Use Case
Dangerous Applications
219,635 apps were delisted by Google and Apple in Q1 2022 alone. Its not just operating system vulnerabilities that put your data at risk. Mobile applications can contain flaws which leave your data exposed. Malware distribution is often facilitated by ostensibly legitimate apps. Apps present a variety of risks to enterprises.

Malicious apps can obtain access to powerful device features and data. Out of date apps can include unpatched vulnerabilities.
And downloading apps from outside official app stores can lead to the installation of fake versions of legitimate services.

How Corrata reduces risk from malicious mobile apps
Corrata provides a number of features which address app risk. Apps which seek user permission to access functions which are not acceptable from a security perspective are identified as are apps with known high severity vulnerabilities. Corrata protects such apps from causing harm through features such as blocking CnC traffic and quarantining low trust devices.
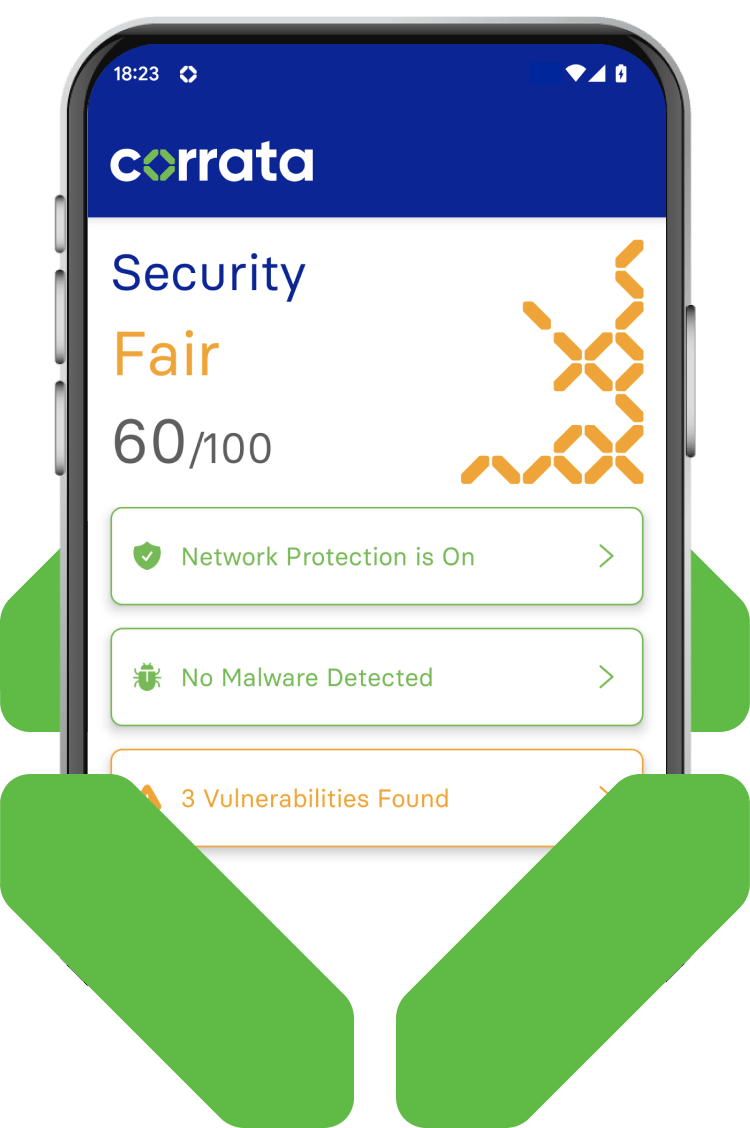
Preventing harm from dangerous apps
-
Dangerous permissions
Highlighting apps where users have given consents which are open to abuse
Malicious apps take advantage of users’ willingness to grant consent to access powerful device functions such as accessibility features, location or file storage. Corrata addresses this risk by highlighting any such occurrences and offering the potential to impose automatic restrictions on impacted devices.
-
Potentially harmful apps
Any apps which represent a threat to enterprise data are prevented from operating
Corrata monitors the apps on every device to identify any that are known to cause harm. In addition to highlighting such apps to Info Sec staff and employees, Corrata’s ability to block CnC traffic is used to prevent such apps exfiltrating data.
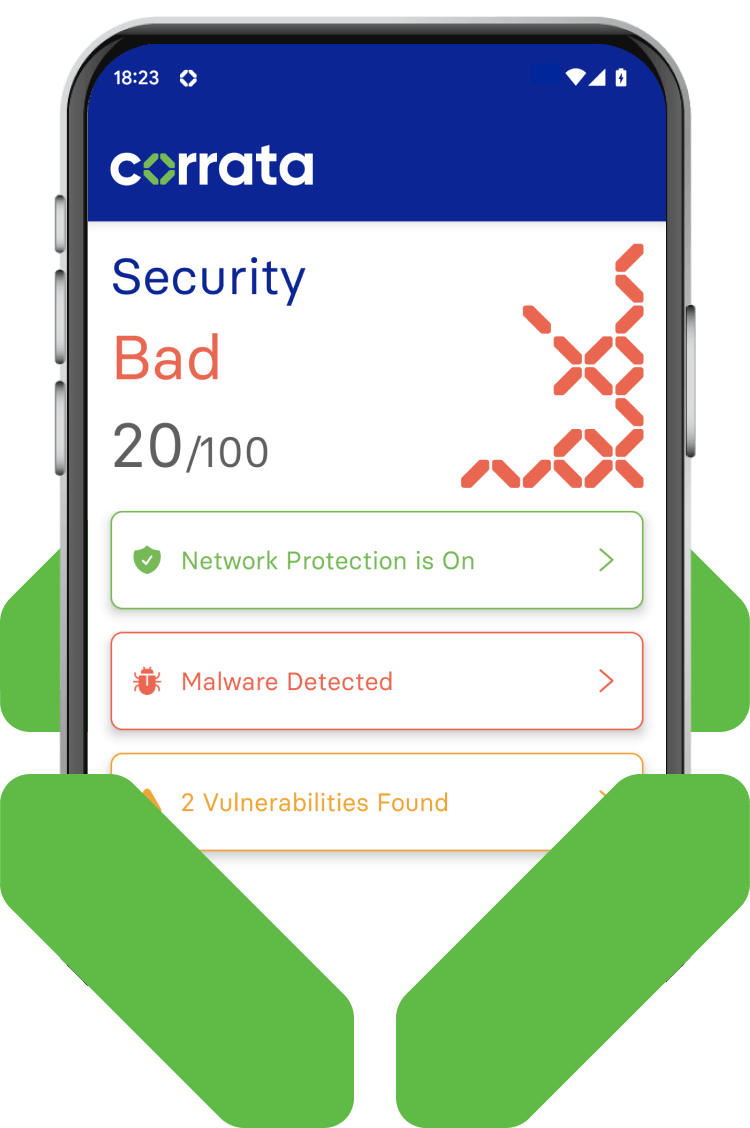
-
Apps with known vulnerabilities
Out of date versions of popular apps can contain dangerous vulnerabilities
Developers of popular apps are generally diligent in addressing any security vulnerabilities through the release of patched versions. However app store distribution cannot guarantee that users will upgrade to the new safe version. Corrata highlights apps with known high severity vulnerabilities.
-
App Catalogue
Ensure that employees download the legitimate version of your enterprise apps
Today, more and more enterprise applications are available on mobile. Corrata provides an App Catalogue as part of the Corrata client to simplify distribution of these apps to end user devices (particularly BYOD) and to avoid the real risk that users are tricked into downloading fake versions from outside the app store.
FAQ’s
Dangerous applications are those, while otherwise legitimate, that contain flaws or request permissions that might put your organization at risk. For instance, an out-of-date application may have an unpatched vulnerability which leaves it open to being exploited. Another concern is apps requesting sensitive permissions like location tracking or accessibility permission, which attackers can exploit.
Corrata identifies and highlights these dangerous apps both to end users and admins. This allows the organization to make informed decisions about the risk associated with the application.
Corrata provides a range of features including alerting, blocking and quarantining which can be used to address the risk associated with risky applications.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management





