Use Case
Spyware Detection
Sophisticated spyware exploits zero-day vulnerabilities to deliver zero-click attacks targeting employees and their colleagues working in critical or sensitive sectors. Less sophisticated malware in used in a wide variety of social engineering attacks
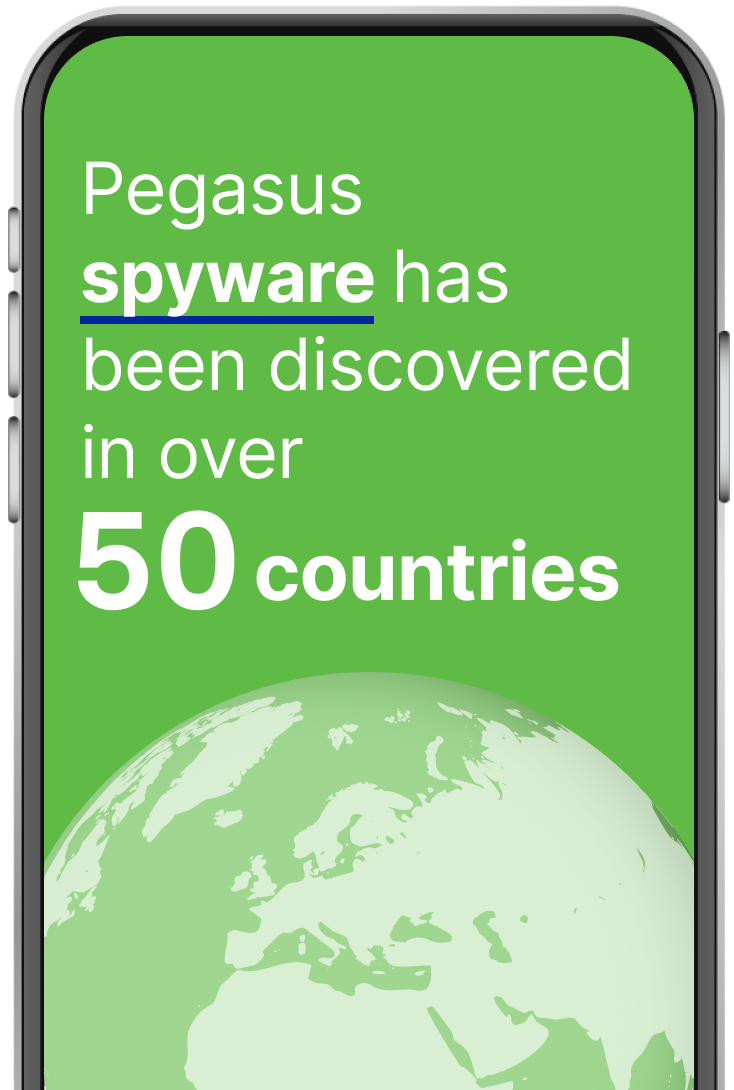
Built-in security protections have proven powerless against sophisticated spyware like Pegasus, Graphite and Predator. Even routine malware can be destructive, tricking users into revealing critical information.
Even routine malware can be destructive, tricking users into revealing critical information.

How Corrata protects against malware
Corrata defends against malware in multiple ways. By blocking access to malware download servers it reduces the opportunity for infection. By scanning devices and network traffic for anomalies it can remotely detect even stealthy attacks. And by quarantining impacted devices it limits the damage that malware can cause.
Advanced spyware detection and response
-
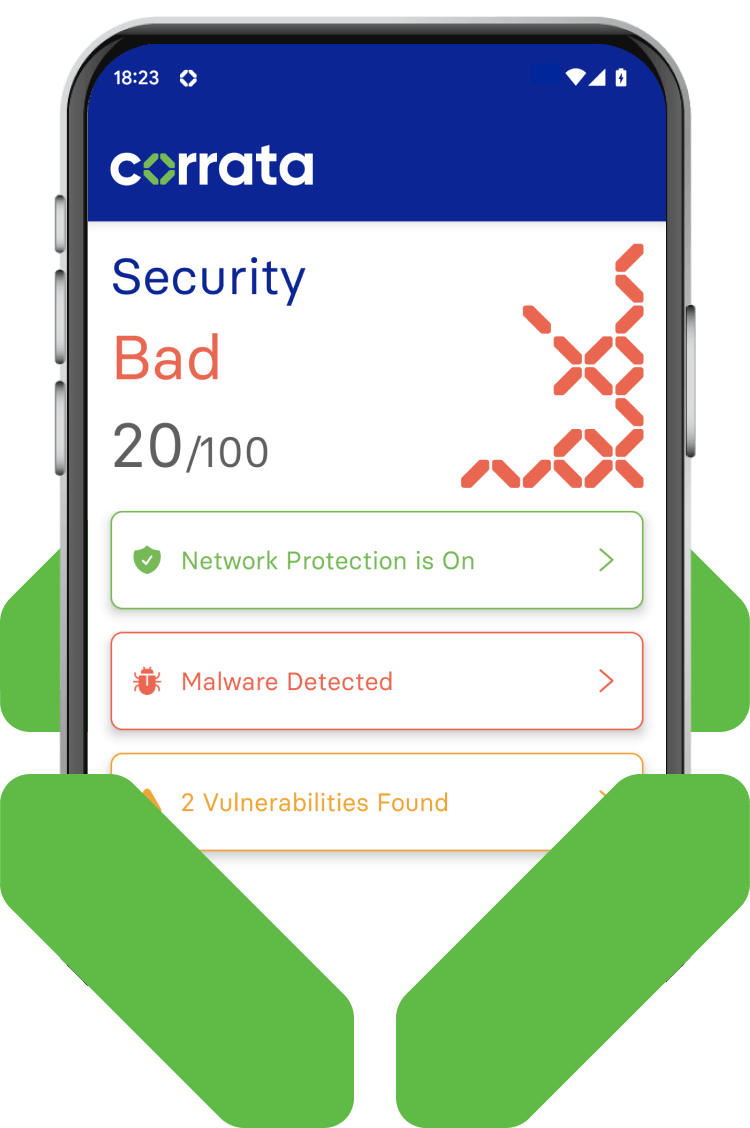
Advanced malware detection
Pegasus, Predator and other advanced malware require sophisticated Android and iOS malware detection techniques.
Corrata is unique in offering a solution that is capable of continuously monitoring for the anomalies in device behaviour which spyware causes.
-
Incident investigation
When suspected spyware related anomalies are detected Corrata offers the necessary tooling for incident investigation and response.
End-users can generate and submit device diagnostic files and packet captures. This files are vital to confirming infection and understand spyware operation.
-
Quarantining
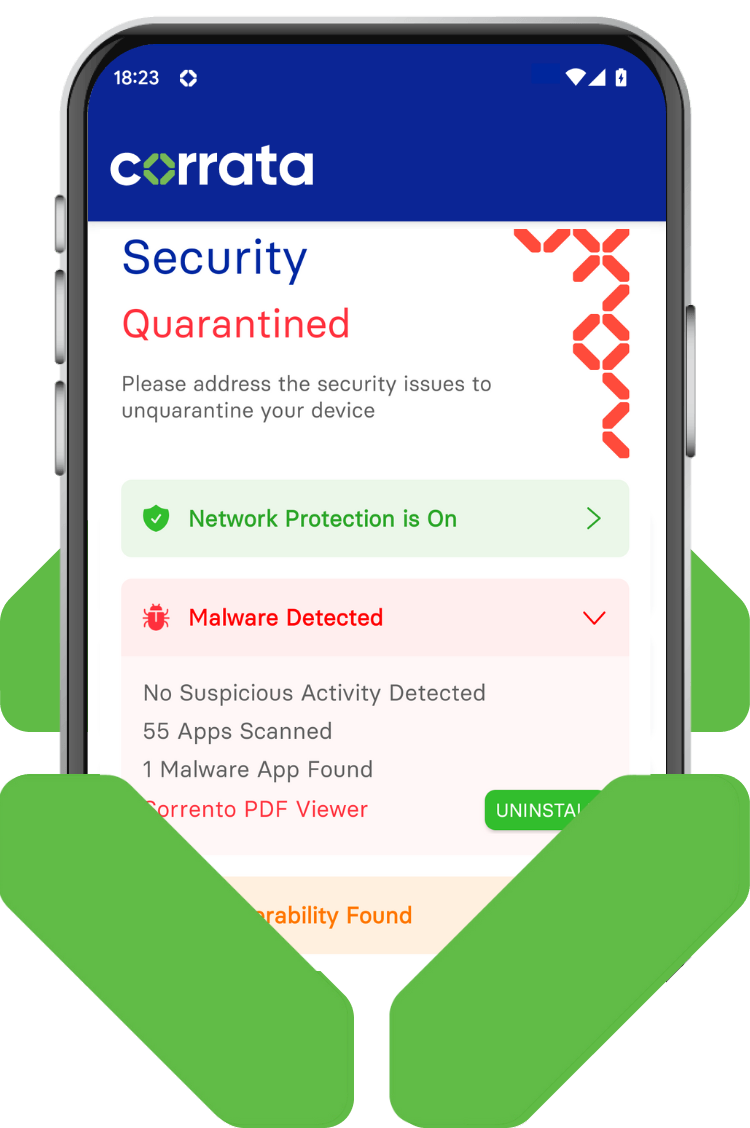
Automatic quarantining of devices is an effective response to malware discovery.
Once infections are identified Corrata provides a protective cordon around the impacted device to ensure that it no longer has access to sensitive corporate data.
-
Preventing routine malware infections
Social engineering is used to trick employees into downloading fake apps and granting dangerous permissions.
Corrata blocks access to malware download sites, prevents malware installation and monitors for apps which use dangerous permissions.
-
Removal of risky apps
The Corrata app prompts users to remove apps which are identified as risky
The Corrata app prompts users to remove apps which are identified as risky.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management





