Use Case
Adversary-in-the-Middle (AitM) Protection
40.5% of websites have inadequate encryption. Today with most corporate applications accessible on mobile we rely on Transport Layer Security (tls) to ensure confidentiality and integrity.
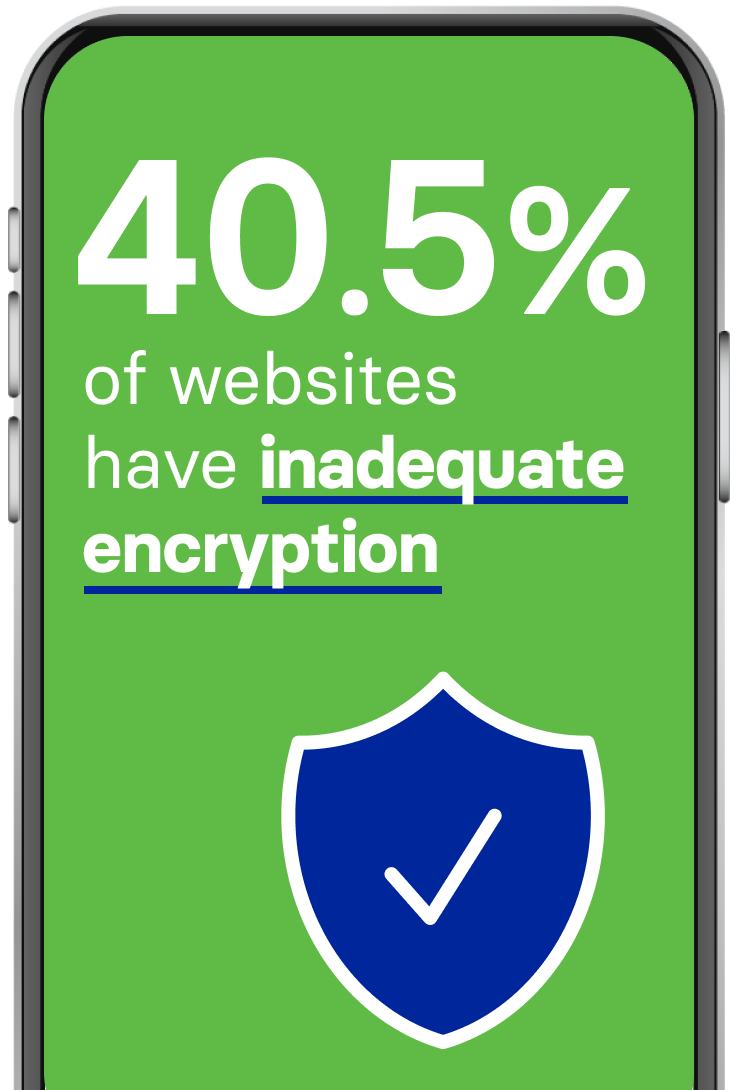
However, due to poor implementations and the activities of determined hackers, this reliance is not always safe. Public networks, including cellular, Wi-Fi, and broadband, are all susceptible to interception by Adversary in the Middle attacks.
Hackers have multiple opportunities to monitor your communications and to redirect your traffic to locations they control, making AITM protection essential. Today, the only coherent approach is one based on zero-trust.

How Corrata Protects Against Adversary-in-the-Middle Attacks
Corrata uses a variety of techniques to monitor the security of data mobile devices transmit. By examining indicators such as cipher suites, protocol versions, and TLS certificates, Corrata is able to identify rogue hotspots and other cases where communications are vulnerable to hackers and ensure that sensitive data is not transmitted when at risk of interception.
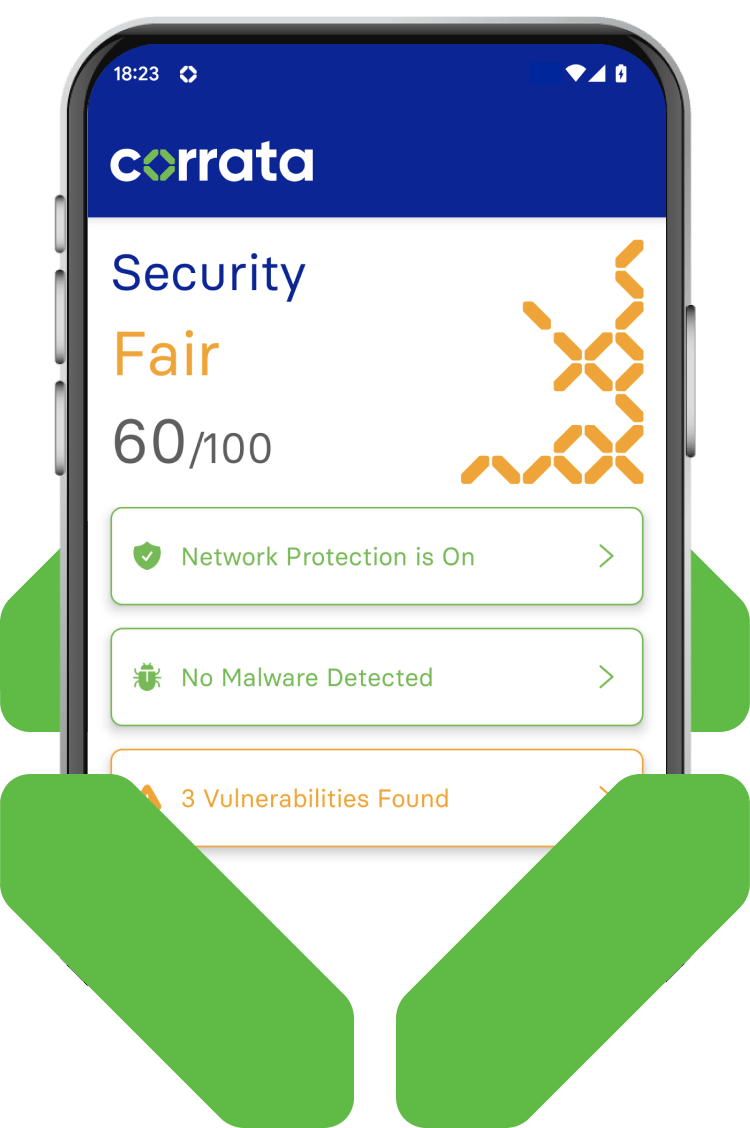
Advanced Network Protection For Your Mobile Communications
-
Countering Adversary-in-the-Middle Attacks
A series of measures which prevent bad actors intercepting sensitive communications
Corrata starts from the assumption that the safety of network infrastructure, including cell towers and Wi-Fi hotspots, can never be accurately assessed. Instead Corrata monitors the quality and integrity of Transport Layer Security, preventing the transmission of data where vulnerabilities are identified
-
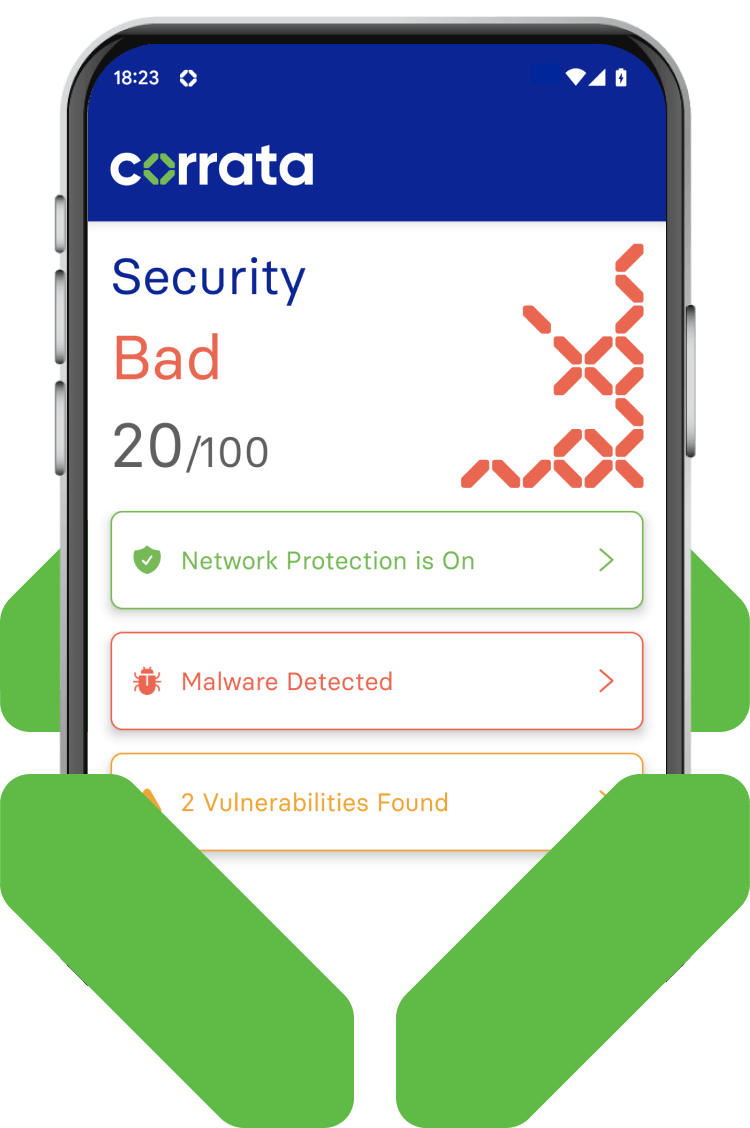
Checking the quality of encryption
The use of out-of-data cipher suites leaves traffic vulnerable to snooping and Wifi eavesdropping.
Corrata continuously monitors the quality of encryption offered by applications and websites to ensure it cannot be compromised by Wifi Hacks. Traffic to applications or websites offering poor encryption can be automatically blocked.
-
Enforcing cert pinning for sensitive applications
Threat actors can easily trick end users into trusting servers they control using fake certificates.
Certificate pinning is a powerful technique to prevent devices from being mislead into trusting malicious websites, applications or APIs. Corrata offers the ability to extend cert pinning to any sensitive domain whether accessed via an app or a browser.
-
Preventing transmission of data in the clear
Posting data to a server without encryption should never be permitted
Corrata identifies attempts to send data ‘in the clear’ for storage. This prevents such data in transit from being captured by bad actors. It also allows Corrata to identify activity which may indicate malware infection.
FAQ’s
Mobile devices are used predominantly over public networks whether they are cellular, Wi-Fi or fixed. Because these networks are public they can be accessed by bad actors using a range of techniques to intercept and manipulate IP traffic. Internet users rely on the integrity of Transport Layer Security (tls) and SSL Certificates to secure their communications, but poor implementation by 3rd parties can lead to compromise.
There are a number of features of Wi-Fi that make it easier to hack. Your traffic can be observed while travelling over the radio waves. Hotspots can be faked or compromised. However many of the techniques used to interfere with traffic on Wi-Fi can also be used on fixed networks.
Corrata uses its position sitting between applications and the network to examine the quality of encryption (or its absence). It examines the tls implementation details and the SSL Certificates to identify weaknesses and prevents the transmission of sensitive data in circumstances where it may be hacked.
We’re on a mission
We’re here to stop every existing and emerging threat to your mobile workforce and business. Explore our Use Cases to find out more about the powerful and proactive protection we provide.
Mobile Phishing
Spyware Detection
Data Loss Prevention
Device Trust
AiTM Protection
Vulnerability Management




