Use Case
Vulnerability Management
A total of 773 iOS and Android vulnerabilities were patched in 2025. Keeping your devices up to date and replacing any that are obsolete is only the start. Poor security configuration can also leave your organization vulnerable.

Mobile devices running unpatched versions of Android or iOS leave you exposed to a wider range of threats than necessary. This includes risks from iOS vulnerabilities, Android vulnerabilities, iOS exploits, and Android exploits.
Sophisticated malware will take advantage of such devices, especially those with out of date Android versions or out of date iOS versions, to gain access to critical systems and steal enterprise data. Good device hygiene is table stakes, and this involves patching Android devices, patching iOS devices, keeping Android up to date, and keeping iOS up to date.

How Corrata reduces risk from insecure devices
Corrata’s approach to vulnerability management comes in three parts:
Real-time Monitoring: Corrata monitors the security status of devices in real-time, calculating a security score which provides a simple-to-understand summary of the devices’ security posture. This includes monitoring for iOS zero day and Android zero day vulnerabilities.
Isolation of Insecure Devices: Corrata provides an automated process to isolate insecure devices, especially those with mobile device vulnerabilities.
User Alerts: The Corrata App alerts the end user to any misconfigurations and provides a simple interface to remedy any issues identified, including guidance on addressing iOS vulnerability and Android vulnerability.
Automatic monitoring and remediation of Android & iOS vulnerabilities
-
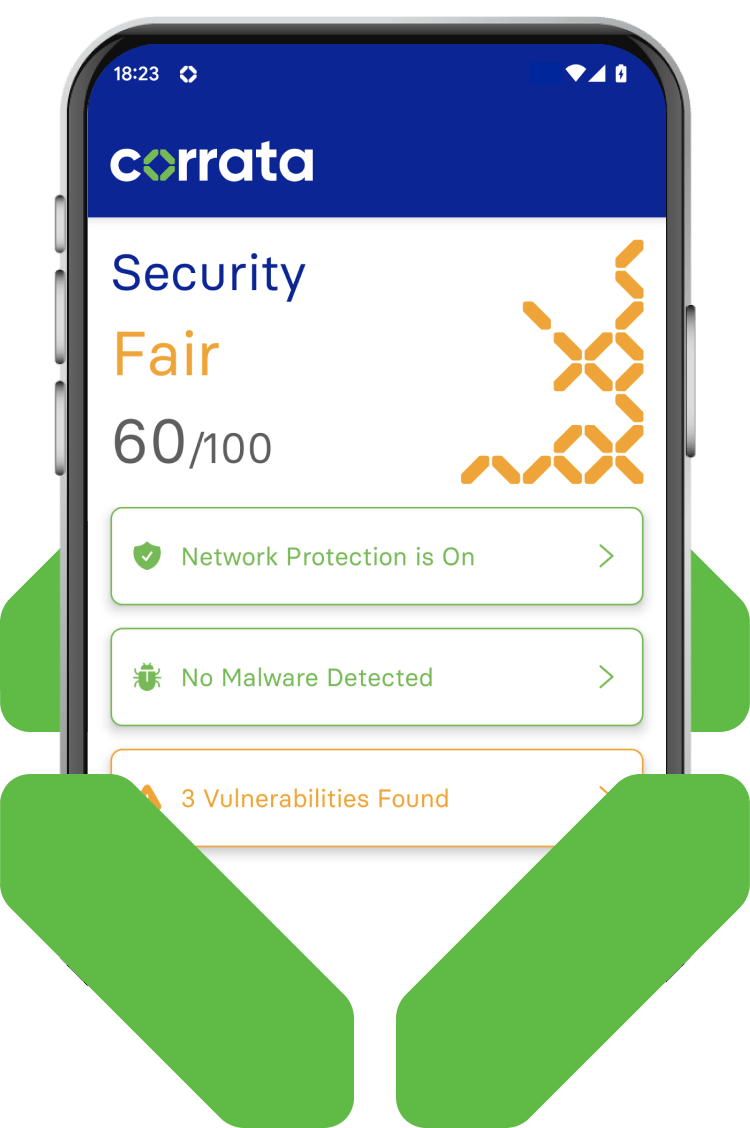
Establish individual device Security Score
At a glance understand the security posture of individual devices and your device fleet
Corrata’s unique security score gives you a simple to understand indicator of the health of each device. Ongoing monitoring of the key security indicators on the device enables an assessment of the vulnerability of the device to threats. Security score is based on a combination of operating system status, device configuration and malware status.
-
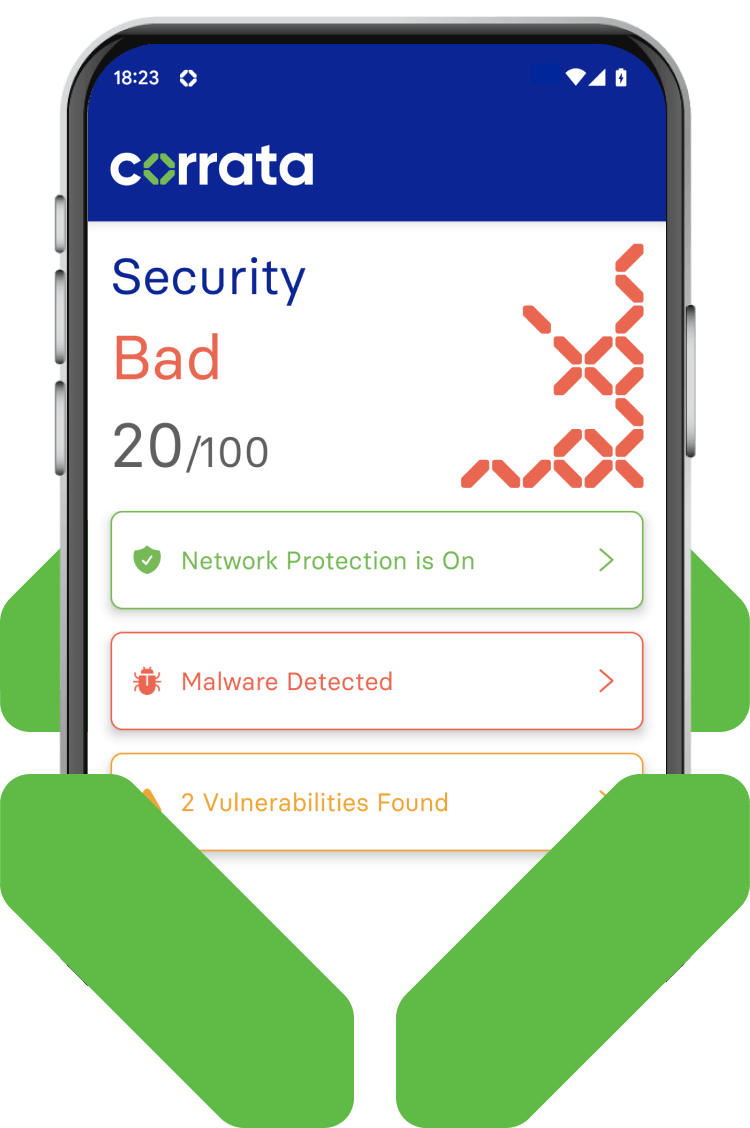
Isolate insecure devices
Devices below a specified threshold can be quarantined until vulnerabilities are addressed
By denying insecure devices access to business applications the impact of poor security configurations can be mitigated. When users update their devices and correct misconfigured settings, access to applications is re-enabled. As this is automated there is no requirement for IT Admin resources in managing this process.
-
Guided remediation
Making it easy for users to fix vulnerabilities
The Corrata App highlights poor security configurations for the user and guides them through the remediation process. Changing insecure settings, updating out of date operating systems and removing potentially harmful apps is made easy with an intuitive user interface.
-
Conditional access policies
Enabling a graduated response to device insecurities
Devices with insecure settings which are of low concern can continue to access lower risk applications while those with severe vulnerabilities can be completely isolated from the internet. Corrata can integrate with your Identity Provider to enable conditional access.
FAQ’s
The objective of vulnerability management is to reduce the risk of data breaches by fostering good security hygiene across the fleet of devices that employees use to access business applications. This starts by establishing the security posture of devices (are they running up to date software, do they have passcodes set etc.) and then making it easy for employees to remedy any insecurities found.
When Corrata is initially deployed, out of date operating systems and apps, malware, absence of passcodes, and disabled security settings are among the most frequently found vulnerabilities. In rare cases devices will be found to have been jailbroken or rooted.
Corrata scans the key security settings and establishes a security score for each employee device. The Corrata app provides employees with details of the factors driving the score and guided support in resolving any issues. Admins also have access to this score and can set rules which will quarantine devices with serious unresolved vulnerabilities.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management




