Landfall: Detecting Spyware in the Wild

In late 2025, Unit 42 published an in-depth analysis of a novel Android-focused spyware family, dubbed LANDFALL. (Unit 42) This malware is of special concern because it leverages a previously undocumented exploit chain for delivery, then downloads follow-on payloads, and ultimately conducts broad data exfiltration. In this blog we’ll unpack how the infection takes place, how the malware subsequently behaves, and why monitoring device network communications is essential to detecting this type of threat.
How infection begins: the crafted image file
The attack vector in LANDFALL is elegant and insidious. According to Unit 42, the campaign starts with a maliciously constructed image file – specifically, in the DNG (Digital Negative) format. (Unit 42) These DNG files appear to be benign image files (for instance, with filenames like “WhatsApp Image 2025-02-10 at 4.54.17 PM.jpeg”) but in fact contain a hidden ZIP archive appended at the end of the image data.
In principle, this would be ignored. But the key is that the image-processing library of targeted Android devices (in this case certain Samsung Galaxy models) contains an arbitrary code execution zero-day vulnerability (CVE-2025-21042) in the part that handles DNG decoding (libimagecodec.quram.so). When the crafted image is processed – for example when viewed or handled via a messaging app – the vulnerability unpacks the appended ZIP archive and executes its code on the device.
In sum: malicious image file → exploit of image-processing library vulnerability → embedded payload extraction and execution.
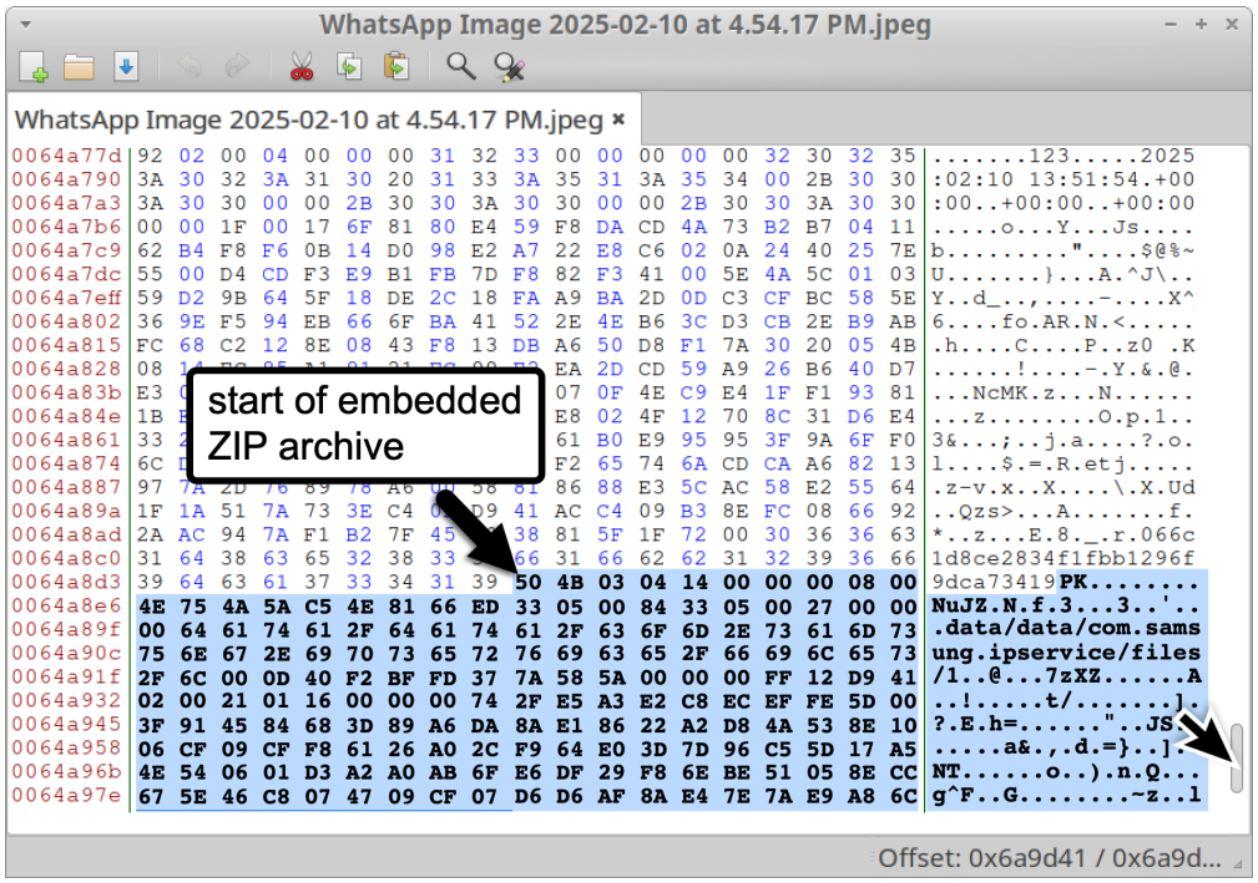
Example of a malformed DNG image with an embedded ZIP archive (Source: Unit42)
Downloading further software & data exfiltration
Once the exploit succeeds and the loader component is active, it serves as a staging point to download additional modules and carry out extensive spying. LANDFALL’s design is modular: the loader initiates the chain, then further payloads expand its capabilities. For instance the loader may extract and execute a SELinux-policy manipulator component (l.so) which allows the spyware to modify system security controls for persistence and privilege escalation.
Once active, the spyware is capable of fingerprinting the device (OS version, hardware IDs such as IMEI/IMSI, SIM card serial, installed apps, location services, etc) and then performing data collection and exfiltration. The types of data exfiltrated include:
- microphone recordings
- call recording and call history
- contacts database
- SMS/messaging contents
- camera photos
- arbitrary files and device databases (browsing history, etc)
From a defender’s perspective, this means that the initial image exploit is only the beginning – once the payload is in place, it reaches deep into the device’s data and functions.
Command & Control (C2) communications: the tell-tale sign
Obviously, LANDFALL maintains a back-channel with its command-and-control infrastructure. The loader component engages in HTTPS communications with C2 servers, but , interestingly, uses non-standard TCP ports. Unit 42 identified several hard-coded C2 servers (IP addresses and domains) used by LANDFALL. For example: 194.76.224[.]127 (brightvideodesigns[.]com), 91.132.92[.]35 (hotelsitereview[.]com) among others. Because of this, one of the strongest indicators of a LANDFALL infection (or similar spyware) is anomalous network traffic from a mobile device – especially involving HTTPS connections to unexpected domains or IPs using non-standard ports.
Why monitoring for this communication is essential
On modern mobile operating systems, mechanisms that ensure strong process isolation and limited visibility prevent third party apps from monitoring system or other app processes. When combined with the stealthy nature of the image-based exploit and the deep device-level access of the payload, detection via traditional endpoint antivirus or app-scan mechanisms is impossible. The exploit may bypass user interaction and the payload may run under the cover of legitimate processes. In this context, searching for anomalous network behaviour becomes one of the most reliable defence modalities. Defenders should:
- Track devices for unusual domains and IPs associated with spy-tool infrastructure (such as the hard-coded C2 addresses in the report).
- Monitor mobile devices for outbound HTTPS connections on unexpected ports (i.e., not typical 443 or 80), especially to IPs or domains that are not part of normal app-ecosystem behaviour.
- Establish baseline network-behaviour profiles per device: for example, domain sets used by messaging apps, OS updates, app-store calls; then highlight deviations (new domain, large data volume upload, odd port usage).
- Implement mobile-device network filtering or proxy-ing that can flag or block unknown high-risk outbound flows.
Implications for mobile security and your environment
For organisations concerned with high-value mobile-device protection the LANDFALL case underscores several important points:
- The attack vector is non-traditional: it abuses the image-processing path rather than requiring a malicious app install or user-clicked link. This means mobile-device management (MDM) and app-whitelisting offers no defense.
- Post-exploit, the malware is highly capable: deep access, elevated privileges via SELinux policy manipulation, and full-scale data exfiltration.
- Network‐level detection is critical. Given the modular payload and covert communications, network monitoring becomes a key line of defence.
In Closing
The mechanisms we observe in the LANDFALL campaign have been used repeatedly in advanced spyware attacks . By exploiting an image-processing vulnerability (CVE-2025-21042) via a seemingly harmless image file, the attackers bypass traditional controls, inject a loader, download further modules, and then communicate over non-standard ports to exfiltrate data.
Detecting the network communications is one of the most practical and potent detection strategies. For any organisation with sensitive mobile endpoints, especially in sectors targeted by advanced adversaries – ensuring that your devices are monitored for atypical outbound flows, unknown domains/IPs and unusual port usage is not optional: it is essential.


