Whitepapers
Read a selection of whitepapers and briefing notes for in-depth coverage of key topics in mobile endpoint security.
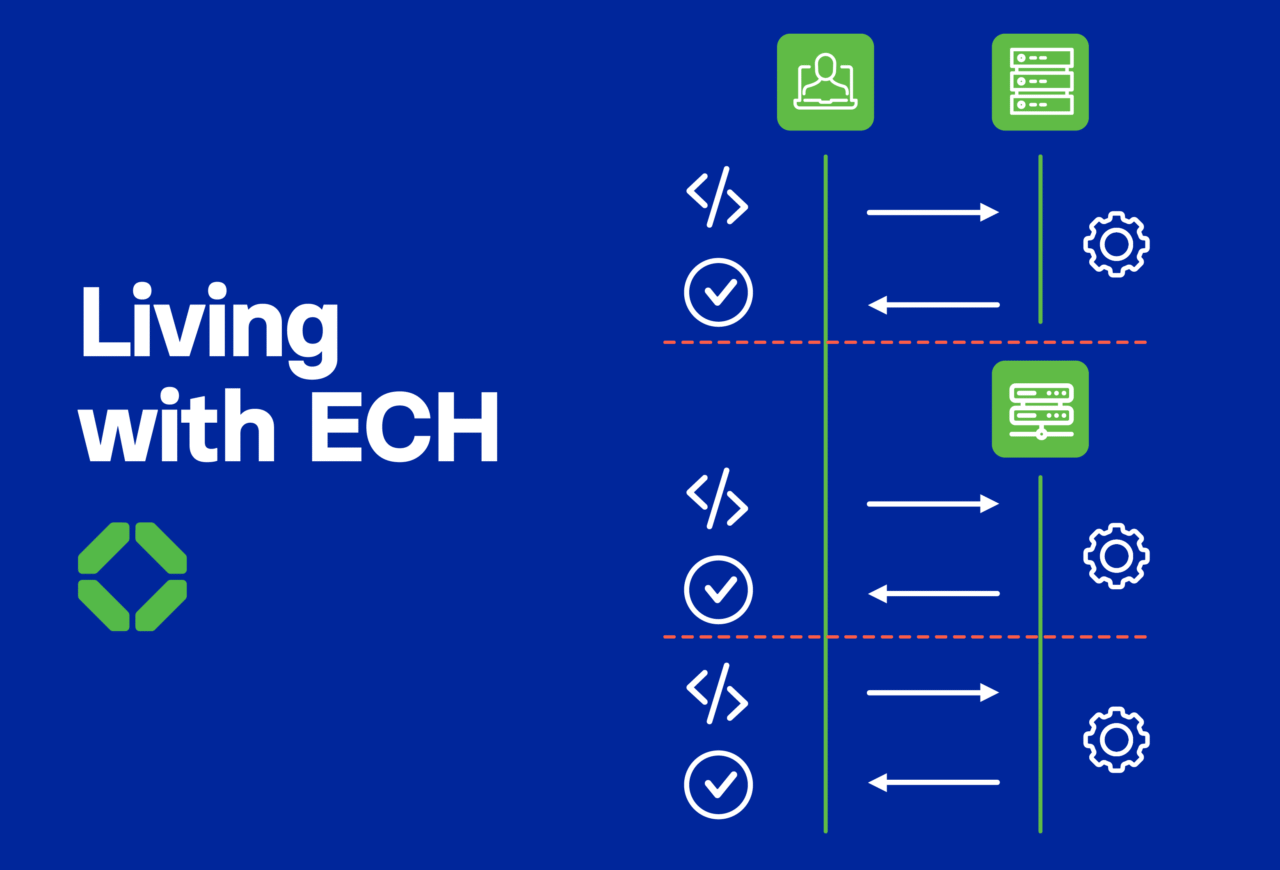
Featured Whitepaper
Living with ECH Read our report on the prospects for adoption of Encrypted Client Hello.
Read more -

-

-

-

reading time: 10 min
Dangerous Permissions – Location Tracking
One of the most insidious aspects of the mobile advertising ecosystem is how app vendors exploit end-user trust. Apps that...Download -
reading time:
Living with ECH
Read our report on the prospects for adoption of Encrypted Client Hello.Read more -

reading time: 10 min
Guide to Mobile Phishing
The growth in adoption of SaaS means that your organization's most critical information is now available on phones and tablets.Read more