Stealing secrets – the menace of mobile RAT’s

Smartphones infected with Remote Access Trojans are a critical risk for enterprise security
Remote Access Trojans (RATs) have plagued Android devices for many years. These pieces of malware are disguised within seemingly benign applications, granting attackers remote access to a device. Essentially, this software allows attackers to manipulate a phone as if they had physical access to it.
The damage from remote access to an employee’s smartphone is significant. Most employees access a wide range of enterprise applications directly from their smartphones, including productivity suites like Microsoft 365 and Google Workspace, SaaS apps like Salesforce and Workday, and various line-of-business applications. Successful authentication to these apps often means credentials and MFA challenges are not subsequently required. This reliance on physical security and passcodes to safeguard enterprise data becomes a vulnerability when a RAT is involved, exposing all data previously only accessible with physical access to an unlocked phone.
Most enterprise access on mobile devices occurs through apps rather than browsers, which has important security implications. Apps typically use tokens to manage access, while browsers use cookies. Tokens are often configured so that end users never need to re-authenticate, even with SSO and identity providers like Okta or Entra (Azure Active Directory). In contrast, session cookies usually expire within days or weeks, requiring re-authentication. The use of tokens means attackers can be confident that access to an application will persist, greatly increasing the likelihood of exfiltrating sensitive data.
At first glance, RATs might seem like a remote risk. How could such devastating software end up on an employee’s phone? And surely the built-in protections of the mobile operating system would prevent such malware from doing harm?
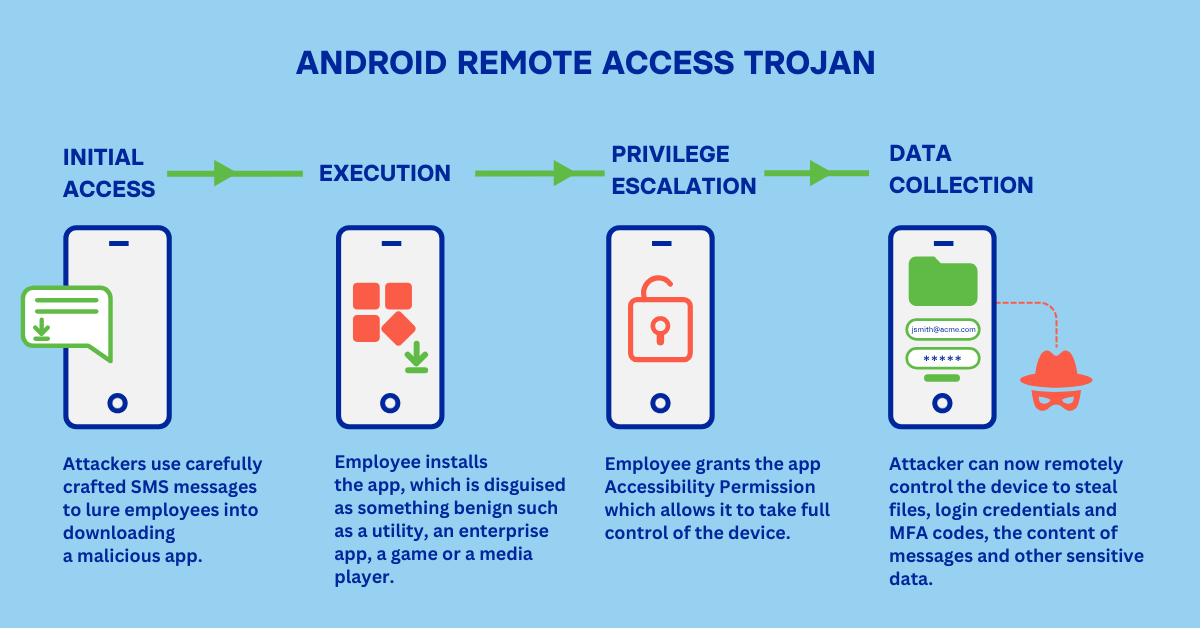
Steps in RAT Attack
Initial Access
Cybercriminals are adept at tricking people into doing the wrong thing. They might promise early access to a new movie, concert tickets, a hot deal, or an exciting new crypto scheme. Alternatively, they might create urgency around avoiding being locked out of a bank account, being cut off by a mobile or broadband provider, or being blocked from work accounts. They often leverage critical incidents like the Crowdstrike outage or impending natural disasters. Recently, attackers have used QR codes embedded in emails or posted in public places where employees gather. These lures can be delivered via multiple channels: SMS, WhatsApp, LinkedIn, or email. No matter how well-trained staff are, some percentage will always fall victim.
Execution
The crudest form of malware delivery is via unapproved app stores or download sites. Here, the operating system might warn users to avoid downloading from ‘unknown sources,’ and Google’s built-in Play Protect security service should flag any potentially harmful app. However, users have become accustomed to ignoring such warnings, so they are not foolproof. Additionally, attackers have successfully introduced malware via the Google Play Store. Typically, this involves a ‘Dropper,’ an initially innocuous app that fetches the malicious payload once installed. This method bypasses warnings from both the operating system and Google Play Protect.
MDM compliance policies may disable sideloading of apps and restrict which apps can be downloaded to work profiles. However, enforcing these policies comprehensively in the real world is challenging. They offer no protection for the large proportion of accesses originating from BYOD (Bring Your Own Device).
Privilege Escalation
The security architectures of both Android and iOS are significantly better than Windows, with strengths in sandboxing, encryption, and app store distribution. However, attackers have found one devastating vulnerability in Android: the Accessibility Service.
Designed to make devices more usable for people with disabilities, the Accessibility Service is a core part of Android, so its use by an app might not raise suspicion. Apps granted accessibility access have extensive permissions to interact with the device, making it difficult to distinguish between legitimate and malicious use. Attackers rely on tricking users into granting accessibility access, making it seem like a necessary step to use an app’s features. However, its powerful capabilities are a boon for attackers:
Capturing Screen Content and User Input:
- Keylogging: Malware with accessibility access can monitor and record every keystroke, including passwords, credit card numbers, and other sensitive information.
- Screen Recording/Screenshots: The malware can capture what’s displayed on the screen, revealing personal data or login credentials.
- Overlay Attacks: Malware can create fake overlays that mimic legitimate app screens, tricking users into entering credentials into the malicious overlay instead of the real app.
Performing Actions on Behalf of the User:
- Clicking Buttons and Links: Malware can automatically click buttons or links, leading to unintended actions like downloading additional malware or making fraudulent transactions.
- Filling Forms: The malware can fill in forms with stolen data or malicious content.
- Sending Messages: It can send SMS messages to the victim’s contacts, spreading the malware or sending phishing messages.
Bypassing Security Measures:
- Granting Permissions: Malware can abuse the Accessibility Service to grant itself additional permissions, such as access to contacts, call logs, or SMS messages.
- Disabling Security: It can disable security features like Google Play Protect, making it harder to detect and remove.
Data Collection
Once a RAT is installed, attackers can steal sensitive data from cloud applications, collect credentials, and respond to MFA challenges while accessing the enterprise network from an attacker-controlled device. They can also communicate with colleagues as part of a Business Email Compromise attack. Essentially, the attacker inherits all the privileges of the employee whose phone they have subverted.
Attackers’ tactics continue to evolve. The recently discovered BingoMod RAT can remove security apps and wipe the device once its mission is achieved. Earlier RATs developed extensive sandbox evasion and anti-analysis techniques. GuardZoo is spyware distributed via WhatsApp designed to exfiltrate photos, documents, location data, and device configuration information. CapraTube collected and sent SMS messages and calls while capturing screens and modifying files. The list goes on.
Conclusion
Android RATs are among the most devastating attacks observed. They are particularly dangerous due to their relative lack of technical sophistication. Unlike commercial spyware like Pegasus and Predator, they don’t rely on expensive zero-day exploits but instead use classic social engineering techniques. They are also relatively easy to defend against with the right tools. Ultimately, they exploit the complacency many organizations exhibit around mobile endpoint security.




