations from a separate server. Some of the higher-end paid apps even recorded ambient audio. This allowed the team to listen in on conversations that were happening in the phone’s locality. In addition, the test phones gave little to no indication that the devices were under surveillance.
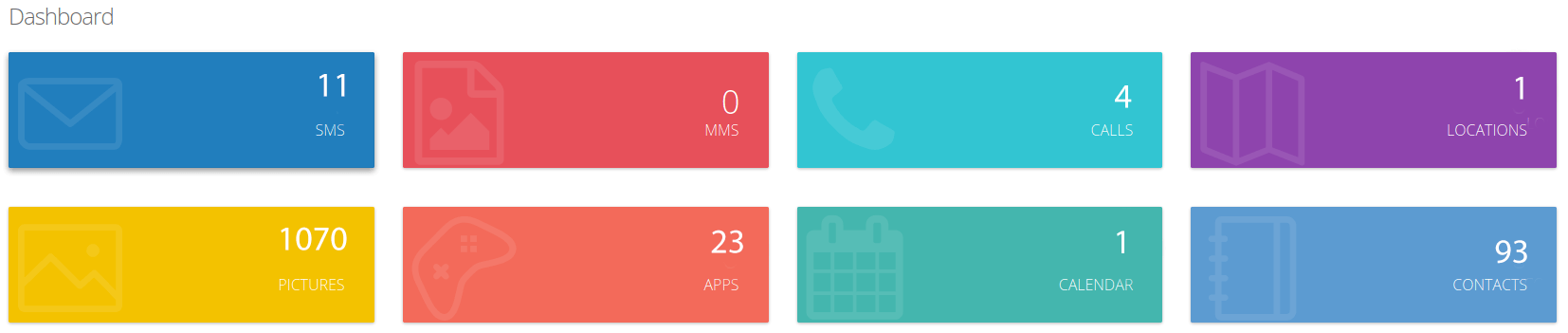
Dashboard Features: Access to SMS, photos, contacts, GPS location, calls and more
From conducting test SMS and WhatsApp conversations, the research team had access to the name of the sender, receiver, mobile number, date, address and text body.
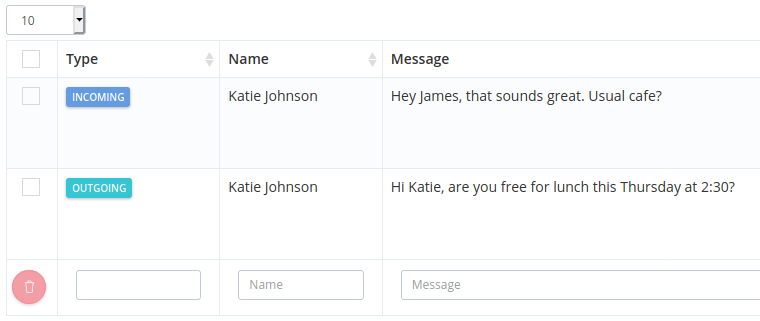
Test conversation visible from separate server
The team also had real-time visibility of web browser and app history. In summary, every element of the test phones were visible, highlighting just how prying these applications are.
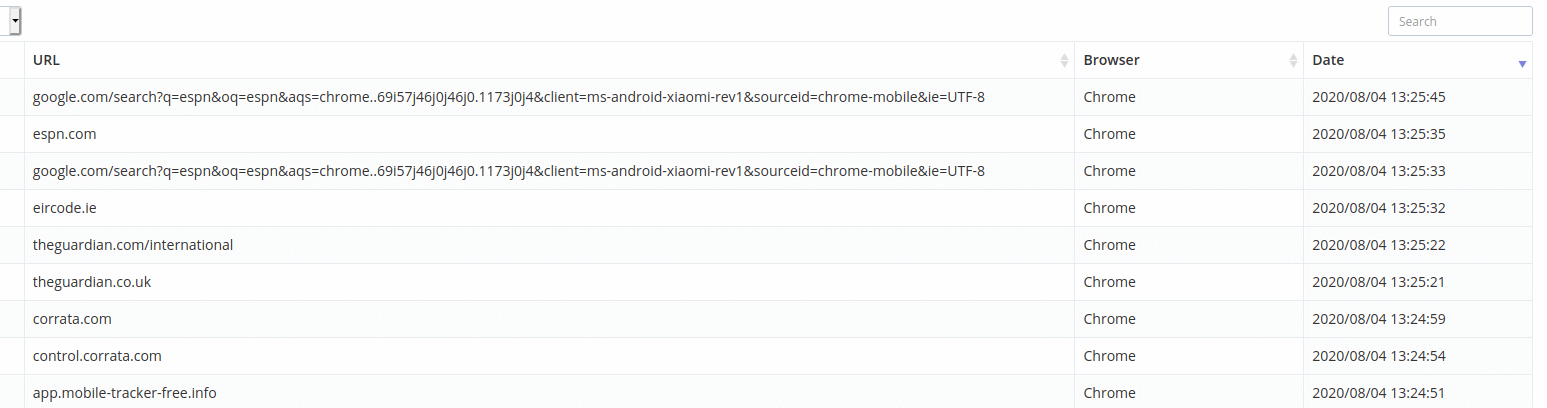
List of websites visited
Part 2: Stalkerware flying under the radar
The next step in the experiment involved testing five popular stalkerware apps against 80 URL categorization sites. These trusted platforms are designed to eliminate cyber fraud and protect web users. Alarmingly, only 2.5% of the platforms detected the apps as being malicious. The majority scanned the URLs as ‘clean’.
These results are concerning as thousands of businesses and individuals worldwide rely on these platforms for network filtering and mobile security. It is a well known fact that stalkerware sites market themselves as ‘parental control’ or ’employee monitoring’ software. Corrata advises that URL categorisation sites investigate and reevaluate their classification process.
Good app or bad app?
The first thing to note is that Stalkerware apps usually cannot be downloaded from the official app stores. These dodgy apps are normally downloaded directly from the website in question. During set up, these apps require users to turn off Google Play Protect and Google Play Store notifications. Following this, the software downloads an APK file onto the device.
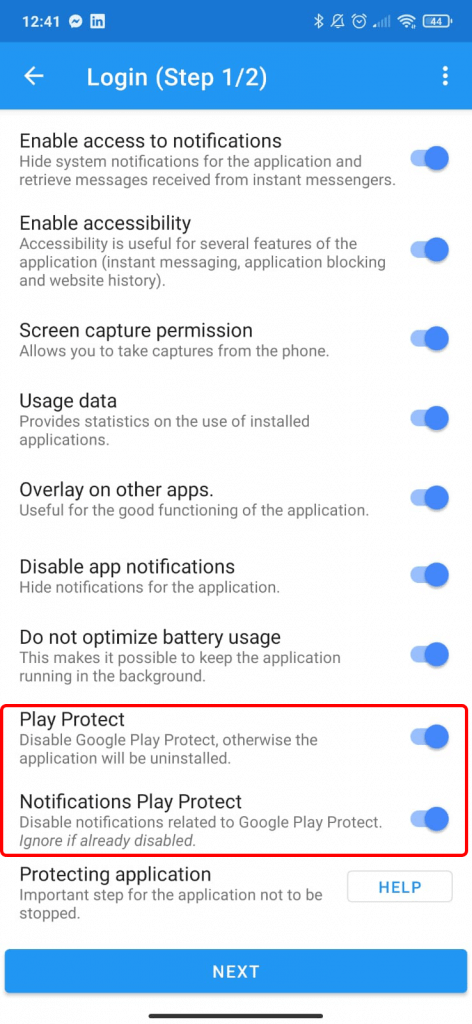
How can a victim tell if they are being spied on?
Stalkerware apps require access to device admin privileges. This is an extra level of permission which allows the app to wipe or locate the device and make the app more difficult to remove.
One way to determine if stalkerware is installed is to check device admin apps under settings. Typically, MDMs such as MobileIron and Airwatch appear here along with popular apps such as ‘Find My Device.’
However, if there is an app listed here that you don’t recognize, it could be stalkerware. For example, one particular stalkerware app appears as ‘Wi-Fi’ to avoid detection or suspicion. If users notice that Google Play Protect has been turned off, this could also be an indication of spyware.

Stalkerware app disguised as ‘Wi-Fi’
If you do suspect stalkerware is on your device, you should seek professional advice before uninstalling the app. In many cases, the software will alert the abuser if the app has been removed.
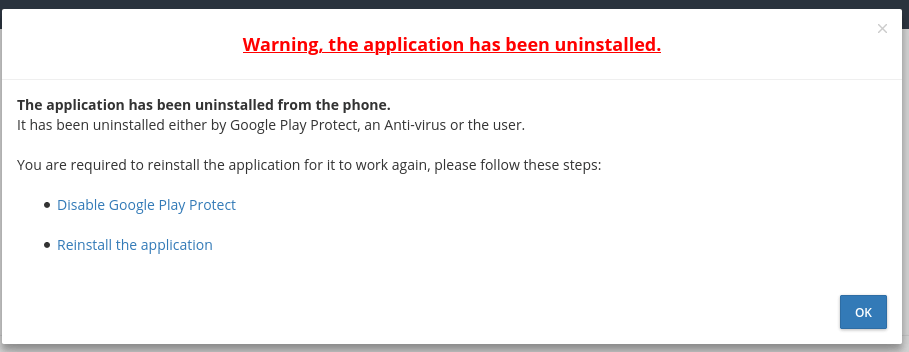
Abuser alerted of uninstallation
Going forward, cyber security firms need to unite and work together to tackle this growing problem. One encouraging example of this is Google announcing that from August 11 they will be banning all online advertising of stalkerware. Following this great announcement, Corrata look forward to working alongside our partners in the Coalition Against Stalkerware to help fight against this terrible menace.




