Use Case
Device Trust
Today mobiles have the same access to sensitive corporate information as traditional endpoints. This makes it essential to verify the security status of devices every time they attempt to access your environment.

MDM systems provide only superficial visibility and are incapable of detecting malware and other advanced threats. Even this limited insight is absent for the 72% of employee devices which are unmanaged.
Corrata provides 100% visibility into the security status of devices it protects, allowing organizations to grant access from both managed and unmanaged devices.

How Corrata protects your cloud environment
Identity Gate from Corrata is our unique approach to protecting cloud apps across both managed and unmanaged devices. Any employee device which is secure can safely access all of the apps needed to drive productivity and digital transformation.
Enabling safe access to your environment from any safe device
-
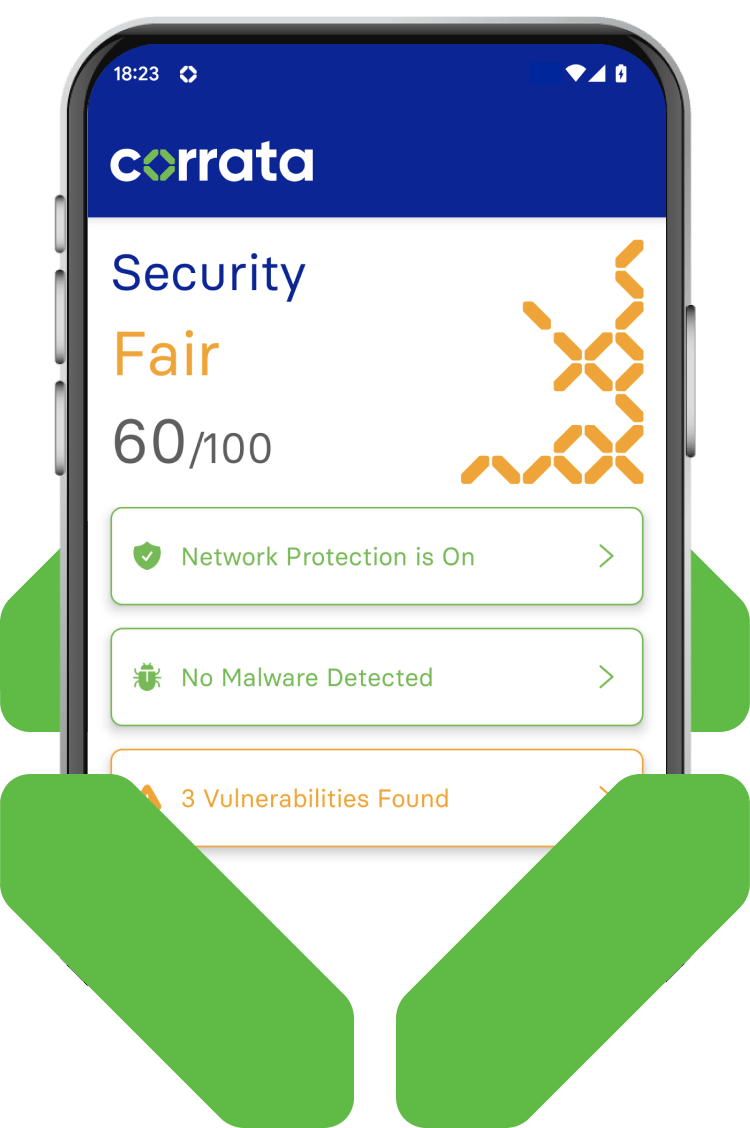
Device security status
Continuous monitoring of device security status
Corrata continuously monitors each individual device for evidence of malware infection, poor security hygenine, misconfiguration or other vulnerabilities. Employees are kept informed of any issues which require their attention.
-
Identity Gate
Allow authentication from any safe employee device
With Identity Gate organizations can safely extend access to enterprise apps to all secure employee devices regardless of whether they are managed or unmanaged. Identity Gate prevents devices which are unsafe or whose security status is unknown from accessing the enterprise environment.
-
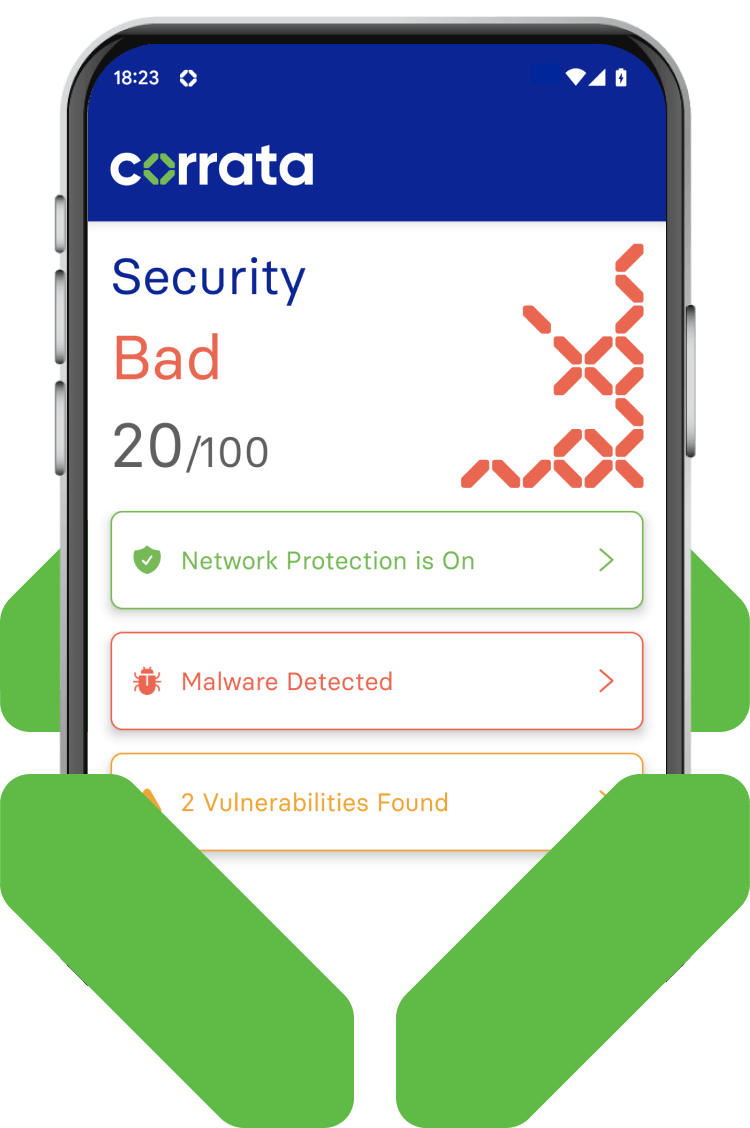
Device quarantine
Prevent data exfiltration instantaneously
When indicators of compromise are detected devices are instantaneously blocked from accessing enterprise apps. In the event of less severe security concerns a more nuanced approach can be used with access to less sensitive apps maintained.
-
Guided remediation
Employees are provided with easy steps to fix issues
When issues of concern are identified, employees are alerted and provided with the help needed to address them. The Corrata App provides an easy to understand summary of any vulnerabilities or misconfigurations.
FAQ’s
Every time an employee connects to your environment you need to answer two questions. The first is whether you can trust that the user is who they claim to be, the second is whether the device they’re using is safe. The second step is referred to as ‘device trust’ and is provided by security software running on the endpoint.
Unlike Windows machines, neither iOS or Android devices routinely share a unique identifier when they connect to an app or service. This means you cannot match up signals from a security app running on the device with the access attempt. MDM addresses this gap through the MDM Identifier, though this feature can be complex to leverage for conditional access. Unmanaged devices have no mechanism for sharing their identity with an application.
Without a reliable way of establishing Device Trust organizations have the choice of either blocking access from mobile devices or tolerating an untreated risk. Using Identity Gate organizations can apply a policy of accepting access requests from an employee using any devices conditional on that device being verified as secure at the exact instant of the login attempt.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management





