Advanced Detection and Response
Mobile threats matters
Mobile is not just about email anymore. Most if not all business applications are now accessible from your employees mobile devices. Increased risk means heightened threats.
0
Employees are 18x more likely to click on a phishing link via mobile
0
Known exploited vulnerabilities in iPhone OS in 2025
0
Of employees upload corporate data to unsanctioned AI Chatbots
0
54% of employee mobile devices have poor security configuration
Mobile security solved
Corrata provides market leading protection against mobile phishing, spyware and data loss. And it does this with a solution which is employee friendly, simple to deploy and easy to manage.
3x
Corrata is 3x more effective at blocking mobile phishing than our competitors
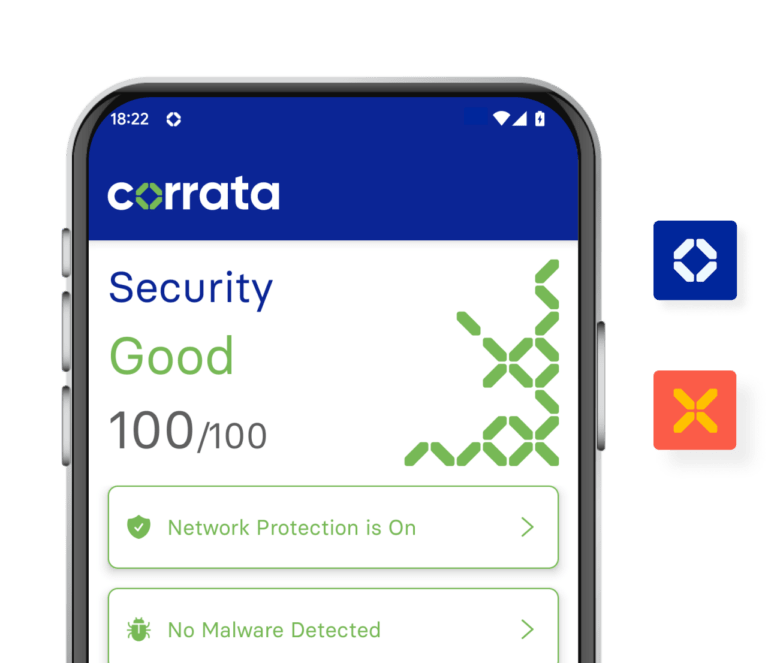
100/100
The security score achieved by over 95% of devices running Corrata
52%
Of employee phones encounter a malicious link in any 2 week period
1,000+
Average number of scans performed by Corrata per device per day
How Corrata helps
The CISO
Employees
The CIO
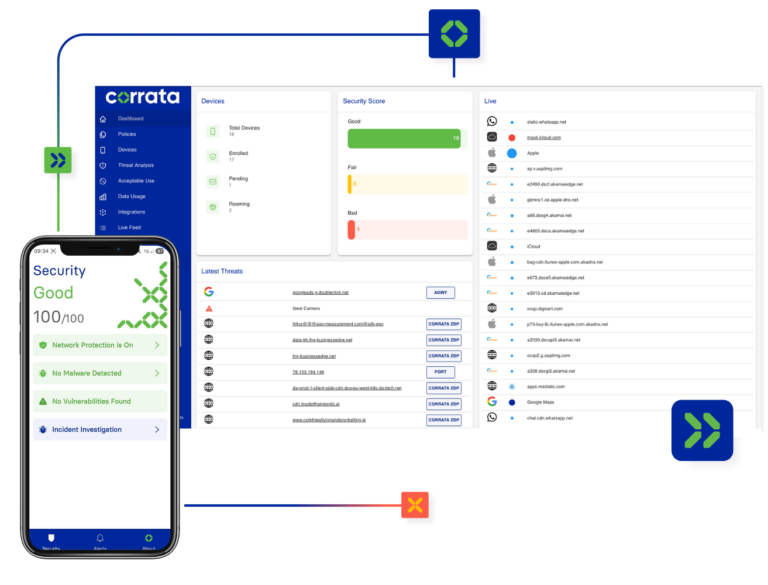
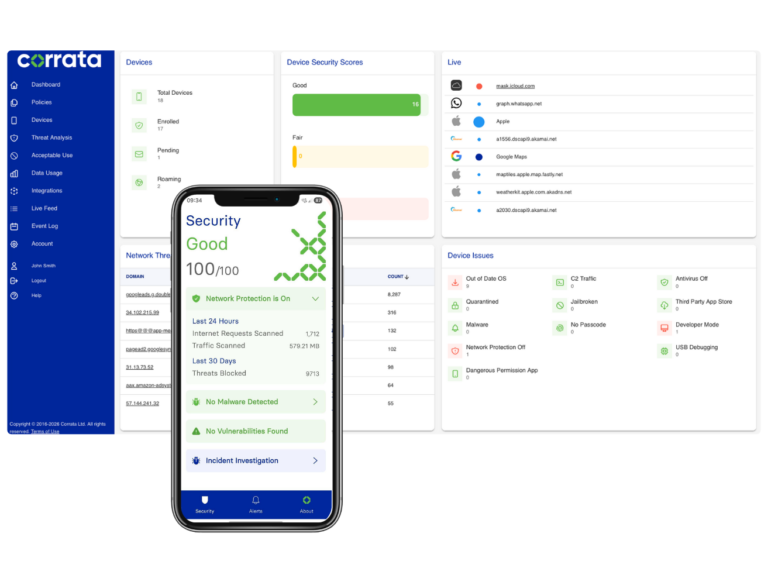
Corrata’s key capabilities
Corrata dramatically reduces the mobile risk by protecting your employees' devices across multiple dimensions.
Robust protection against mobile phishing and other malicious links
Corrata automatically scans all connection attempts to ensure they are safe. It combines industry threat feeds with specialized threat intelligence and detection techniques to ensure both a very high success rate with a very low rate of false positives.
Testing has shown Corrata to be 3x as effective as the competition.
Powerful malware detection and response
Corrata extends the state of the art for malware detection on mobile. By observing a wide range of indicators, Corrata is able to identify suspicious activity associated with potential infections even when there is nothing visible on the device. CnC traffic is disabled and infected devices are automatically isolated. In cases of advanced malware infection detailed diagnostic information can be collected from impacted devices.


Data Loss Prevention
Organizations need effective endpoint data loss prevention (DLP) to allow employees to safely embrace AI chatbots and use cloud services responsibly. Corrata protects against unauthorized data sharing from employee smartphones and tablets by enforcing policy at the device level. Access to unsanctioned services can be blocked, and previously unknown applications can be detected and addressed as required.
Effective vulnerability management
Corrata’s unique security score provides an easy to understand summary of the security stance for all your employee devices. Gamification and guided remediation encourages end-users to keep their devices up to date, fix poor configuration setting and remove potentially harmful applications. Quarantining is a powerful tool to isolate insecure devices and to encourage end-users to remediate.
Guide to Mobile Phishing
On mobile devices 85% of phishing attacks take
place outside email. Click the link below to learn
more about the mobile phishing threat.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management