QR code security risks: innocent scan or malicious scam?

The recent news that QR codes had been used in a large-scale phishing attack against a major US energy company is a reminder that cyber criminals are constantly searching for new ways to trick end-users into falling for their scams. It’s also a reminder of the particular risks associated with QR codes. In this blog, we take a step back to explore how QR codes work, the security concerns around them and how to mitigate against the potential risks.
What are QR codes?
Quick Response (QR) codes are two dimensional barcodes that provide instant access to online information when scanned. While they may seem like a relatively new technology, QR codes were actually created in 1994 in Japan by Chief Engineer Masahiro Hara of manufacturing company Denso Wave.
The QR Code System became an instant hit in China in the late twentieth century. The COVID pandemic was the trigger for an explosion in their popularity throughout the world. In a global effort to stop the spread of the virus, QR codes were deemed the “most effective system for COVID-19 tracing.”
However, the uses of this technology extend far beyond tracking social movements. They can be used to pay for goods and services, rent city bikes, direct consumers to a company’s Facebook page, apply to a job advert… the possibilities are endless.
How do QR codes work?
QR codes function in much the same way as traditional barcodes by displaying specific information when they are scanned. However, QR codes are most commonly used to direct smartphone and tablet users to a particular URL.
Visually, the codes are made up of black and white squares designed to encode different characters of text. Their ability to read code in both the transverse and longitudinal directions allows them to encode over one hundred times more data than regular barcodes. The larger the image size, the more characters the code contains. The three larger corner squares help align the code, allowing it to be easily scanned from any orientation.

What are their advantages?
The main advantage of QR codes is their ability to read information at incredibly high speeds. For example, imagine walking by a billboard and seeing an eye-catching advert. Instead of wasting time typing the website URL into your smartphone, a quick scan of the QR code loads the desired web page instantly.

Or, imagine you are at an industry trade show and want to sign up to a company’s newsletter. By scanning the stall’s QR code you are brought straight to the landing page.
An advantage for business owners is that QR codes are easy and free to create with step-by-step tutorials available on YouTube. Once created online, they can be printed off and placed on everything from restaurant tables and shop windows to business cards and flyers.
Originally we tended to encounter QR codes in the physical world. Increasingly however, they are appearing on our computer screens as a way of linking web and mobile applications. The most well-known example of this is the mechanism used to enable WhatsApp access on desktops.
Are there security risks?
Just like with any technology, QR codes come with potential security risks. By default, they are not automatically encrypted. This allows cyber criminals to easily tamper with them by placing stickers on top of the original. When the sticker is scanned, the user is unknowingly redirected to a malicious phishing site designed to steal their credentials.
The added danger is that there is no easy way of predetermining where a code leads to/what URL it will open. As a result, the user has to blindly trust that the code leads to a safe domain. With no humanly readable elements, it is extremely difficult to differentiate a legitimate code from a fake.
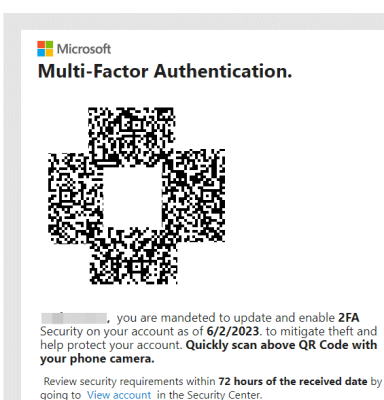
Example of QR code used in phishing attack against major US energy company, Source: Codefense
The use of screen-based QR codes has opened up a new avenue for cybercriminals. QR codes can now be distributed digitally via email or messaging applications. In the case of the recent attack against a major US energy company, the QR codes were included in an email sent to employees. The phishing emails contained an embedded QR code which redirected to fake Microsoft account credential pages. The call to actions were around updating of accounts, information related to 2FA, MFA or general account security.
How can you protect yourself against fake QR Codes?
Most modern smartphones will not automatically redirect to the site embedded within the QR code but will give the user the opportunity to review the destination URL. Be vigilant by inspecting the destination URL. Exercise the same caution you would upon receiving a suspicious-looking email or SMS. If in doubt, search the subject line through your browser instead. Trust your instinct – if the landing site looks suspicious, do not enter your personal details or credit card information.
From the cybercriminals’ perspective, one of the attractive features of using QR codes within an attack is that many employee smartphones still lack anti-phishing protection. As a result, in contrast to a standard phishing attack, the malicious link in QR based attacks will not be blocked by web-filtering controls.
We decided to show just how easy it is to fall for fake QR codes. In the video below, the user is unknowingly brought to a phishing site which looks extremely convincing. However, upon closer inspection, the URL is different to the official eBay website.
When Corrata is switched on, the user is now unable to reach the phishing site and is informed that a security threat has been detected. Corrata sends the URL anonymously to our threat engine for examination, which tells the phone whether to allow or block, and does this all in milliseconds.




