The Hidden Security Risks of AdInt
Data produced as a byproduct of the online advertising industry presents a significant risk to enterprise security. Every day, online advertising networks run by companies such as Google, Microsoft and Meta broadcast employee and organizational data to thousands of third parties worldwide. The ease with which malign actors can access this highly sensitive information makes it not only a privacy concern but also a serious corporate and national security threat.
The online advertising ecosystem systematically leaks location, behavioral, and contextual data at a scale and granularity that makes it trivial to identify specific individuals – including those most likely to be targeted by nation-state adversaries or criminal groups.
Background: Real-Time Bidding
Real Time Bidding (RTB) underpins most digital advertising today. Each time a user visits a website or opens an app containing programmatic ads, an automated auction takes place – typically in less than a second:
- Supply-side platforms (SSPs) which are embedded within most websites send a bid request containing metadata about the user and their device.
- That request is distributed via one or more ad exchanges to hundreds or even thousands of demand-side platforms (DSPs).
- Each DSP uses this data to decide whether to bid – and even if it doesn’t win, it typically retains the information, adding it to ever-growing “dossiers” about individual users.
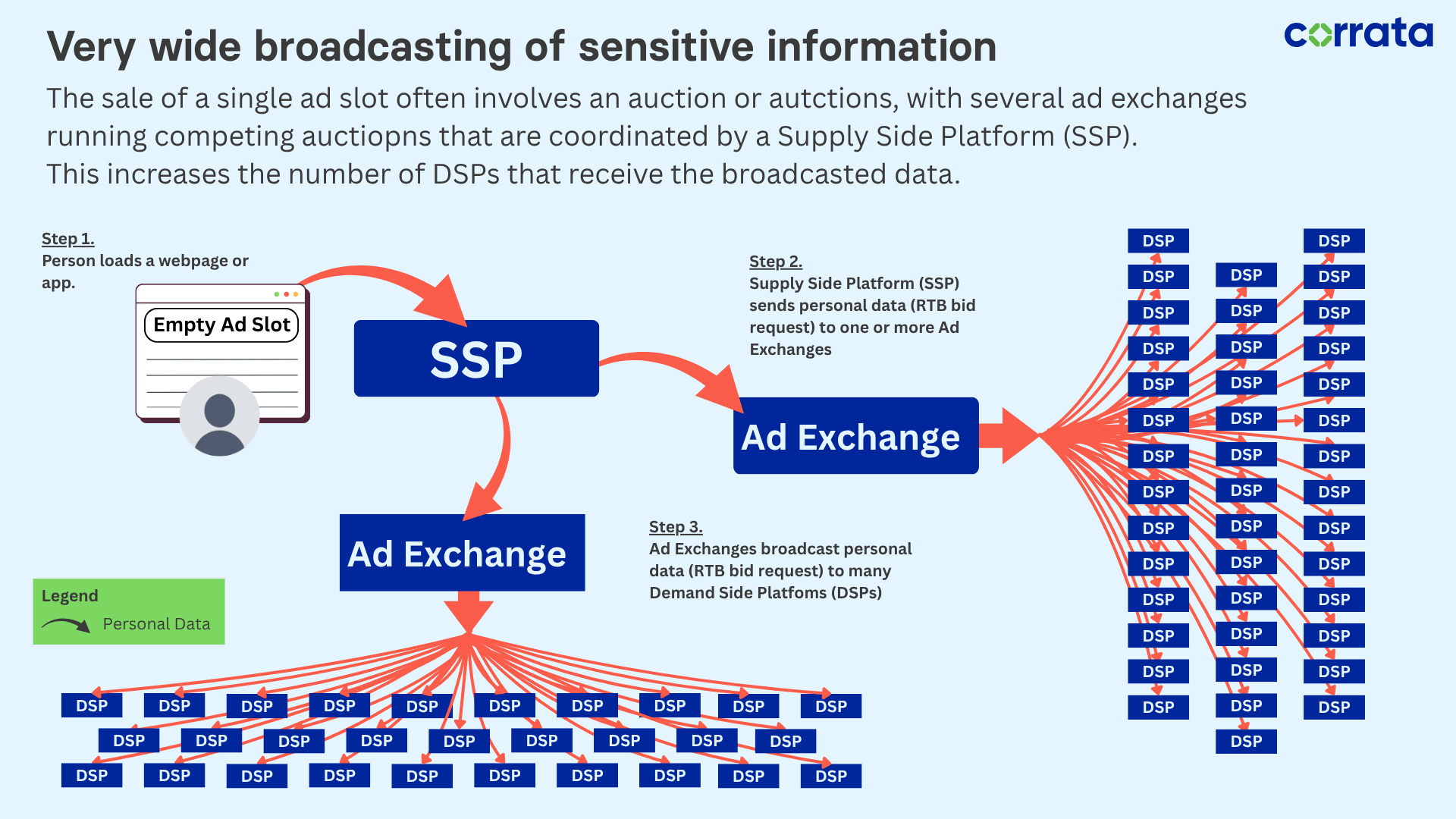
Image: Flow of personal data through the online advertising ecosystem.
The scale of these broadcasts is difficult to overstate. According to a 2023 report by the Irish Council for Civil Liberties (ICCL):
- Google’s RTB system in Europe shares data with up to 1,102 companies. In the United States this number rises to 2,015
- Microsoft’s Xandr platform shares with 1,647 firms.
- Across the EEA and UK, 71 trillion RTB broadcasts of personal data occur every year (excluding Amazon and Meta). The equivalent figure for the US is 107 trillion.
These bid requests routinely include precise or derived location, IP address, device identifiers, browsing context, and timestamps – none of which are subject to post-broadcast control.
From Advertising Data to AdInt
This constant flow of personal data has become a valuable resource for the commercial surveillance industry.
- The Israeli firm Rayzone Group operates a DSP that powers its Echo surveillance tool, reportedly used for mass collection of online user data.
- Another Israeli company, ISA Security, markets Patternz, a platform it claims enables national security agencies to use “real-time and historical user advertising-generated data” to detect threats.
This emerging discipline – referred to as Advertising Intelligence (AdInt) – has already proven useful to law enforcement, assisting in investigations such as child abductions and hijackings. However, the same data, when accessed by hostile actors, can be weaponised for targeting, coercion, or espionage.
Nature of the Risk: A Global, Uncontrolled Data Broadcast
For enterprises, AdInt represents an unbounded data leakage channel. Each transaction can expose:
- Device and network metadata, which can be used to fingerprint corporate endpoints.
- Employee location data, including workplace, home, and travel routes.
- Inferred behavioral and psychological characteristics.
Actors with malicious intent can easily acquire this data – by creating front entities that appear to be legitimate participants in the ad ecosystem, or by purchasing information from existing data brokers and exchanges.
Because the RTB system has no technical enforcement mechanisms, once data is broadcast, it can be re-shared indefinitely. The result is a global, uncontrolled data shadow of corporate and personal activity.
Such data allows adversaries to map personnel networks, routines, and associations, or even target family members for social engineering or surveillance.
RTB feeds often contain precise location data, revealing:
- The coordinates of secure facilities, including military installations, one dataset identified individuals located within six miles of a base.
- Patterns of travel between home and sensitive workplaces, allowing adversaries to infer organizational structures or project activity.
In addition, RTB data can include inferred psychological and financial information, such as:
- Debt, bankruptcy, gambling, alcohol use, or mental health conditions.
- Sexual orientation and relationship status, derived from app usage or browsing activity.
For employees in sensitive sectors or roles – defense, energy, healthcare, government, or critical infrastructure – this data is a potential goldmine for adversaries. It offers insights into financial stress, health issues, and personal relationships that could be exploited for blackmail, recruitment, or coercion.
In some cases, it can also create physical risk by enabling real-world tracking and covert surveillance.
Reducing Exposure
While the RTB system operates largely outside traditional security controls, organizations can take concrete steps to limit exposure:
- Block access to supply-side platforms and ad exchanges using endpoint content filtering. This simple measure cuts off the root source of data leakage.
- Apply these protections to mobile devices, which provide the RTB ecosystem with especially detailed insights into user location and movement.
- Educate employees, particularly executives, field workers, and technical specialists, about the risks of RTB-based tracking and the importance of using corporate-secured browsers and networks.
The combination of an employee’s home and work location is often enough to uniquely identify them. Preventing this information from entering the RTB ecosystem should be treated as a core element of enterprise data protection.
In Closing
Real-Time Bidding was built to optimize ad delivery, not to protect privacy or security. But in its current form, it has evolved into a global telemetry system that leaks sensitive personal and organizational data at industrial scale.
For adversaries, AdInt provides a low-cost, high-fidelity means of tracking, profiling, and targeting key individuals. For enterprises, this translates into a new category of operational risk – an exposure which can no longer be ignored.



