Use Case
Combatting Spyware
Corrata empowers organisations to stay ahead of nation-state adversaries by delivering proactive protection where current tools fall short. With continuous IOC monitoring, remote forensic capability, and rapid containment, Corrata closes the gaps that attackers exploit - ensuring that executives and critical operations remain secure.

Nation-state adversaries target key executives in energy, communications, and infrastructure, exploiting zero-days to steal intellectual property and sensitive data - turning mobile devices into gateways for espionage and corporate compromise.
Current tooling leaves critical gaps: attacks are only revealed after Apple or Google warnings, by which time sensitive data may already be compromised, and traditional forensic investigations cannot be executed remotely, leaving security teams blind.

How Corrata protects against spyware
Corrata empowers organisations to stay ahead of nation-state adversaries by delivering proactive protection where current tools fall short. With continuous IOC monitoring, remote forensic capability, and rapid containment, Corrata closes the gaps that attackers exploit – ensuring that executives and critical operations remain secure.
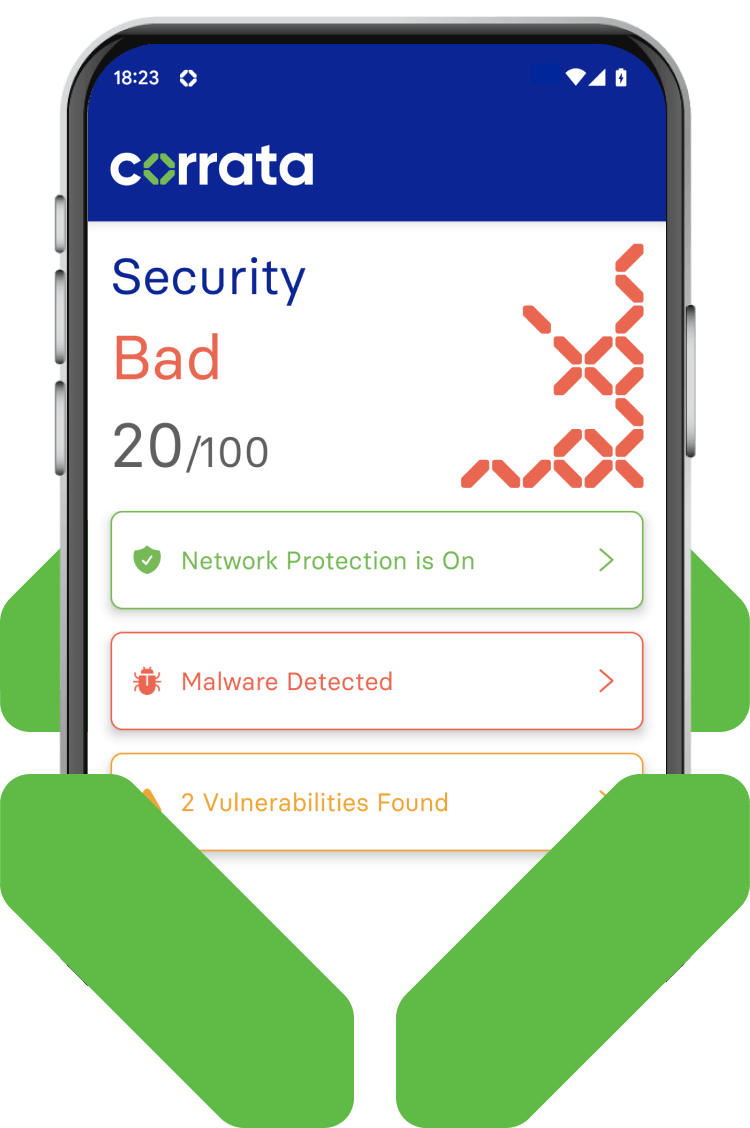
Advanced spyware detection and response
-
Continuous On-Device Monitoring
Corrata constantly monitors device settings and network activity for spyware indicators.
Running directly on the device, Corrata continuously analyses traffic patterns, configuration changes, and unusual behaviors. This persistent monitoring ensures that potential spyware activity is identified in real time rather than after significant harm.
-
Detection of Sophisticated Threat Indicators
Corrata identifies subtle, high-risk anomalies missed by traditional methods.
The system detects indicators such as traffic over rarely used ports, connections to risky IP addresses, or abnormal data transfers. These nuanced signals provide early warning of sophisticated spyware, improving detection speed and accuracy.
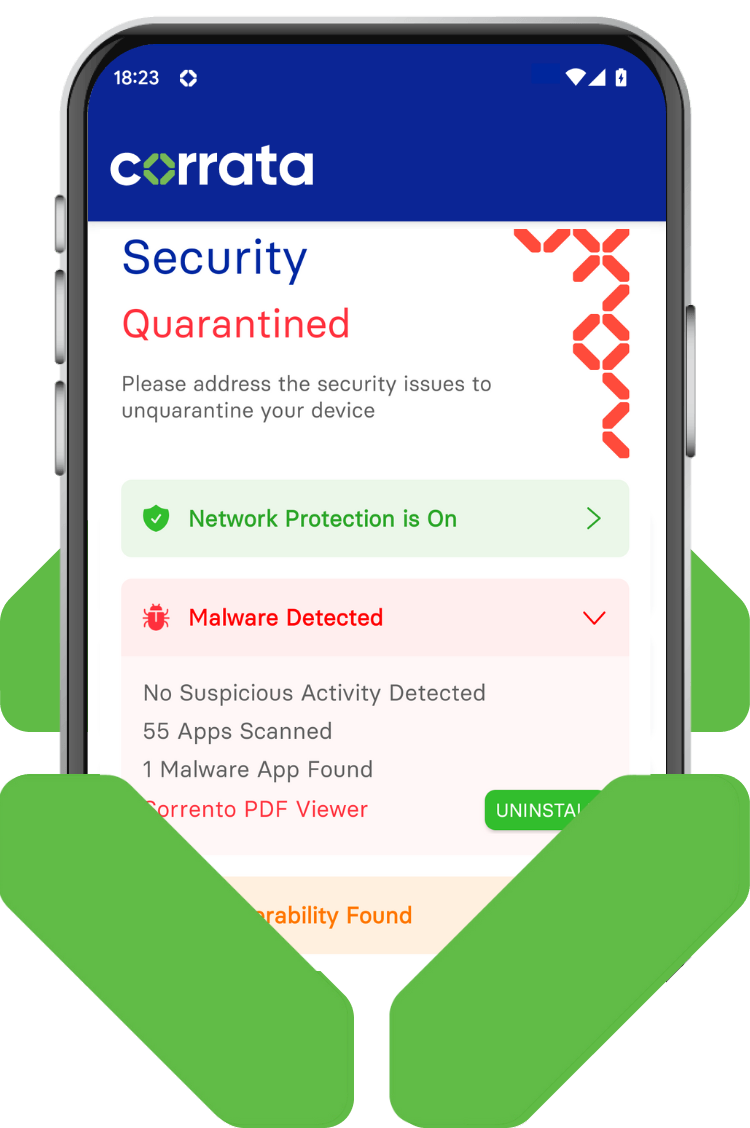
-
Empowered End-User Response
Users can securely gather and share forensic data when threats are suspected.
When suspicious activity is flagged, Corrata enables end users to easily collect diagnostics and forward them to analysts. This streamlined process accelerates investigations while removing the complexity and burden of traditional manual forensic scans.
-
Secure Isolation During Investigation
Compromised devices can be isolated to prevent further organisational harm.
While analysts review collected data, Corrata can automatically quarantine the affected device from sensitive systems. This containment step protects the wider organisation while ensuring the user experiences minimal disruption to their normal device activities.
FAQ’s
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Malware Detection
Device Trust
AiTM Protection
Vulnerability management
Web filtering





