TLS – Trust the Lock, Not the Road.

Transport Layer Security (TLS) is the backbone of secure communication on the modern Internet.
Over the years, TLS has evolved significantly, improving performance, tightening security and simplifying configuration. But while the protocol itself has improved, many of our assumptions about how and why we use TLS remain outdated.
There’s still a widespread belief that the safety of a connection depends on the network you’re using – that a coffee shop Wi-Fi or a public hotspot is risky, but your corporate VPN or home broadband is inherently trustworthy. This assumption is not only outdated – it’s dangerous.
We’ve all been told to watch out for “the guy in the hoodie” at the café spoofing a Wi-Fi network. But the real threat often lies much deeper: in the infrastructure itself. The routers, switches, telecom routes, and even undersea cables that move our data have been compromised time and time again – often at the state or enterprise level.
Consider some examples:
- NSA’s QUANTUM and TURBINE programs, revealed by Edward Snowden, tapped into backbone routers and silently injected malicious payloads mid-flight.
- NSO Group’s Pegasus spyware leveraged network injection over rogue telecom infrastructure, often using compromised routers and middleboxes.
- Cisco and Juniper zero-day vulnerabilities exposed core routing hardware to silent compromise and surveillance.
These aren’t rogue actors on public Wi-Fi. These are trusted, critical components of the global internet infrastructure being quietly turned against users.
The locked briefcase
Picture this: you’re sending sensitive documents across a city in a courier van. That van may pass through unsafe neighbourhoods, take detours, or even be briefly stopped and inspected – but it doesn’t matter, because your documents are in a locked briefcase, one only the recipient can open.
TLS is that locked briefcase. It doesn’t matter what path your data takes – it could go through your home Wi-Fi, a rogue router in a telco, or even a nation-state-controlled exchange point. With properly configured TLS, the message stays sealed.
TLS doesn’t just rely on “strong encryption” in a vague sense – it enforces several well-established principles that make it trustworthy, even when everything else isn’t. At the heart of TLS is ephemeral key exchange, most commonly using Elliptic Curve Diffie-Hellman (ECDHE). This means the client and server each generate temporary, one-time keys during the handshake – allowing them to derive a shared secret without ever sending the secret itself across the network. It’s like agreeing on a combination lock in separate rooms without shouting the numbers through the door. And since a brand-new lock is used every time, even if someone later steals your old keys, they can’t open yesterday’s box – that’s Perfect Forward Secrecy.
TLS also authenticates the server using X.509 certificates, issued by trusted Certificate Authorities (CAs). These are the digital equivalent of checking a passport before unlocking your side of the connection. Some systems go further by implementing certificate pinning, which tells clients to only trust specific public keys, guarding against mis-issued or rogue certs.
In TLS 1.3, many legacy algorithms and insecure options have been eliminated altogether – there’s no RSA key exchange, no static secrets, no downgrade paths to weak ciphers like RC4 or 3DES. Even the handshake itself is mostly encrypted, reducing metadata exposure.
State of the Nation
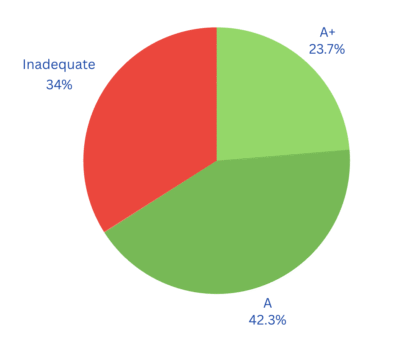
A recent scan in May 2024 by Qualys SSL Labs evaluated 134,495 secure websites. The results were mostly encouraging: 66.0% of sites received an A- grade or higher – considered secure by modern standards. However, 34% – or 45,693 sites – were graded below that threshold:
- 32.1% scored a B (minor weaknesses),
- 1% scored C (moderate risk),
- 0.9% received an F (high-risk configuration).
Thankfully, browser vendors have raised the floor for users. By now, all major browsers – Chrome, Firefox, Safari, and Edge – have fully deprecated TLS 1.0 and 1.1: Chrome and Firefox disabled them in 2020. Safari and Edge followed shortly after, with Apple fully deprecating them across its ecosystem in 2021. As of 2025:
- TLS 1.2 is the minimum version browsers will negotiate.
- The weakest fallback cipher still in play would be similar to:
- TLS_ECDHE_RSA_WITH_AES_128_CBC_SHA – a secure, but older, suite with 128-bit AES in CBC mode.
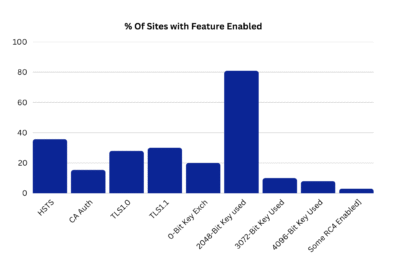
Browsers no longer tolerate truly weak configurations. If your server only supports deprecated ciphers, users simply won’t connect.
High quality TLS is not optional
The internet isn’t unsafe because of rogue cafés or sketchy Wi-Fi – it’s unsafe because the very infrastructure we rely on has proven untrustworthy time and again. From compromised telcos to nation-state surveillance implants, there is no safe path – only secure payloads.
That’s why TLS matters. Not just on public networks, but always. TLS 1.3, and strong configurations of TLS 1.2, ensure that even if someone owns the wire, they can’t read the message. So if you’re an organisation building apps, running servers, or managing mobile devices – don’t treat TLS as optional. Treat it as your armoured truck, locked briefcase, and diplomatic pouch – because the road is anything but safe.




